While home working might now be the norm for some, more and more people are going back to their place of work on a more regular basis.
If you’re commuting again or if you’re responsible for securing your people’s devices it’s a good idea to revisit and review your security admin for mobile devices. This post isn’t breaking any new ground, but it is a good place to start that review process, and think about your security behaviours.
TL;DR
- Passcodes need to be present, ideally with a lock out duration of more than 60 seconds. That passcode should have a minimum of 8 digits
- Updates fix security issues, so install them
- Consider a MDM for business devices to allow for remote wiping, application allow-listing, installation of applications and device lockdowns
- Consider pushing profiles for connections to known good Wi-Fi networks. Favour cellular data elsewhere, unless roaming charges will be a major issue
- Consumers might consider a VPN to secure communications on untrusted Wi-Fi connections, though there is debate about the benefits of consumer VPNs for mobile devices
- Physically secure devices through the use of privacy screens
Hackers don’t restrict themselves to attacking our desktops or laptops, so we need to up our game.
I guess you’ve considered the security of your mobile device itself, but what about its content? What about if it’s a company device?
Here are some security tips that will help you ensure that both the devices and their data are protected too.
Use strong passwords / biometrics
Strong passwords should be the norm these days. The default requirement of an iPhone or android is a 6-digit number however there are options for 4-digit passcodes.
In some circumstances, this can be worked out in little under a day with the correct tools. Introducing a long numeric passcode of at least 8 digits will greatly hinder any attempts to break into a device. Better still, enforce fingerprint or FaceID-style authentication.
This is an oldie but a goldie from @matthew_d_green that shows the difference in cracking time for various complexities of passcode:
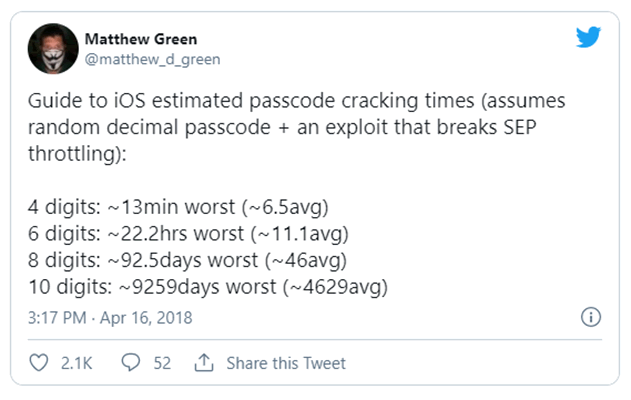
Also ensuring a timed screen lock is in place prevents unauthorised access to data if your phone happens to be stolen or misplaced.
Updates
Keeping your device and its applications up to date is paramount to ensure the latest bug fixes and security loopholes are mitigated. Out of date devices are susceptible to vulnerabilities that can lead to a breach in the confidentiality of the data it holds.
Implement an MDM or similar
Using a mobile device manager (MDM) allows remote management of corporate devices centrally ensuring that every device is running the same policies and protections. MDM’s can perform a variety of tasks from auto enrolment, application management and other security features.
Personal devices can benefit from careful configuration using, in the case of Apple devices, iCloud.
Backups
Backing up data in case a device must be wiped due to loss or theft is a simple way to ensure the user is back up and running in no time. It may, however, be worth considering where you’re backing the data up to and whether it is stored with a 3rd party. Dependant on the sensitivity of the data, considerations should be made for secure storage of any company data.
Again, for the personal user, it’s a good idea to keep data backed up in a cloud platform. Think carefully about the security of these though: a strong password that you don’t use elsewhere, plus multi factor authentication is very wise. Don’t forget to have some redundancy in that process though: if the only way to authenticate through MFA is through an app on your phone, you’re a bit stuffed if the phone has died or been stolen.
Remote wipe
The ability to remotely wipe a device that has been stolen is golden. Allowing for all content to be deleted, renders a device almost useless to an attacker. iPhones have the ability to allow for a full wipe after 10 failed passcode attempts but also, any good MDM will have this functionality available to deploy to end users.
Connecting to public Wi-Fi
It is always wise to have your Wi-Fi disabled when not in use and out in public. Not only does it eat your battery, but it prevents a malicious attacker from potentially spoofing access points that you have previously connected with. This can lead to compromise of passwords and data in some circumstances.
If using public Wi-Fi is necessary then encrypting all communications is a good idea. An MDM will perform this, as will a personal VPN
And remember, just because it’s called ‘Airport Wi-Fi’, doesn’t mean that the airport has anything to do with it
Screen privacy filter
It is worth investing in a privacy screen. They can prevent shoulder surfing attacks which require minimal skill and result in maximum damage.
User awareness
We’ve saved this one until last because many of the problems experienced with data loss from mobile devices are a result of user error, and in this case just a little knowledge can go a long way.
Educating and sharing good ideas, tips and tricks around mobile device security can really help.














