IoT security flaws were always systemic: by that I mean that if I find a flaw in my smart thermostat, it affects ALL of those thermostats. A security problem with one connected car leads to problems with ALL the connected cars using that same system.
That led to incidents such as the Mirai botnet with CCTV DVRs and the Horus Scenario for solar panel invertors. One knocked social networks off the internet for a couple of hours, the other could be used to bring down the power grid.
Surely it’s getting better?
Standards and regulations are being drawn up and (slowly) implemented.
Manufacturers are learning from their mistakes. Painful stories in the media about data loss and device hijack offer an incentive for security to be done well.
Good resources are available online to help IoT manufacturers get security right, not least OWASP.
So what’s going wrong?
Many IoT manufacturers are starting to accept that they don’t have the skills to do smart product security in house, so they outsource. That’s a wise idea.
They look to third party service providers, often ‘one stop IoT shops’ that do everything for them – from chip specification to mobile app to API, everything.
There are plenty of excellent 3rd party IoT service providers. One I have personal experience of is Electric Imp, who provide the back end for the iKettle 3.0.
However, not all of these service providers provide such a secure service.
Super-Systemic
We are starting so see what we refer to as ‘super-systemic’ flaws in IoT now. What do we mean by that?
In the past, a flaw in a product meant that all of the instances of that product could be exploited.
Now, we’re testing IoT products and finding that the back end service provider has security flaws. Really serious authentication and authorisation flaws.
We find a security flaw in the service provider and now we don’t just have a compromise of the IoT product we’re working on, we have a compromise of EVERY IoT product that service provider services.
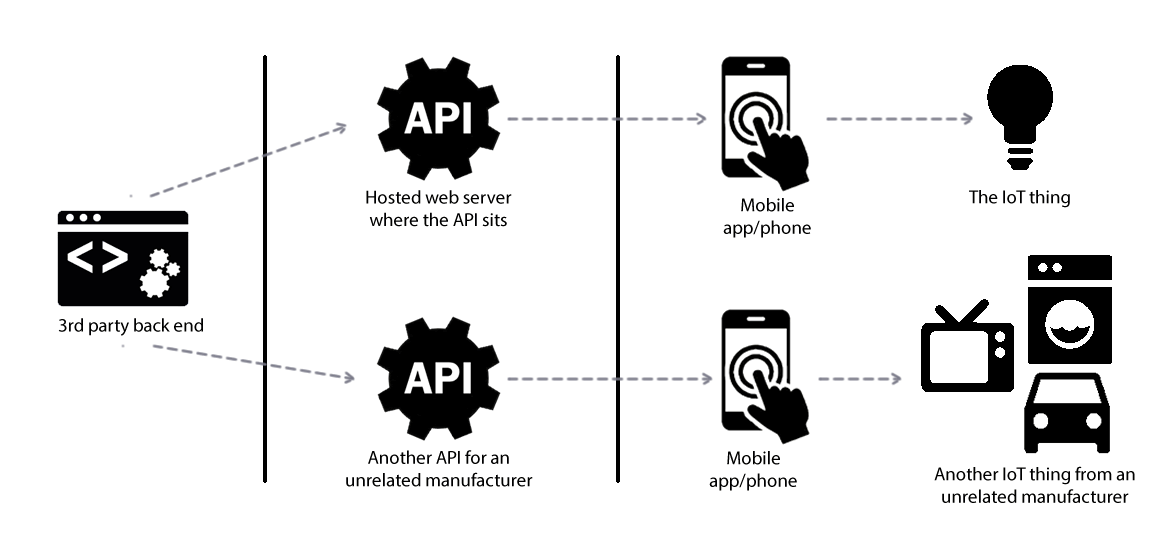
One we’ve recently looked at serviced over 300 different products covering over 100 different IoT manufacturers. What was a problem with one product is now 300 times worse.
Consequence
This is the worst possible case. IoT has always been ‘break once, run everywhere’ over that vendors product. Now it’s worse by several orders of magnitude.
By seeking 3rd party help, the problem has increased.
Advice
Carry out VERY thorough due diligence against any potential IoT service provider.
We spent some time reading the web site of the provider in the example above. The security pages read well: it had an email address for responsible disclosure, talked about pen testing and a dedicated in house security team.
Yet, it had a huge authorisation flaw for every IoT product its service was used for.