A while ago I saw a tweet that initially angered me for many reasons, but then I thought about it and wondered how much effort do companies put in to awareness and training. The tweet was:

Security awareness is overrated. You got to do it, but don’t expect users not clicking on phishing mails again.

You can see why as a security awareness trainer that I initially got angry, there is real value in awareness training and it does with the right messaging lead to a reduction of successful attacks against your organisation. Then there is the fact you have to do it, well you don’t have to do it, for many organisations there is no regulatory requirement to do any security awareness, however, many choose to because they see the value it brings to the organisation.
A second thought
Then I thought about it and I can see what the poster meant, commonly when we perform assessments against companies we make the recommendation that the business should perform some security awareness training. We hold it in high regard, but time and time again phishing is successful.
The recent Twitter hack shows this, the attackers used social engineering techniques to get credentials to an admin portal that Twitter used. Surely Twitter of all companies must run security awareness, according to LinkedIn there are over 740 people whose profile shows they have some degree of responsibility for security at Twitter, which is around 12% of staff involved in security! This vastly exceeds most businesses, most businesses have less than 5 people, so they get security at Twitter… yet they got hacked through a phishing attack.
So yes security awareness is overrated, staff will still click on phishing emails. However, does that mean we shouldn’t do it? That point the original poster got right, you do have to do it…but not for regulatory reasons.
Excessive access
The Twitter hack demonstrated another problem, too many staff had access to admin functions at Twitter. According to Twitter most of the staff had access to the admin panel that the attackers used to take over the accounts and send the scam tweets. This is something we see time and time again on red team assessments, the most common, staff with admin rights, its trivial to traverse domains when you encounter users with admin rights.
Often this excessive rights is a business need, even if its not administrative rights over the local workstation, but rights to make changes to line of business applications. Your staff will need some degree of privilege, however, they will also receive phishing emails. Do you really think the attackers sent just one phishing email to Twitter? It seems unlikely, surely they would have sent in many, yet they only succeeded in compromising one person.
That does suggest the security training at Twitter is effective, we may never know the detail behind this, but it is certainly a lesson. A Security aware culture is needed, it’s needed to help the 99% of your organisation get better at spotting attacks, even if you still find 1% of staff click on links. It is not a regulatory requirement… it is a good practice requirement. However, it’s important to recognise that this culture change should be part of a program of assessment, including reviewing access levels for all staff and a wider program of social engineering.
Widening the net
One area that needs much more investment is the social aspect of security testing. Most clients we work with have a large program of testing, including websites, infrastructure, API’s, hardware, etc. but don’t have budget or approval to test the security culture of staff. Many companies use bug bounties but most will exclude social engineering attacks.
This example is Twitter’ bounty posted on Hacker One, showing that social engineering exclusion:
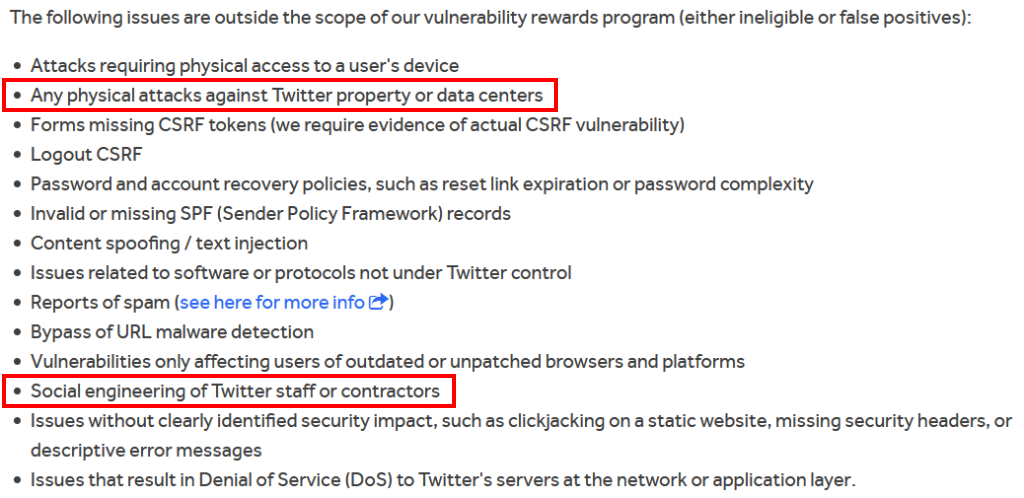
Note that physical attacks and social engineering attacks are out of scope. Now whilst I can understand that on a bug bounty program you may not want to have all and sundry on the internet trying to phish your staff or physically breach your office, but I certainly hope Twitter are performing these assessments internally.
Many clients are not, this needs to change, these days network level attacks against companies are harder to orchestrate as companies have ensured they patch issues and fix vulnerabilities through a program of testing and remediation. So where are attackers turning – your staff. Attackers are phishing staff or following them in to buildings, it is the easiest route in to your business. Are you testing for this? Are you giving your staff the tools to know how to spot this, how to raise it, how to prevent it? Does your business have a culture that promotes a positive security mindset?
Solving the problem
You need to fix your security culture problems in the same way you are fixing your network level problems, a program of testing and vulnerability management and remediation. So make sure your budget has money for social engineering attacks, both physical and logical. Then make sure you have budget to remediate those risks through adequate security awareness training. That training should look to address the security culture at the business, building the right security culture in your business is really hard, it takes time and it takes money, in the same way that it took time and money to implement a program of technical testing and remediation.
Changing culture is not a once a year tick box exercise, it needs continually improving. The recent ClubCISO security maturity report (requires signing-up) highlighted that 73% of CISOs see security culture as their number 1 hot topic.
Security awareness is something that can kick this off, but it is not the destination. Security awareness is certainly not overrated, it’s as valuable today as ever, but it needs to be part of a program of security culture change and improvement, like the rest of your security testing program… just don’t expect your staff to not still click on links. However, hopefully the culture you create will allow them to feel comfortable telling you about it.














