I get involved in a lot of IoT and ICS pen tests and found an interesting device on one of them. I didn’t have enough time on the job to go as deep as I wanted, so got PTP to buy a couple to play with. eBay FTW!
It’s an Ewon Flexy IoT Router.
It’s important to note that local access / public IP access is necessary in order to pwn the device. If users use Talk2M and change their default password, the risk is greatly mitigated.
This is the abbreviated version – if you want the full-on JTAG, locked bootloader, NAND flash dump, IDA, head-banging-against-the-wall, nearly-got-RCE-but-not-quite, Spidey-senses-a-tingling version, it’s here.
Anyway, here’s what it looks like. It’s used extensively in industrial control systems for securely communicating with remote devices in outstations over GSM/Wi-Fi/WAN/LAN. It offers ‘Secure VPN Connectivity’.

The vendor states >210,000 of these are out there. Plus about 3,500 on Shodan. Oops.

The default creds are adm/adm – I’ll bet a fair few haven’t been changed from default. This is a customer issue – what on earth are customers doing putting their industrial controllers on the internet?
Karn Ganeshen (@juushya) found some interesting vulnerabilities (XSS/CSRF etc) in the web interface a few years ago. The vendor got most of the bugs fixed, though it took a while.
I’m going in a different direction though. How about decrypting the master encryption key
Once authenticated to the web interface (maybe using XSS, the default creds or another way) I started looking at the VPN config:


Or you can just do a simple post request and grab the encrypted VPN Private Cert (remember you can get creds ?)

[“ptp”,”#_1_EHyXHCXlKSnkcW2f7kthnIg=”]
Hmm – Base64. Unfortunately, the decoded data wasn’t really anything of use.
But, if I can decrypt the data, can I decrypt the VPN Private Key too?
This is where things got a bit silly:
I started by adding another user to the Ewon Router and setting a password to the minimum length that was accepted “aaa”.
3 char creds. Really?
So I tried iterating by character: “aab”,”aba” etc.
“BXWfyGY=”-> “.u.Èf” = “aaa”
“BXafyJY=” -> “.v.È.” = “aba”
“BXWciGc=” -> “.u..g” = “aab”
Oh no – this looks like per-character encryption. CyberChef time:

BINGO! Although we still have the two ending chars at the end, we can for now forget those. Now let’s see if we can get it do the full 22 length password.
And yes, we can, this was very labour intensive on CyberChef (Calculating 9.578097130411805e+52 values) so we wrote a python script to do this and left it running.
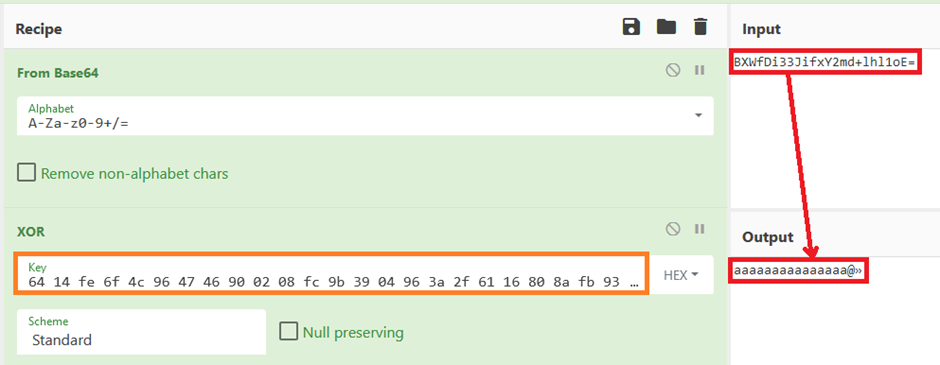
WIN
Now, how about trying this method on the private VPN certificate?

One private key. Boom
We tried this on several Ewon Flexy devices we owned. It worked on all. The Private VPN cert recovered and decrypted from the web app was the users own VPN certificate, this allowed us to connect to the users VPN as a device and reach internal networks (if connected).
Disclosure timeline
2019-01-29 – First contact with Ewon to report vulnerabilities
2019-02-04 – Confirmation of vulernabilities and estimated timeline provided by Ewon
2019-02-11 – Response from PTP that the timeline was too long, Ewon response as well
2019-05-23 – Final chase before disclosure
2019-05-28 – Response from Ewon, test firmware provided
2019-06-04 – Disclosure made by Ewon
2019-06-18 – PTP disclosed, updated FW 13.3s0 now available https://websupport.ewon.biz/support/product/manual-firmware-update/manual-firmware-download
Mitigations and Recommendations
The really obvious stuff:
Don’t put your Ewon Flexy (or any ICS device) on the public internet. That’s asking for trouble!
Change the default credentials.
Segment your IT and OT networks with decent access controls, obvs.
Use the free of charge Talk2M security connectivity cloud with your Ewon devices.
From the vendor:
HMS have a secure remote access solution called Talk2M which should mitigate the issue also: https://www.ewon.biz/cloud-services/talk2m
We haven’t tested Talk2M, so can’t comment on its security, but any additional layers of defence are usually a good thing. We’ll be taking a look at the new firmware when I get some time.
New firmware is available which should fix the bug. It should be available here: https://websupport.ewon.biz/support/product/download-firmware/ewon-firmware-0.
From us:
Update your Ewon Flexy firmware and keep it up to date.
Do that with all of your industrial control systems. If you can’t update an ICS (e.g. it’s too old / out of support / too critical to touch) then consider building additional security controls around it.
Conclusion
We haven’t finished with the Ewon Flexy yet, my continued research is here.
The vendor stumbled a couple of times along the rocky road of disclosure, but the end result was positive.














