TL;DR
- How RDP Bitmap Cache can reveal user activity
- No RDP logs? How can we reconstruct RDP activity?
- How cached tiles can uncover insider threats
Introduction
A lot of people are aware of RDP and what its functions are. It’s known for providing remote access and making life easier for administrators and users. With that comes insight for forensic investigators, regarding the ‘bitmap cache’. This is often overlooked, but when analysed correctly can provide some great understanding about what’s happened on a system.
What does that look like? Let’s say a threat actor has gained access to a system via RDP. They’ve then attempted to cover their tracks by wiping traditional RDP artefacts left behind such as logs, but the lesser-known bitmap cache can still hold valuable clues.
In this blog post, we’ll explore the DFIR techniques for digging into the RDP bitmap cache to reveal what was on the screen, even after the user has gone.
What is the RDP Bitmap Cache, and how does it work?
Like many other tools and browsers RDP optimizes performance by caching screen elements locally on the machine. Instead of repeatedly reproducing static icons, backgrounds etc. RDP stores these as small tiles in the bitmap cache. These tiles persist even after remote desktop disconnection, which creates a cached record of remote sessions.
The bitmap cache mechanism is ultimately designed to enhance the user experience and reduce the amount of data transmitted over a network. Each screen element is divided into small tiles, these tiles are hashed, which avoids duplication of the same tiles, ensuring that only unique tiles are cached. These tiles are stored in the user’s profile directory: (%USERPROFILE%\AppData\Local\Microsoft\Terminal Server Client\Cache)
Significance for DFIR investigations
Cached tiles can be reassembled to recreate the screen as the user had seen it during an RDP session. This is valuable if the session was encrypted, or other artefacts of relevance have been wiped. The persistence of these artefacts means that even if the user has attempted to cover their tracks by deleting files or clearing logs, the bitmap cache may still hold clues as to what their actions entailed.
Real-world scenario. Traditional RDP logs have been wiped
In a recent investigation into a threat actor who had exfiltrated sensitive data from an organization, we discovered that the adversary had used RDP to access a critical file server but had deliberately wiped traditional artefacts on the initial access machine including Windows Event Logs, TerminalServices logs, and $Security.evtx.
However, the RDP bitmap cache folder remained intact. Using BMC-Tools, we were able to extract over 8,000 files and begin to put pieces of the puzzle back together. The bitmap cache provided some key breakthroughs.
Network issues and administrative account access:
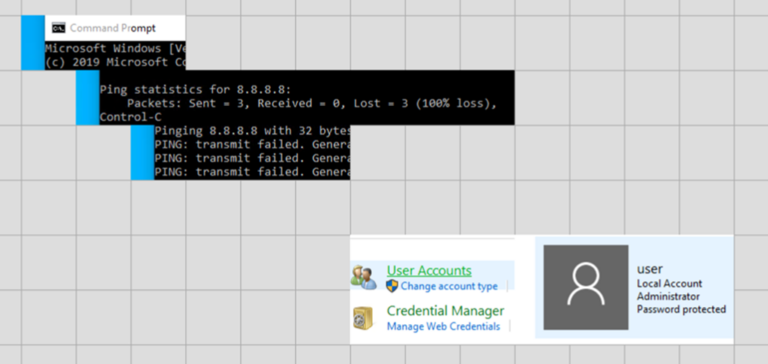
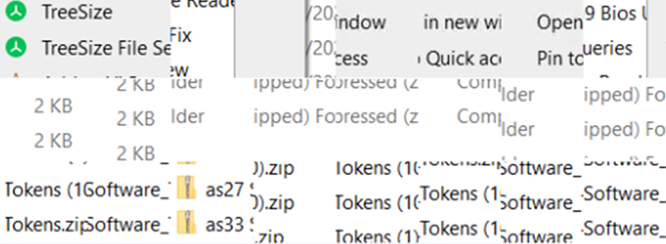
TreeSize present and credentials archived:
PowerShell scripts attempting to run – blurry due to actual tile size:
Malware alerts, alert artefacts were wiped – blurry due to actual tile size:
We were able to recover the cached tiles from BMC and stitch them back together using RDP Stitcher. We could evidence that during the RDP session the user had used TreeSize. It was most likely used as a reconnaissance tool to identify locations containing valuable data, compress sensitive datasets into 7zip archives, exfiltrate the datasets to external destinations including TOR hidden services and extract credentials and authentication tokens. Stitching the artefacts back together we were able to see images of open password manager windows and plaintext credentials visible in configuration files.
The reconstructed tiles revealed the hostname of the remote machine being accessed, which allowed us to pivot our analysis to a secondary host, where we uncovered more traditional artefacts including PowerShell logs, Sysmon events and evidence of credential dumping, which were no longer available on the original host.
By correlating evidence from both of these hosts, we were able to reconstruct the full attack chain. Evidencing the threat actor’s entry into the system, the reconnaissance that had taken place, the data being exfiltrated, and their eventual exit from. The RDP bitmap cache played a key role in bridging the gaps left by anti-forensic techniques used by the attackers, allowing the full intrusion to be established.
Analysis of the cache. Tools and techniques
Certain tools and techniques can be used to analyse the bitmap cache, let’s run through them:
1. Extracting the cache
The first step is to extract the cache from the machine; the bitmap cache is found below. %USERPROFILE%\AppData\Local\Microsoft\Terminal Server Client\Cache:
2. Reconstructing the cache
Several tools can be used to parse and reconstruct the cached tiles, I have used BMC-Tools which is a python-based utility designed to parse the .bmc files, provide all tiles individually and also a collage of the tiles together.
BMC-Tools:
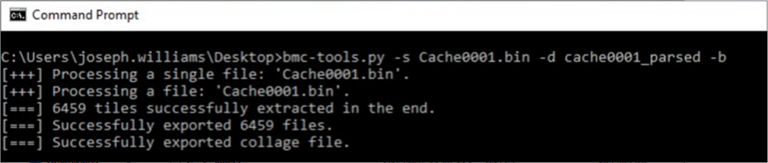
From one cached session file, BMC-Tools has exported 6459 files, alongside a collage file, which provides us with the following files:

One of the main challenges once we have parsed these tiles is the arrangement of those tiles. The tiles are stored. BMC-Tools attempts to put these tiles in a readable format, but the results are hit and miss. To provide an example of this, let’s look at the collage of these tiles:
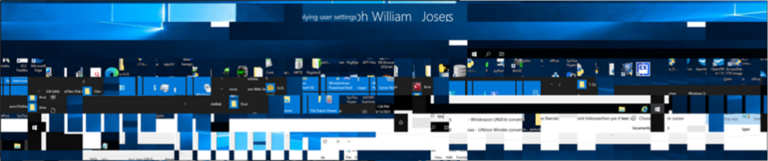
Although we can figure out what some of those tiles might be, it’s still tricky to work out what was going on during this session, we can see some potential forensic tools, a username and that’s about it. That’s where RDPCacheStitcher comes in, this is a tool which supports analysts in reconstructing the bitmap, using raw cache tile bitmaps extracted by tools like BMC-Tools. RDPCacheStitcher provides a graphical user interface and placement heuristics for putting tiles together so that meaningful information can be reconstructed.
Spending a few minutes piecing things together, we can see some forensic tools on the desktop, a user trying to access a location they don’t have permission to access, a text file, what was present on the start menu at the time of RDP connection and the user account signed in. Whilst this doesn’t provide the most exciting of examples, it provides an insight as to how we can go from a mess of over 6,000 32×32 individual tiles, to a legible representation of what has occurred on a system during the remote desktop session.
RDP Cache Stitcher:
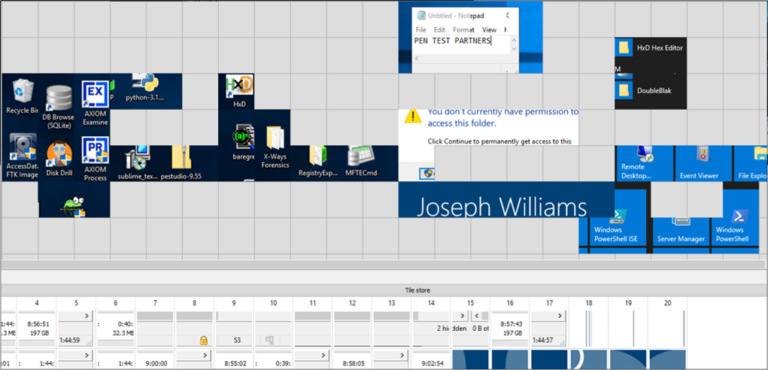
Visual placement heuristics
RDPCacheStitcher uses visual placement heuristics to simulate human pattern recognition to determine where one tile fits in relation to other tiles, based on their similarity to one another. Ultimately, the goal is to provide the analyst with tiles ordered in a way that makes it easier to reassemble an image, from many small, unordered cached fragments.
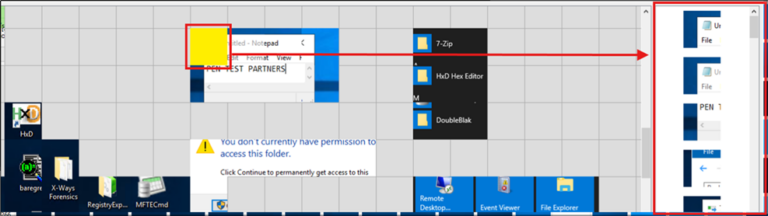
To provide an example of this, take the image below – the tool has used edge pattern matching to compare the pixels along the edges of one tile to those of adjacent tiles (left, right, top, bottom) e.g. if the right edge of Tile 1 matches the left edge of Tile 2 closely in colour or pixel pattern, the heuristic suggests placing them next to each other, though the results are hit-and-miss.
Similar tile results:

The tool does however offer another useful feature whereby when you are adding your tiles to your workspace, clicking an empty tile will provide you with a list of tiles that it thinks might fit in the space you have selected, i.e. in the image below, the tool correctly gives us the left-hand corner tile of the text document.
It is worth noting that the cached tiles aren’t stored sequentially, and the matching is achieved through many visual placement heuristic techniques including edge similarity, colour matching, pattern continuity and pixel similarity. Whilst it doesn’t automatically perform full reassembly, it speeds up the manual work for analysts dramatically by doing some of the comparison legwork in the background.
Recent exploit
In January 2025, Cyber Security News reported that hackers had been successfully reconstructing RDP session frames. With additional tools, such as BMC-Tools and RdpCacheStitcher, attackers can attackers rebuild visual representations of the victim’s screen activity, including usernames and passwords. This allows threat actors to silently view credentials entered during RDP sessions without needing keyloggers or full screen captures.
Conclusion
The RDP bitmap cache is a witness to remote desktop interactions, providing forensic analysts with an insight into past activities. By understanding and using specialized tools, analysts can piece together potentially crucial evidence when other forensic insights are not available.















No Comments yet!