Tl;DR
- Scammers send emails to the payroll team in an attempt to change an unlucky employee’s banking details.
- They harvest LinkedIn for details about potential victims.
- An organisation can prevent this type of fraud by putting control measures in place.
- You can adjust your LinkedIn privacy settings to protect yourself, and your colleagues
Introduction
In my previous job as the SOC manager for a public sector organisation, I would often see attempts from scammers trying to get some unlucky employee’s payroll details changed to their own bank account. The emails weren’t exactly sophisticated and looked a bit like this:
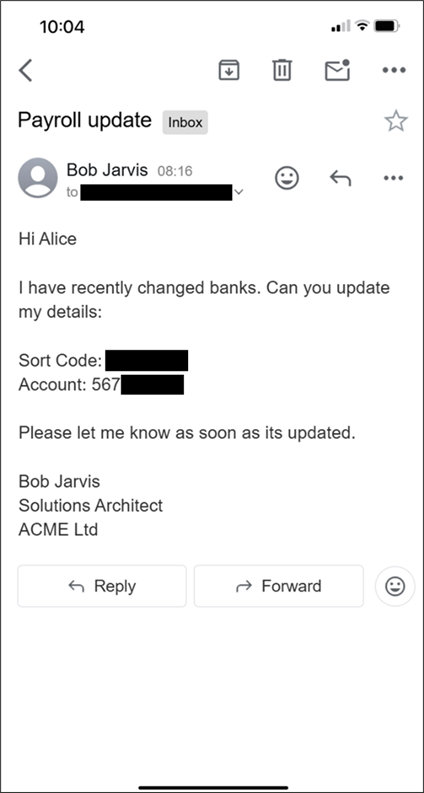
The sender’s email address would usually be a different and seemingly random Gmail address and would generally not match up with their victim’s name – something like [email protected]. In most cases, this red flag would be enough for the vigilant recipient to report the email as phishing, where it could be reviewed by the SOC team.
However, two aspects of the email added a bit of realism:
- They always managed to pick a recipient who worked in payroll, and
- The signature would usually contain the victim’s correct job title
It wasn’t possible to block these emails. There were no links, or patterns that we could have used to identify and filter them out.
Unfortunately, one time, the fraudsters’ chosen recipient was the head of payroll rather than a payroll administrator. They didn’t spot the red flag and simply forwarded the email to someone who could action the request, and in doing so added legitimacy to it. The request was no longer from a random external email address but from the head of payroll. The victim’s payroll details were then changed but luckily it was noticed before any money was sent to that account!
How can organisations and individuals better protect themselves?
From an organisation point of view, it’s crucial to have strong processes and procedures around updates to payroll information.
The easiest, and safest, approach would be to reject any request sent over email and allow employees to self-service (i.e. update the details themselves). Any system would need to have suitable security controls in place, such as MFA along with confirmation emails for any changes.
If that’s not possible, then the organisation should only accept requests made from internal email and always follow up with some form of validation, such as a phone call to a phone number on their file, before the details are updated.
M365 offers user impersonation protection, and Mimecast has a similar feature, which could help to block these kinds of emails, however the payroll team should be aware of them and have regular phishing awareness training.
In the above case, there were internal policies that tried to mitigate the attack path by having employees contacted to change any personal data. However, this wasn’t enough, as emails could be missed or ignored. Self-service wasn’t an option, so the organisation tightened its procedures and currently refuses any requests made via email. Before making any changes, employees are now required to contact the payroll team and verify their identity.
How can you mitigate the initial risk of becoming a target?
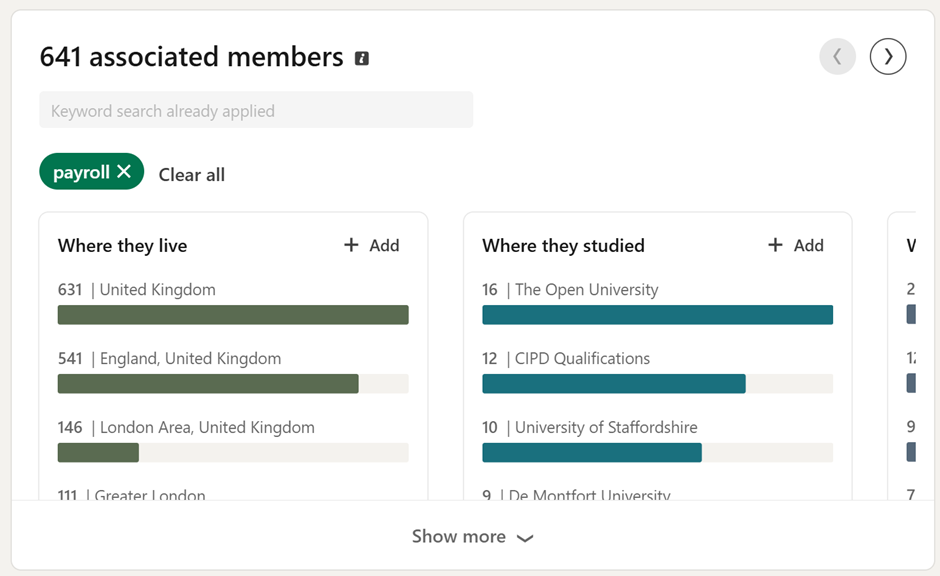
Well firstly, it’s important to know where the scammers are getting the information from. They aren’t hacking into databases, as they can easily find it on LinkedIn. It’s a straightforward approach. First find someone who works in payroll by using a Google dork to search for people with “payroll manager” or “payroll administrator” in their LinkedIn profile. The screenshot below shows a fake profile, but reflects one that an attacker could easily find.
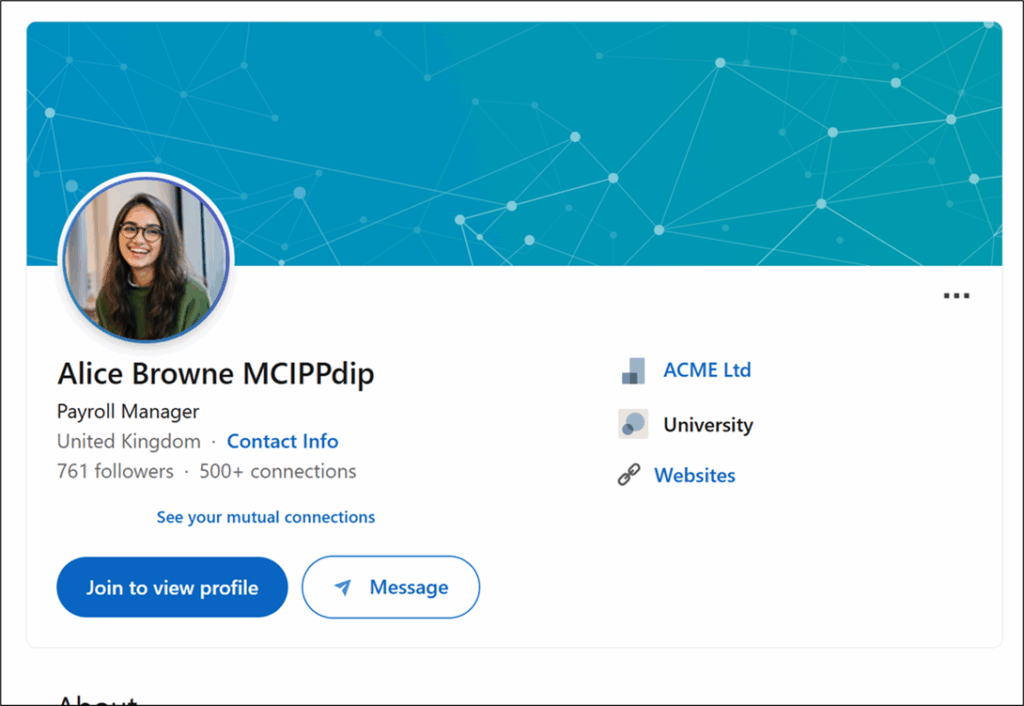
Once they have selected their first target, they will pivot and find someone else working in the same company. This can all be done without even touching LinkedIn, however by signing into LinkedIn and using the internal search, they can massively increase their proverbial net.
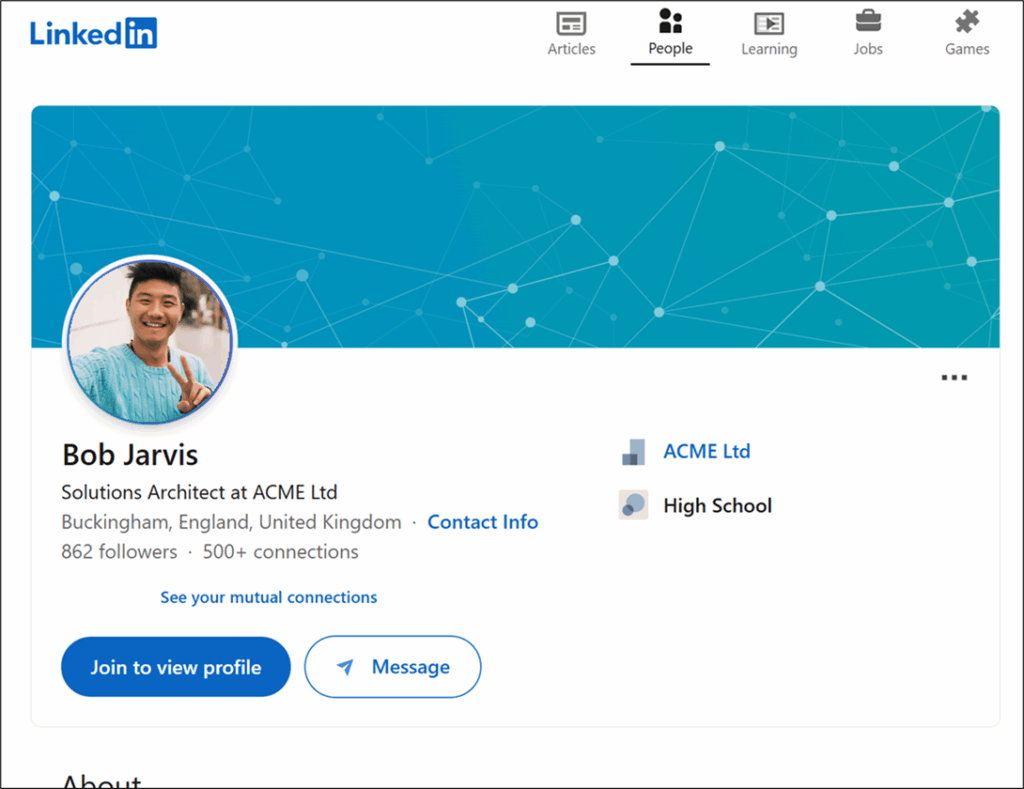
From there, a little bit of OSINT should help them work out the format of the payroll target’s email address – in this fictional case it was <firstname>.<lastname>@acme.ltd.
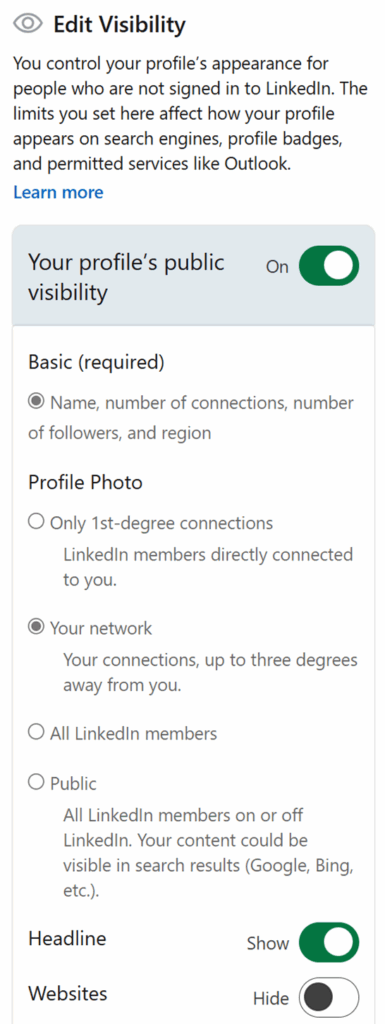
The most important thing you can do to protect yourself is to review your privacy settings on LinkedIn. However, this is easier said than done – a lot of people are on LinkedIn to promote themselves and boost their current and future career prospects. Therefore, adjusting your privacy settings could unintentionally decrease your visibility and prevent others from viewing your profile entirely, thereby defeating the original purpose of using LinkedIn.
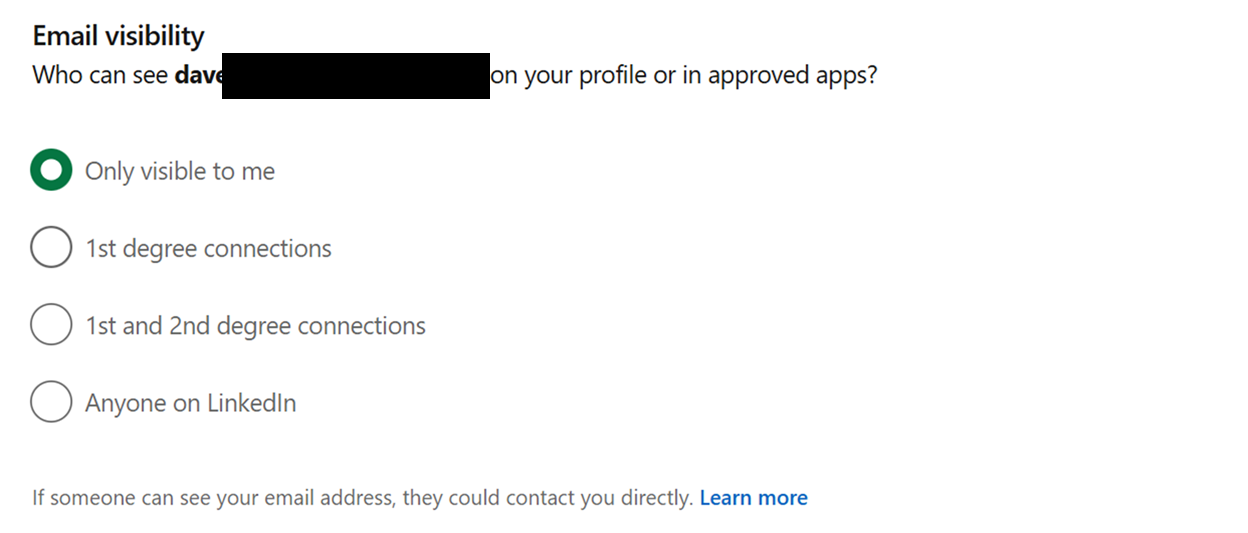
I’m not going to go into too much detail about the various privacy options available on LinkedIn – there are plenty of guides available. But there is one option that I would recommend everyone enables, especially those working in payroll, and that’s changing your last name visibility:
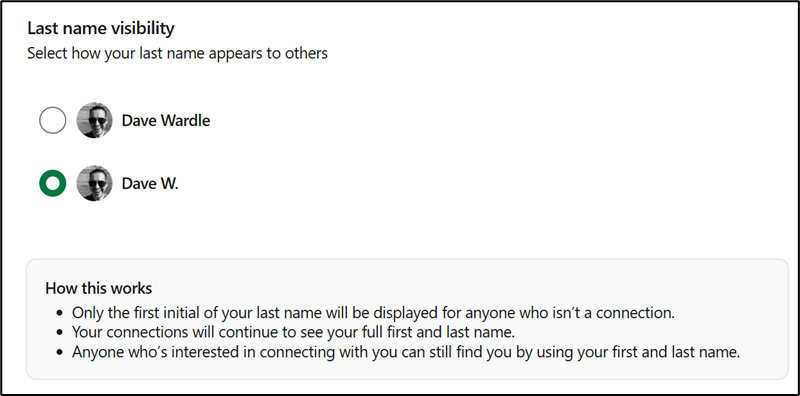
This setting means that only direct connections will be able to see your last name, everyone else will just see an initial. This one change will massively reduce the risk of your details being used in this kind of payroll scam.
Obviously, this relies on you being careful with who you connect with and keeping an eye out for fake profiles – the NPSA have a great campaign about this. You should also check that your vanity URL does not include your full name. You can change this to anything if it isn’t used by someone else.

While you are at it, I’d recommend reviewing your entire profile for unnecessary information. Consider adjusting your job title and limiting the amount of detail you share about your work. I’d recommend either removing (or tweaking) your job title and don’t go into too much detail about your work. The less information you put on LinkedIn, the less it can be used in a scam.
The theme of this blog post has been around payroll fraud, but the same tactics are used to aid social engineering attacks. Adding information helps add realism to spear phishing emails (e.g. Hi Alice, I’ve been working with Bob on Project X – can you send me some super-secret information? Thanks). I realise I’m getting off topic, so please take a look at the previously mentioned NPSA campaign.
Conclusion
This kind of fraud is, unfortunately, quite common. Hopefully this post will help you and prevent you from being selected as a target. However, if you have been a victim, then it’s important that you report it to Action Fraud as soon as possible.
Helpful settings:
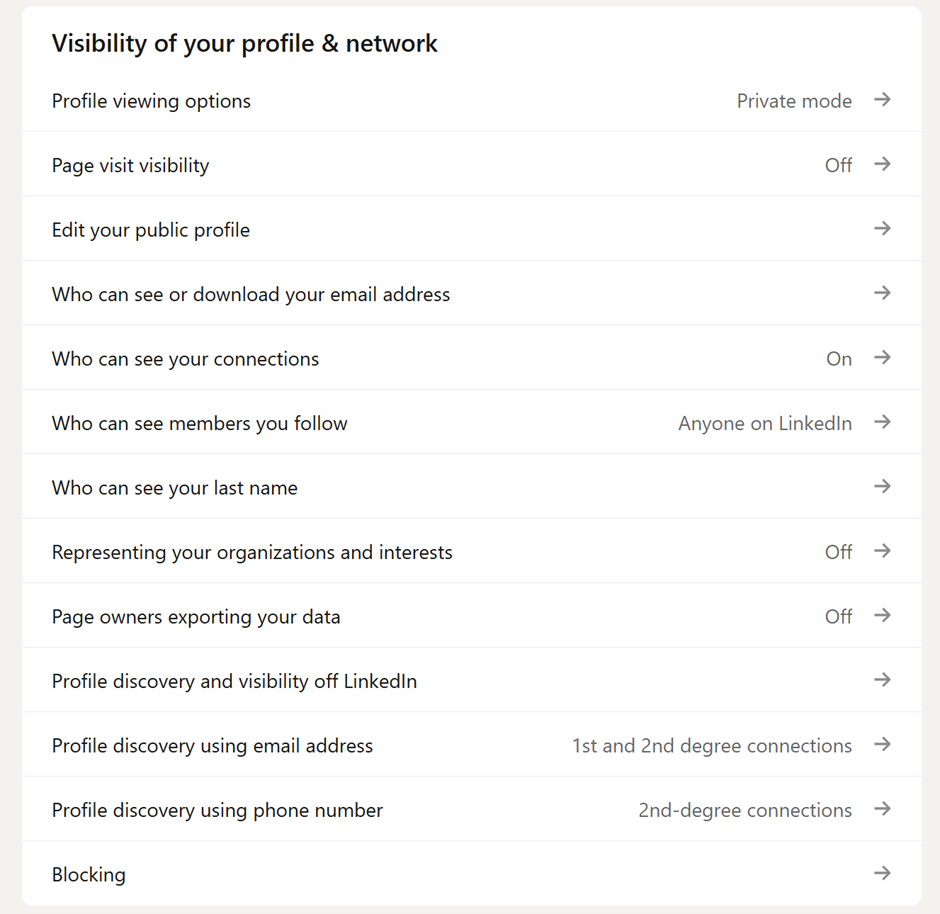
Your public profile: