The ‘Secure by Design’ guidance for consumer IoT security from the UK’s Department for Digital, Culture, Media and Sport (DCMS) is coming shortly. In the meantime we’ve seen SB-327 from California legislators, mandating some basic security standards for consumer smart tech.
Both are big steps forward, though take very different approaches.
SB-327
This is mandatory regulation to protect Californians, though it’s not effective until 1st Jan 2020.
It’s quite a vague bill, but I think that’s actually a good thing as the consumer smart stuff market covers many categories of product. However, it will require much testing in law. What is ‘appropriate security’?
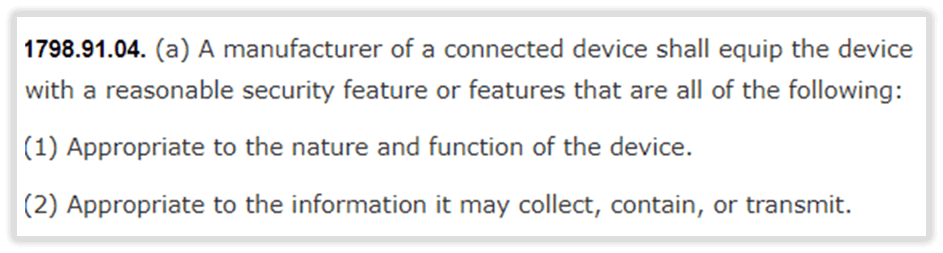
If appropriate is not defined, then there is plenty of wriggle room for manufacturers.
‘Designed to protect’ is also an interesting point:
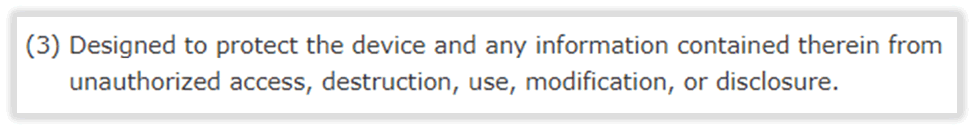
We’ve tested hundreds of smart products that were designed to protect, yet no-one had checked that the ‘design’ worked as intended!
A little more clarity around this point would definitely help implementation.
Mandatory unique device passwords will be a big step forwards, as many smart products are left in default configuration by the consumer, opening them to trivial tampering:
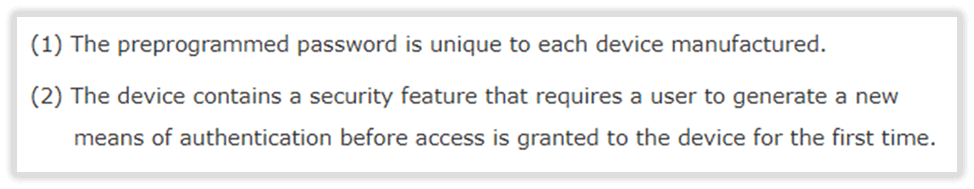
There’s an issue here though: a password can be unique, yet it can also be sequential and weak!
I can see that the intention of the regulation is to have a strong, unique password generated from a good entropy source on the smart device, but lawyers will act on the wording of the Bill.
If we leave wriggle room for manufacturers, legal cases are likely to fail. Consumers will lose out.
Channel stuffing?
Finally, is there a perverse incentive for manufacturers to stuff the retail channel with insecure product on the run up to 2020?

If there is no duty by the retailer, then what has the manufacturer got to lose? That area may need clarification!
There is also no detail of updates to smart product to ensure it stays secure. For the future perhaps?
DCMS ‘Secure by Design’ Code of Practice
This takes a very different tack. Whilst the final guidance hasn’t yet been launched, the initial report contains proposed standards and advises on good practice.
It’s much more detailed and gives guidance to manufacturers, mobile app developers, service providers and retailers.
Despite not being mandatory, there is a backstop of perhaps the best consumer privacy regulation in the world: GDPR.
It also has the benefit of addressing a much wider segment of the IoT supply chain and marketplace. By influencing retailers and then consumers, buying behaviour can be changed so that the public are more likely to purchase secured smart devices.
There are some aspects in common with SB-327 such as:
No default passwords
Securely store credentials and security-sensitive data
These make a lot of sense, as they’re very common issues that we find
But perhaps my favourites from the DCMS guidance are:
Keep software updated
And
Implement a vulnerability disclosure policy
- Music to the ears of security researchers who continually struggle to get errant IoT vendors to pay attention!
My regulatory wish list
- I would like to see fresh primary legislation in the IoT arena in the UK, but this will take time. It would also be reasonable to let the DCMS guidance ‘bed in’ with manufacturers. If they don’t start to change behaviour, then that would be the time for regulation.
- Giving consumers the right to return vulnerable smart products for credit will create financial incentives for manufacturers to get security sorted
- Retailers committing not to stock vulnerable smart tech, backed up by trading standards legislation
- Manufacturers delivering product security updates for the foreseeable life of the product
Conclusion
There are plenty of other IoT security standards out there being worked on, but these two present completely different approaches to the problem, though I suspect with similar results over time.














