Almost all commercial airlines now use electronic flight bags (EFBs) to drive efficiency and safety in their operations. We’ve been testing the security of EFBs and their apps, here’s our latest findings.
TL;DR
- Many airlines use Lufthansa Systems’ Lido eRoute Manual for their EFB approach plates.
- We found an integrity check bypass that allows modification of data presented to pilots.
- This could increase the chance of controlled flight into terrain (CFIT) on non-precision approaches in instrument conditions.
- It relies on a weak EFB device build, plus physical access to the device or some way of upstream injection for the update.
- Weak EFB device security is not uncommon in airline operations.
- Lufthansa Systems responded quickly to our disclosure.
- The issue was fixed in the latest version of Lido eRoute Manual. Lido eRoute Manual release 5.11 now includes protective mechanisms against data manipulation.
- Use of this app has reduced significantly since we first disclosed the vulnerability, owing to migration to newer versions. It was being used by a large airline when we discovered the issue.
- Remediation took around 18 months, which is not unreasonable given the highly certified aviation software environment.
Detail
We reviewed Lido eRoute Manual for Windows version 4.2.2.6 installed on an EFB.
The integrity of data is not checked effectively – verification and checksum methods used are vulnerable to manipulation. This could result in an attacker modifying files directly on EFBs, or by intercepting the supply chain of updates.
The application makes use of MD5 checksum files alongside databases to verify that the contents of files have not been changed. By reviewing the Java libraries, the code involved to create these checksum files is easily reverse engineered.
AES keys are hardcoded in Java classes which are readily accessible from the Lido installation. A relatively weak key was also the default.
We were able to reverse engineer the MD5 comparison functions to create a tool which would create the correct string of hex bytes based on the filenames, path and the previously mentioned keys within the libraries.
Example code used to re-generate binary (.md5 suffix) files:

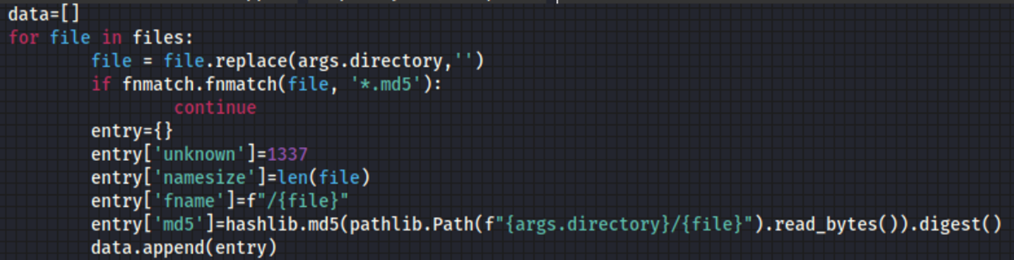
Chart and document modification examples are given however these are only used to illustrate some of the possible effects of modifying the data rather than as an exhaustive list of data that could be modified or manipulated.
In particular, chart modifications are significant as they are the primary source of navigational information for pilots. The Flight Management Computer (FMC) database is compared for accuracy with charts however if there is a discrepancy between the two then it is the information provided on the chart (not the FMC) that takes precedence.
An attacker would need physical access to an EFB in a poorly hardened state (which is the responsibility of operators presently) or by some means of attacking over the air updates or source data. We did not find any mechanism in the LIDO app for these but again, some operators have different deployment mechanisms to exploit this vulnerability.
Approach Plates
As part of a non-precision approach (so where no Instrument Landing System or ILS is present) as found in numerous regional airports where expensive ILS has been retired or was never invested in, approaches are made by descending at known safe rates to known safe altitudes.
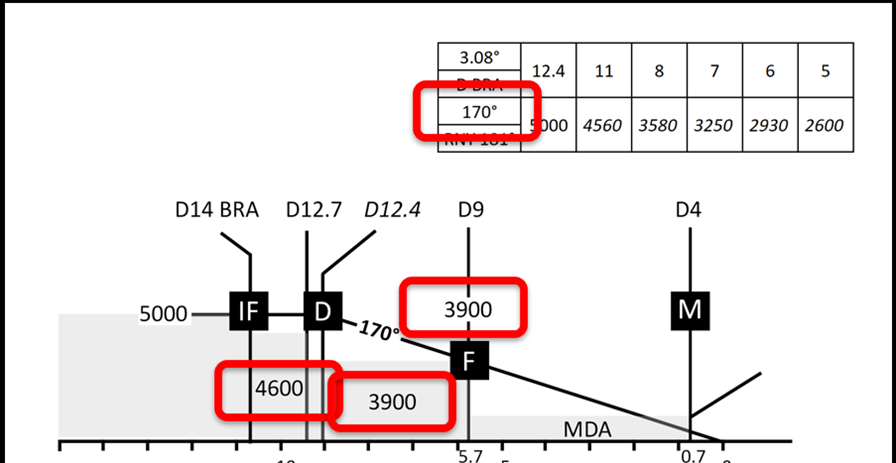
Here we have a plate showing one such approach to runway 18R at Barajas airport in Spain. The pilot should approach at 5000 feet to the Initial Fix (IF) at 14 miles from the BRA VOR (a ground based navigational beacon).
From the IF it is safe to descend to a minimum of 4600 feet to the Top of Descent (D)
From there you should take a magnetic bearing of 170 degrees to the Final Approach Fix (F) and descend to 3900 feet by 9 miles from the VOR.
Finally, you can descend to the Minimum Descent Altitude (MDA) until the Middle Marker (M) at which point a decision to land if safe or go around is required.
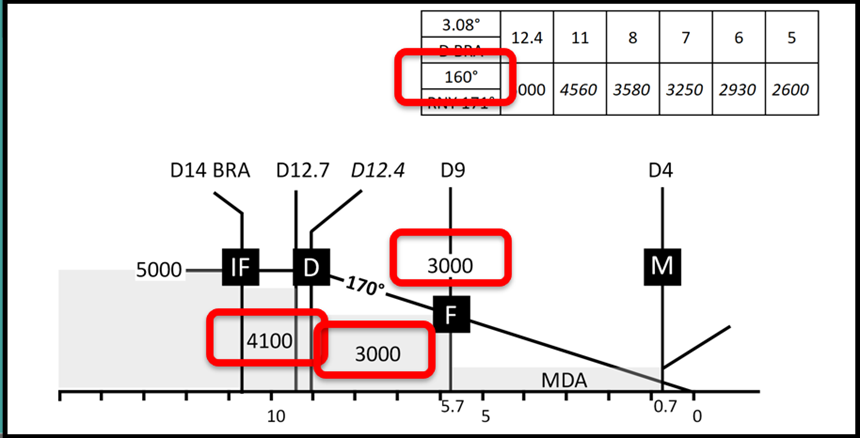
This descent profile is required because the approach area to the airport is hilly.
We discovered that we could modify the data just a little to avoid pilots noticing gross errors, but enough to cause the plane to descend into terrain.
Now, there are plenty of opportunities to avoid an incident, even if pilots are misled. Air Traffic Control operators may notice the unexpected descent and alert pilots.
Sadly EGPWS is less likely to alert, as some terrain collision warnings are disabled when on approach, as otherwise multiple false alarms would result
Lido eRoute Manual has plenty of other features
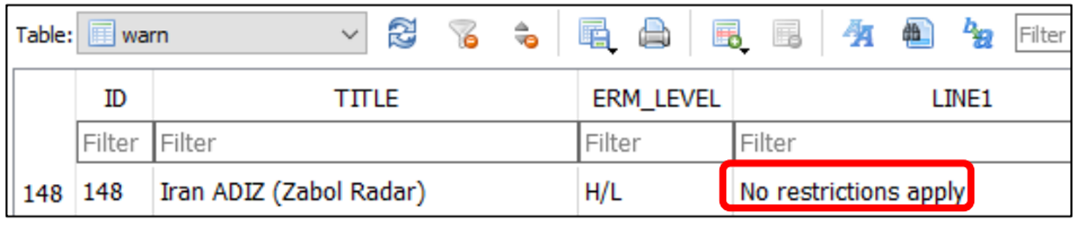
One that alarmed us was the potential to remove airspace warnings. For example, it’s mandatory to call Zabol Radar before entering Iranian airspace.
If you fail to do so, there’s a high chance that Iranian Air Defense will engage the aircraft.
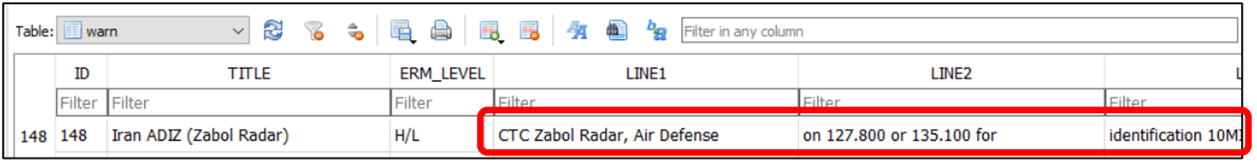
It’s trivial to remove the warning:
Other features include:
- High level charts, used for navigation during the cruise.
- Weather deviation procedures, so what a pilot should do if over say the North Atlantic in the event of heavy turbulence. Tampering with this may bring planes into conflict.
- En route NOTAMs are used to alert pilots to airspace changes.
- Airport ground charts, so potential to delete obstacles or modify taxiway width restrictions, leading to something akin to this:
There was an incident with a BA 747 at Johannesburg airport in 2015, where an experienced pilot taxied in to a building, partly a result of faulty taxiway visual aids and partly a loss of situational awareness by the crew.
It important to mention that the pilot is still responsible for the situational awareness and they cannot solely rely on the ground chart.
Disclosure timeline
Lufthansa Systems were alerted to the vulnerability on the evening of Monday 17th May 2021.
The report was acknowledged by Lufthansa CERT on Wednesday 19th May 2021.
At first we were directed to HackerOne. However their terms prevent public disclosure if the recipient organisation doesn’t want it so this wasn’t an option for us.
A request for an NDA was made by Lufthansa . We made it very clear that an NDA wasn’t appropriate.
We then had a great call with the Lufthansa CERT and it became clear that both parties understood each other.
We’ve since had really positive exchanges with Lufthansa and are really pleased that the vulnerability has been fixed, together with coordinated disclosure.
A happy ending!
Statement from Lufthansa Systems
Lido eRoute Manual version 4.2.2.6 was released in October 2015.
Only one customer was still using that version while transitioning to Lido mPilot, our iPadOS Version.
Lido eRoute Manual Version 4.2.2.6 reached end-of-life in May 2017. We urge all our customers to always update to the latest version. The current version is Lido eRoute Manual 5.11, released in June 2022.
It is worth remarking that the pen test was performed while having full access to the device and the application. The manipulated data are usually underlying access control measures by the airline and would not be accessible by a regular user.
Another important remark is that pilots are always obliged to look outside to see and avoid. Especially but not only during ground operations as well as when ATC is not responsible for separation.
We agree with Lufthansa, particularly around ground manoeuvring.
Recommendations
Defence in depth is critical to EFB security. Both the device and the apps running on it need to be secure. This attack relies on the EFB device being vulnerable, though this is not uncommon in our experience of testing lots of different EFBs for various operators.
EFB hardening is the responsibility of the airline and their device supplier.
There is no “one size fits all” solution as it depends on a variety of factors (e.g. device used, airline policies etc.) Given that installed EFBs are harder to access this helps to mitigate some threats but it doesn’t necessarily prevent physical access, for example cleaning/maintenance crews, or cabin crew (arrival at aircraft prior to pilots).
Portable EFBs make physical access much easier with them regularly being used as personal devices in public areas such as shopping malls and hotel lobbies/restaurants etc. Even if restricted to remaining inside the pilot’s flight bag whilst on layovers physical access is possible by hotel staff.
There’s plenty of advice in our post about hardening EFBs, but some options include: Possible security hardening options for both portable and installed EFBs:
- All applications including third party and internally sourced should be reviewed to ensure coding is secure
- Mobile Device Management (in particular detection of jailbreaking and monitoring of installed software and versions)
- Two-factor authentication, for example on a pilot’s mobile phone
- Applications on EFBs restricted to only those required for operations (prohibit personal email/messaging applications or unnecessary applications such as games – all often found on portable EFBs)
- Regular updates (although the challenge of assessing compatibility with EFB applications needs to be considered). Lufthansa Systems urges all customers to use latest and updated version of Lufthansa Systems’ products.
- Pilot cyber training. Importance of complying with security policies/appropriate use of EFBs etc.
Conclusion
This was a very positive disclosure experience, Lufthansa were kind enough to include a note of thanks:
Lufthansa Systems GmbH & Co. KG would like to thank Pen Test Partners for their research, professionalism and collaboration.














