Introduction
Satcoms are the game changer in maritime cyber security. In the past, satellite connectivity was so expensive as to be prohibitive for all but the most essential communication. Crew personal email and social media access was a pipe dream.
However, now that ship operators have access to data plans and significant bandwidth is more affordable, always-on connections can be a valuable recruiting tool and enable the concept of the smart ship.
‘Always-on’ can be the downfall of a vessel if its cyber security is not addressed. From being an isolated (and therefore more secure) environment when at sea, a ship is now just as connected as many offices. Yet, cyber security is usually an afterthought, if it’s even considered at all.
Basic satellite equipment checks
My advice to operators is to check the following in your satcoms equipment:
- Administration passwords
- Access from the public internet
- Terminal software version
- Physical security of the terminal
- Check that the satcom system has its passwords changed from the manufacturer default
By far the most common problem: the satellite terminal installer hasn’t changed the administration passwords from the default admin/admin, admin/1234 or similar. Ensure the passwords are complex and only known by those who need to know.
A hacker could easily access the terminal administration interface, use a default password and then take control of the satellite terminal. They may also be able to then access more critical networks on the vessel
For example, if the password is default, a hacker can easily downgrade the software and introduce security flaws. Here’s an example of a downgrade attack in a Cobham terminal. Even if the password was then changed, the hacker would still have access!
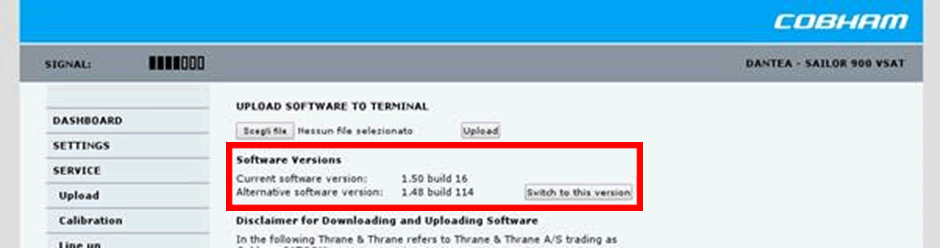
Ask if anyone on the crew knows the admin password. If not, who does know it?
Is it written down anywhere? It is often written on a note physically stuck to the terminal! Here are some examples of passwords stuck to computer systems found on vessels:

Review the password if it is supplied to you. Is it at least 10 characters long, does it have uppercase, lowercase, numbers and non-alphanumeric (e.g. !”£$%^ etc) content. However, “Password1!” would not be acceptable.
Is the password ever changed? If so, how often? Once per year would be reasonable, as well as when key personnel leave.
How is the terminal administrated? Does anyone on the crew know how to fix bugs with it, if it failed at sea?
Make sure the satcom system isn’t available from the public internet
Terminals should NOT be available on the public internet. If they are, an attacker anywhere in the world can connect to the terminal and attempt to compromise it
Most satellite airtime providers offer a private IP address space, so hackers can’t reach your satcom system as easily over the internet. Many operators will have a VPN in place so that only the IT staff from HQ can access the terminal.
How to check to see if vessel satcom terminals are on the public internet or not
Connect your laptop or smartphone to the crew Wi-Fi network. Using a browser search using Google for ‘whats my ip’ and you should get a result something like this:
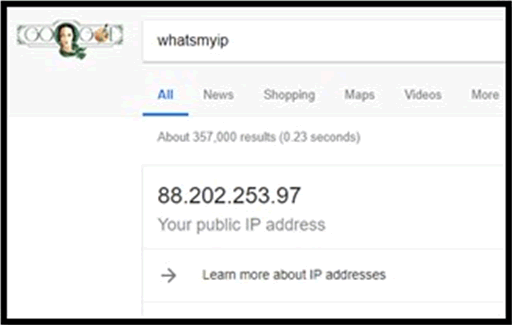
Copy and paste that IP address you see in to a web browser address bar, e.g.
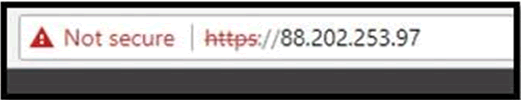
If you see a page that displays a satellite terminal interface you need to take action ASAP. It is likely that the terminal is available to all on the public internet, a bad idea. Speak to the airtime provider to get it reconfigured, correctly, again ASAP.
On the other hand, if the web page does not load or a generic error message is displayed, it is likely that the operator or airtime provider has correctly protected access to the terminal from the public internet.
Whilst this method isn’t foolproof, it is a simple route to check if your terminals are on the public internet. If you have any doubt, speak to a network engineer.
This is still not a guarantee of security; a hacker that had successfully compromised the operator’s HQ network may still be able to access the terminal, but the risk is much reduced.
Is the software running on the satcom system kept up to date?
Keep terminal software patching up to date. No excuses. Terminals need to be running the latest version and you need to ensure that updates are made every time the manufacturer publishes an update. Updates usually include fixes for security flaws, so the more out of date the software is, the more vulnerable it is.
If out of date software is present, a hacker may be able to bypass the login and access the terminal even if the passwords are of a high quality.
Keep a record of who is responsible for updating the satellite terminal software.
Keep a written log of when the software was last updated.
Check the software version of software, often shown on the web interface of the satcom terminal.
For example:
Cobham Sailor 900
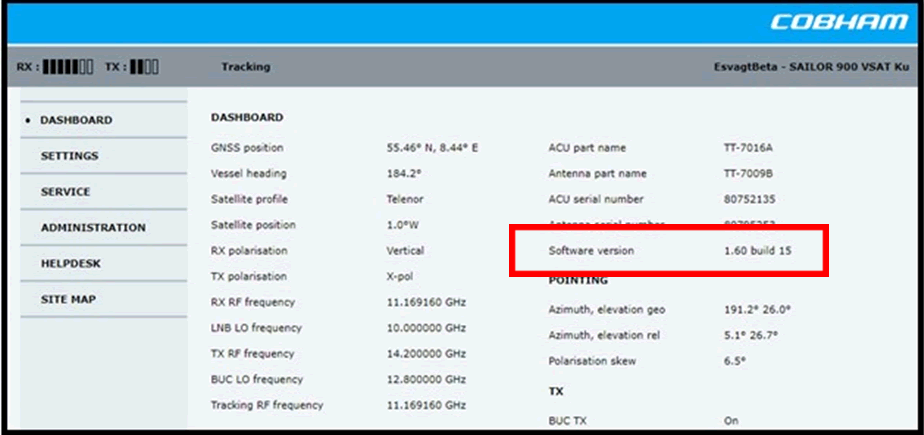
Manufacturer support pages often change, but currently the relevant page on the Cobham web site is here: https://sync.cobham.com/satcom/support/downloads/?type=2502&article=7399
From this, one can see that the current version of software 1.60 Build 15, which means the software in the Cobham image above was current at the time of writing.
Use a search engine to find the vendors current software update pages, or navigate through the vendors web site looking for the update pages.
It’s good practice to keep an audit trail for the procedure used for monitoring for updates and subsequent installation of upgraded software. It contain at least the following:
- A process for evaluating the importance of the update from a cyber security perspective
- A timeline for deploying the update
- Consideration of risks involved in deploying the update (will it affect a ship at sea, for example)
- A ‘staging’ area where the update can be tested and evaluated in a non-marine environment. This will probably be a test terminal on shore.
- A mitigation strategy if it is determined that the update will NOT be applied for a period of time for valid reasons
Physical security of the satellite terminal
Know where the below-deck satellite terminal equipment is located on all your vessels. This should be located in a locked cabinet to which only authorised, senior personnel have access.
Sure, the risk of a direct physical attack to a terminal is much lower than one exposed on the public internet, but its still important to secure it. Ensure that the terminal is locked away from inquisitive crew or you might find that those who have used their data allowance might try to find ways to get more!
Ongoing risk management in terminal equipment
After a ‘spot’ audit, one needs assurance that the terminals were not simply secured as a one-off. Ongoing management of their security is imperative, or security will relapse over time, so you have a regular review process in place.
How do you check if new terminal software is available?
The terminal manufacturer will publish new software from time to time. Software updates may include functionality improvement and bugfixes, however most importantly they usually include security patches.
The manufacturer may have an email alert system when new updates are published. Do you have a process for checking for new software updates. Have you checked that your process actually works effectively?
It’s also important to review what the software update fixes: Is there a critical flaw, such as an admin account login bypass that could expose the operators vessels, or can the update be safely deferred until the next maintenance opportunity?
Applying updates to satellite terminals
If a critical update needs to be applied whilst the vessel is at sea or in port with limited IT support, do you have a process for carrying out the update and backing out if it goes wrong?
Updates can be carried out either ‘over the air’ using the terminal equipment itself or via USB.
Updates usually complete without incident, however there are occasions where they fail. Do you have a detailed update process, particularly one that caters for failed updates?
Consider what would happen if an update failed whilst at sea: operators and crew have become increasingly used to having always-on connectivity. If the satcom terminal is now effectively a non-operational ‘brick’ through a failed update, are the crew fully capable of bringing the vessel to shore with no data connectivity? Bear in mind that the satphone is unlikely to work either.
Don’t forget the communications requirements of the cargo and vessel systems also; telemetry, engine management, reefer management and plenty of other systems require satellite data in order to operate efficiently. Losses may emerge from unexpected directions, even though the crew are perfectly capable of managing the vessel.
Once in range of ship-shore VHF (and mobile data when closer to land), connectivity is re-established, but crews and operators may find the temporary data communications ‘black hole’ unsettling.
Your update process should include assessing the risk of a ‘bricking’ event. Some terminals can recover themselves from a failed update, but may need the intervention of a tech-savvy crew member to restart the device and select an older software image. It is a good idea to have a named, trained person on board at all times to administrate the terminal. Remember, remote assistance is not available, as the satellite terminal is offline.














