TL;DR
- Livall smart ski and bike helmet app leaks the wearers real time position
- Group audio chat allows snooping on conversations
- Both issues are due to missing authorisation
- Bike app affects ~1 million users, ski app affects a few thousand users
- Fixed by the vendor, but after we had to call on a trusted journalist to escalate at Livall
Backstory
Some of us at PTP are keen skiers, and all of us are into IoT and connected devices. This means that smart ski tech is right up our straße!
Connected / smart products are continually emerging in the ski sector. We’ve looked at some in the past, including some rather cool Oakley / Recon goggles with a head-up display, some smart ski helmet speakers, and other ski tech.
This smart ski helmet from Livall caught our attention:

We’ve looked at their smart bike helmets in the past, but other than offering a Bluetooth speaker / microphone and LED turn signals, there wasn’t much in the way of smarts to play with, which is fine. That said, they have a popular group chat function that is also present in the ski helmet app. It was also vulnerable to the same issues.

These ski helmets have additional functionality; they come with an app that offers a push-to-talk (PTT) function and also the ability to track your friend group. Having lost touch with buddies on the slopes in the past, real-time geolocation can be a real boon.
The big difference over the bike helmets is that the PTT function can be used without taking the phone out of a pocket, simply by pressing a large button on the helmet. No need to get your hands cold!


This is a typical phone call on the slopes:
“Where are you?”
“Where are You?”
“I lost you. I’m on a red run”
“We can see you. Turn left. No, my left. No, not that way, the other way. You’ve gone down too far. Ah, we’ll meet you at the bottom”
Etc.
First look
We got hold of a couple of the helmets and set up the apps. The helmets are well designed and constructed, although they don’t include MIPS. At the price point that’s fair enough.
The setup process was interesting. There’s a one-time code function on first sign up, presumably to ensure that you have access to the email address being used to sign up to. We’re not sure how this adds to security though.
The microphone and location permissions are reasonable, without them providing PTT and geolocation would be impossible. However, the PTT and geolocation functions require the user to create or join a group, and this is where things got funky.
The vulnerability
First, user A creates a group. This creates a group with a 6-digit random numeric ID.

Next, user B enters the group code and joins.

Now user A can talk to user B in real time using the PTT function.
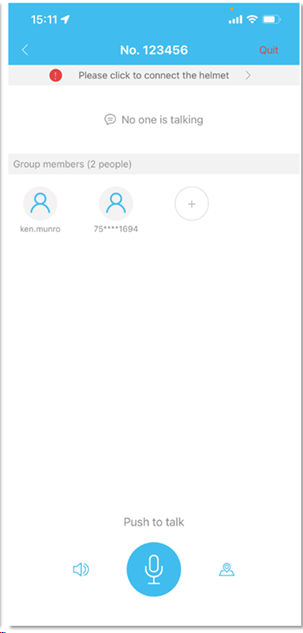
Both users can see each other’s location in real time. Multiple users can join the same group using that join code. Here’s one of our group at the end of a ski run:

Issue 1: insufficient randomness
That 6 digit group code simply isn’t random enough. We could brute force all group IDs in a matter of minutes.
Issue 2: no group joining approvals.
As soon as one entered a valid group code, one joined the group automatically. There was no further authorisation nor alerts to the other group users
It was therefore trivial to silently join any group, giving us access to any users location and the ability to listen in to any group audio communications.
Privacy concerns
The only way a rogue group user could be detected was if the legitimate user went to check on the members of that group. Until then, the rogue user would have the ability to listen to all PTT chat and, more importantly, track all group users in real time.
Until the app was closed or the legitimate users actively left the group, their location would continue to be leaked.
Further issues
Group exhaustion
Whilst not a security issue per-se, anyone could easily create every possible group in minutes, leaving legitimate users with no groups to create.
Create / join confusion
If a user enters a join code for a group that doesn’t exist, a new group is created instead. This has potential for confusion, rather than giving a ‘that group doesn’t exist’ error.
Outage
The entire platform went offline just before Christmas 2023. The error message needed a bit of translation!

So far it has worked about 50% of the times we’ve attempted to use it.
Functionality challenges
The PTT function didn’t work in iOS when the phone screen was locked, rendering it pretty much useless! It worked fine on Android though.
Disclosure
As is often the case, disclosure was a little painful. Only when we got a trusted journalist involved did we get a meaningful response from the vendor:
”We have always taken user privacy and security issues seriously…” said the vendor eventually
I’ll add “…when our brand and reputation are at risk”
Timeline
4th Jan 2024: we emailed [email protected], the only contact on their UK web site asking where we could send our report to. No reply.
5th Jan: we emailed [email protected]. They replied on Saturday 6th asking for details. A good sign.
7th Jan: we sent them details of the issues, asking for receipt of the report to be acknowledged within 48 hours. No reply.
11th Jan: we chased, asking for acknowledgement of receipt and asking if they had any questions. No reply.
We didn’t hear further from Livall.
22nd Jan: we got in touch with the awesome Zack Whittaker, security editor at Tech Crunch to see if he could get a response from Livall. Zack also pointed out that the Livall bike app has a lot more users than the ski app. I already had a Livall bike helmet, so quickly confirmed that it used the same API and had the same issues.
23rd Jan: the CEO of Livall replied to Zack. Funny that.
24th Jan: the CEO asks for two weeks to get a fix out. That wasn’t unreasonable, though both Zack and I felt that they should be taking down the API in the meantime. They refused, arguing that leaving it up improved the safety of skiers. WTF?
5th Feb: Livall got in touch with Zack to say that the app now featured much stronger group join codes. 6 character alpha numeric codes dramatically increased the randomness, largely solving the problem.
We are waiting to see if Livall will alert all users to update the app. In the meantime, updated versions of most versions of the apps have been pushed to the App and Play Stores.
Conclusion
We should not have had to involve Zack to get a response. Disclosure started so well, but then fell flat.
There’s plenty of advice around running a disclosure program here and here, if you’re interested. Most of it is simply remembering to communicate with the discloser.
We haven’t poked the Livall app particularly hard, so may yet revisit it and see what else might be there to find.
I spent some time using the Aleck smart helmet speakers on a recent ski trip. They have similar functionality to the Livall helmets and app, plus great audio, but here’s the group join code format:

A suitably random code. Shame that Livall had to be needled in order to increase the entropy of their join codes to something similar.
We have more research in to smart ski tech coming shortly, watch this space…














