Blockchain is a subject I have been quite interested in for a few years now and I do believe it has a future in a lot of the world, security included. I’ll give a brief overview of what it is in case you are unaware.
Blockchain technology is essentially a distributed digital ledger which records transactions made in the cryptocurrency related to the chain, for example Bitcoin or Ethereum both have Blockchains. Everyone using the Blockchain has a copy of its ledger and provides it to the network, which means if one user drops off, the ledger still exists, therefore it is not centralised like a database in a business might be. The ledger is chronologically ordered in blocks of data, which get created on each transaction. Blockchain prides itself on being public for anyone to view therefore is auditable.
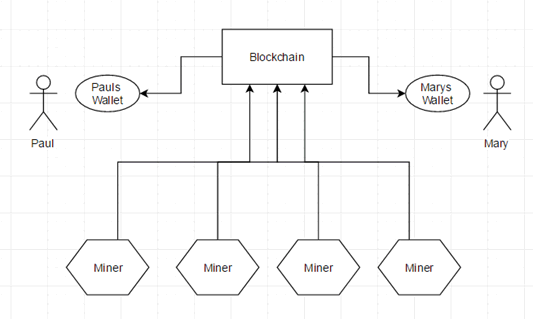
Looking at the diagram above we have a Blockchain which anybody could query to see its blocks. Blocks hold transaction information such as sender, receiver, amount sent and extra bits also stored, such as a text snippet. Anyone could also see the currency available in any wallets. Miners are the security of the Blockchain and each miner has a copy of the ledger which is ever updating with every transaction. Security comes from the amount of users on the network able to provide this ledger.
So when you think about that, there is one main attack vector to break Blockchain security, that is with a 51% attack which involves an attacker owning 51% of all nodes (Miners) on the network. Therefore, forming a majority vote that the rogue Blockchain is the correct one.
Going back to the diagram, if Paul wants to send currency to Mary, the transaction will go via the Blockchain and its miners, who all check if the wallet attempting to send currency has enough coin to do so. It also checks if Paul owns the coins and hasn’t already spent it elsewhere (known as double spending). Each Blockchain transaction block has a hash which the miners must solve in order for the block to be added to the chain. This is called ‘Proof of Work’ and is the proof that the transaction actually occurred. The benefit for a miner to prove the transactions is the reward of currency.
…and that is the basics of Blockchain technology. You have a database, you have many people with said database and you have miners who prove transactions before they go into the database.
The benefits of these are:
- The Blockchain cannot be changed
- If a rogue user tries to change the ledger the miners will disallow the change.
- No central point of failure
- The more miners the more nodes need to be taken down to kill the network.
- Auditable
- A traceable log of all transactions shows everything happening
So now we know this, how can crypto currency transactions be applied in a security context?
Authentication
An example of an authentication mechanism made using the Blockchain could be the example below which eliminates the common user/pass combination and implements the more secure public/private key pair solution.
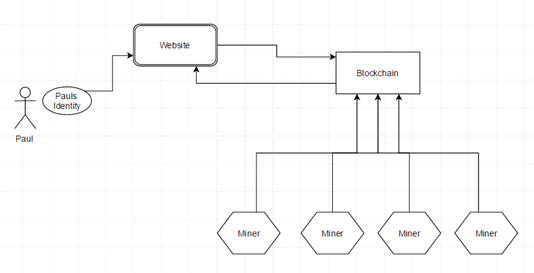
It would be possible to remove the need for a username and password and instead give the user an Identity which would essentially be a public/private key pair. Firstly, the user would sign up for their identity using an application which could be a Windows or Mobile application, for example. This application would then give the user a long passphrase only once, to be used in the case that the user needs to revoke access to their account. This identity, which would be the user’s public key, is then stored in the Blockchain inside a transaction block.
When a user attempts to login to a website, the website would query the Blockchain for the users’ public key block and compare it with the private key that the user is presenting via the Windows/Mobile application, thus logging them in if they match.
If the Identity (private key) was to be compromised, the user could use the long password given on sign up to create a new private key and create a new public key block in the Blockchain, which would be queried by websites on next sign in.
“IoTchain”
An interesting example of Blockchain security might be securing a business network of IoT gear from a rogue attacker trying to turn off the lightbulbs, blow the kettle up and burn your toast. Because let’s face it, as IoT comes into the world, they will have their own subnets that need securing.
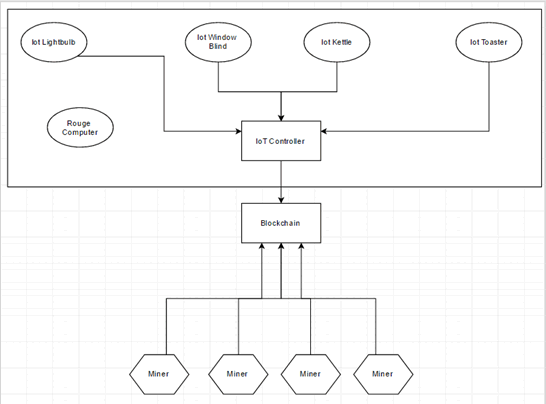
Let’s say we have an Internet of Things controller that creates a network of IoT gear in a business. Each of these IoT devices will have a private key with their public key set into the Blockchain. The IoT controller will constantly query the Blockchain for which IoT devices should be on the network.
Let’s now say a rogue attacker gets into the IoT network via Wi-Fi or an Ethernet port. The reason IoTchain could work is because the attackers machine will not have a public/private key pair in the Blockchain, therefore the IoT controller would block the connection from the attacker’s computer. I suppose this is sort of like blocking MAC addresses on a switch, but this is actually effective. Try spoofing a private key…
How could an attacker potentially circumvent the Blockchain security here? The 51% attack as mentioned earlier. This would mean the attacker has to compromise 51% of the miner nodes or add enough nodes to the mining network in order to add the attacker computer key into the Blockchain.
This is possibly too much work for an attacker?
With more thinking, the IoT devices in the diagram could actually be the miners which would require a lot less resources to run the Blockchain network.
The future
I do believe the future is very bright for Blockchain, especially in the IoT market. But actually, there probably is not a market where Blockchain couldn’t fit in somehow. Maybe I am biased as there are other solutions out there such as the Blockchain rival “Closed Group Consensus” which is also used for crypto currency such as “MaidSafe”. But that’s for another blog!














