It’s cold out there today isn’t it? Good job offices and schools are lovely and toasty thanks to well maintained heating systems. I mean, if someone were to find a way to hack them, over the internet, and turn them off it could cause mild chaos. Which reminded me…
Way back in 2006, I was given a Trend IQ3 Building Management System (BMS) controller. My interest was piqued as these devices were being installed in Heathrow’s Terminal 5, according to the manufacturers press release.
Smart building controllers manage door access control, heating, ventilation and air conditioning and much more. Remember the Target breach in the US? The ingress point was believed to be their HVAC management company.
I’ve just taken delivery of a used 2013 model of the same controller and a brand new 2017 controller from the same vendor. So, has anything improved?
TL;DR? A short summary:
Yes and no. The controller security has improved some, but we’ve found large numbers installed on the public internet, unprotected, with complete authentication bypass in some cases!
We found them in military bases, schools, government buildings, businesses and large retailers among many. Ripe for compromise of these organisations.
We also found some that had already been compromised to a point by malware. Further compromise would be trivial.
It’s about lax installers NOT vendors
Most of these issues have been caused by HVAC & BMS installers, rather than the vendor. The installers have exposed their clients through not following manufacturer security guidelines. The manufacturer could still make improvements though.
Here’s the rogues’ gallery: 2006, 2013 & 2017 at the bottom

I tried to disclose responsibly at the time, but got nowhere with the vendor. The story had a little coverage in the press – smart buildings weren’t a big thing at the time.
I presented the findings to GCHQ and the industry at the old CHECKCON conference too.
The vulnerabilities we found
The 2006 IQ3 Excite building management controller:
This one is running firmware version 1.2.6.2, here’s a list of what we found:
- Plaintext authentication
- Authentication bypass for embedded web server (see below)
- Reflected XSS on various parameters (reported again in 2013 by Darius Freamon, 7 years after it was first found it: CVE-2013-78004)
- Trivial session hijacking through incremental session IDs (e.g. http://192.168.0.244/modules.htm?param0=22, simply incrementing with every request)
- And a really fun memory leak in to broadcast UDP packets – ‘test1’ was the password set – here we can see it leaking in to packets broadcast on UDP/57612
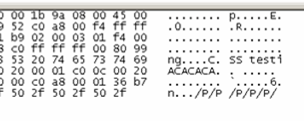
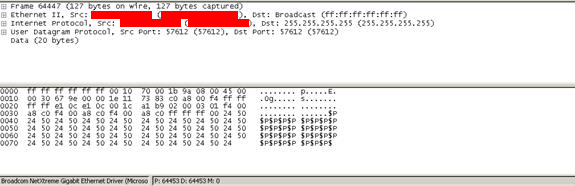
Trivial fuzzing causes a DoS & possibly a buffer overflow:
When fuzzed over FTP with APPE $P at size 513, the FTP server crashes.
But even more amusingly, $P is then found being broadcast over the network from the controller, which is clearly operating in a very odd state.
There was more, but the point is made…
Manufacturer security advice
Trend Controls, the manufacturer, offers some reasonable advice for installers. They make the point that these devices should be on isolated subnets and NEVER exposed to the internet:
https://www.trendcontrols.com/en-GB/Documents/General_Security_best_practice_for_Trend_IP_based_products.pdf
That’s good advice, though what efforts have Trend Controls made to ensure and audit their installers to ensure they aren’t installing insecurely? It took me less than 10 seconds to find >1000 exposed, vulnerable Trend controllers!
This advice also assumes that the threat is only from an attacker on the public internet. These controllers are found in quiet areas of buildings, hopefully in locked plant rooms and electrical panels. Ideal for the social engineer. Also, compromise the guy who manages the building, pop his PC and you can potentially unlock doors to order.
It simply shouldn’t be possible to install these devices in customer buildings this insecurely.
IQ3 Excite 2013 model, used
I bought this used from eBay. The firmware version was more recent and most of the significant flaws had been fixed. Authentication bypass was still possible in default configuration.
IQ412 Excite, latest 2017 model, new and unused
The XSS from 2006 has now been fixed, though we think there’s still a convoluted XSS present. There’s also plenty of opportunity for CSRF. Auth bypass was still present.
Shodan searches
www.shodanhq.com couldn’t be better suited to finding these controllers. Installers helpfully name the controllers right at the top of the embedded web server home page.
With a search for the names of a couple of types of controller I got ~1,000 hits without trying hard. Check out some of these- redacted for safety and privacy:
This looked like the HVAC system looking after microbiology at a university:
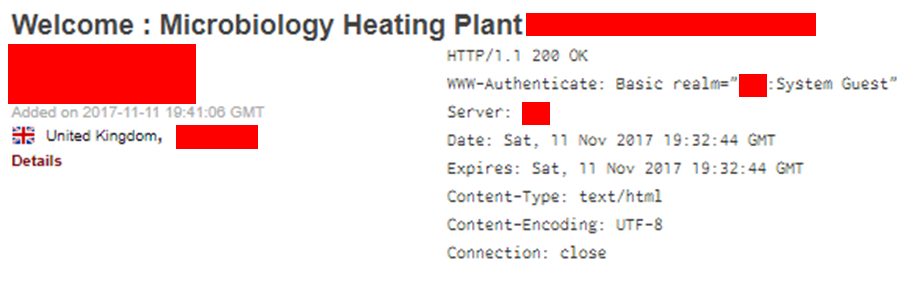
This was an easily locatable London restaurant:
This was possibly the development site at a former brewery:
This was a fire station:
This was an infants school in Chelmsford. Heating controls at a school? School closed because the heating isn’t working on a cold day? That would cause chaos for parents!:
Authentication bypass
Whilst the XSS could be useful, by far the most interesting security issue was a complete authentication bypass.
This is present if the ‘guest’ user has not been created. It’s weird behaviour, but if the guest account has not been added, anyone can add it.
Looking at the web UI, click ‘modules’ in the top nav bar then look at the options on the left hand margin. If ‘users’ is present, then you can add yourself a new user:

And here’s the ‘create new user’ option:
Take control… Manipulate all input & output. Unlock doors, turn heating and refrigeration off? Set off alarms? Use the controller as a stepping stone in to the corporate network?
Compromised controllers, serving malware?
Many of these controllers also have FTP enabled, often with simple, default or blank credentials. This is where it got a bit silly:
Whilst clicking through the web UI of a BMS controller, anti-virus popped up.
On poking around further, it appears that a number of these controllers have been compromised over FTP by a crypto mining worm: Win32/Crytes
We don’t think that the worm can actually execute on the controller, but it has successfully dropped an infection marker in to the web page covering network config (modules | networks)
A simple GET request shows the following marker appended to the web page:
iframe src=Photo.scr width=1 height=1 frameborder=0
We found the same marker on multiple controllers on the internet. Whilst on this occasion the vendor/installer/clients have dodged a bullet, it would not be difficult to write malware that did successfully infect these controllers.
Searching for other BMS controller brands
Trend Controls aren’t the only BMS controllers we’ve found available on the public internet. Useful Shodan searches include:
“G50” – the Mitsubishi G50 BMS
“Saia PCD BMS Web Server” – this features plaintext login. There’s no username, just a password!
Conquest BACnet Controller” – default creds of admin/admin are common
“BACnet Communication Module”
“ACP BACnet”
“Distech Controls BACnet Router Configuration”
“Server: BACnet4Linux”
“SIP Modbus Trend”
Not really a BMS, but searching for “webrelay” will find you very simple, insecure online relays. Amusingly, we’ve found that the relays will actually trigger if you port scan them hard! We achieved this consistently on two we bought for testing.
Conclusion
Building management systems are often installed by electricians and HVAC engineers who simply don’t understand security.
Ask questions about what ‘stealth’ technology is in your buildings. Ask the guys who look after your HVAC how it’s monitored and managed. Whilst you’re there, ask about your door controllers and your IP alarm systems.
BMS vendors need to wake up and smell the coffee: educate your installers, accredit them and audit them. Then ensure your product is as foolproof as possible, making insecure installation as difficult as possible.














