TL;DR
- Unallocated space retains remnants of deleted files, metadata, logs, caches, and other artefacts.
- This is useful if a user attempts to cover their tracks, delete files, reformat drives, or use anti-forensic tools.
- These remnants can help reconstruct user actions exposing data exfiltration efforts.
- We provide a breakdown of how PhotoRec is used to recover files based on file signatures even from damaged or reformatted media
Introduction
In digital forensic investigations involving suspected data exfiltration, the analysis of unallocated space plays a critical role. Unallocated space refers to portions of a storage device that are not currently assigned to any active files or folders by the operating system.
Although this area appears unused, it often contains remnants of previously deleted files that have not yet been overwritten. These remnants can include entire files, partial data, or residual metadata.
From the forensic image below it’s possible to extract the unallocated space:
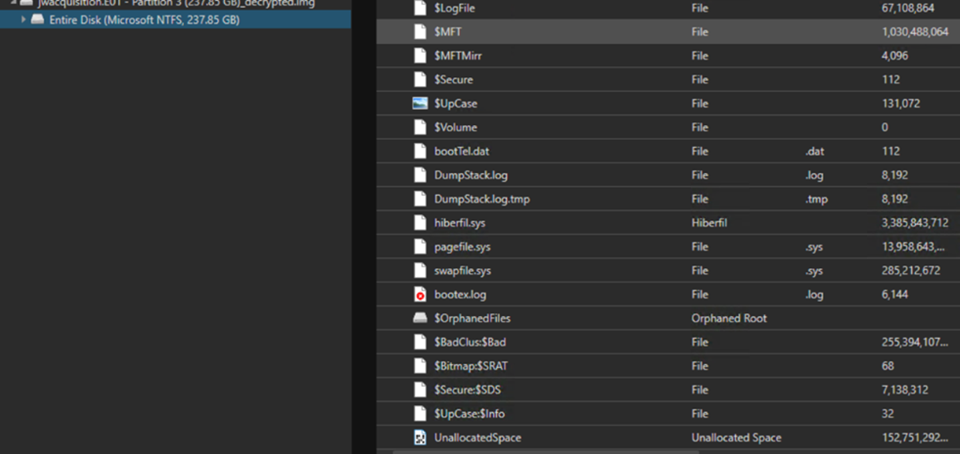
Unallocated space explained
When a user deletes a file, the operating system typically only removes the reference to the file in the file system index, leaving the underlying data intact until it is overwritten by new content. As a result, unallocated space can retain significant evidential material, especially in cases where individuals have attempted to delete incriminating files to cover their tracks.
Forensically recovering this data can reveal confidential documents, file transfer logs, or fragments of data that were moved or manipulated during the suspected exfiltration.
In some instances, the analysis of unallocated space also uncovers traces of anti-forensic techniques. Users may attempt to obfuscate or destroy evidence using deletion utilities or by reformatting storage media.
Despite these efforts, forensic tools can often recover artefacts from unallocated areas that indicate such actions were taken. These artefacts may include temporary files created by compression tools, encrypted containers, or remnants of command-line scripts used to facilitate exfiltration.
Furthermore, the recovery of files and associated metadata from unallocated space can contribute to the reconstruction of user activity over time. Timestamps embedded in file fragments can help determine when specific files were created, accessed, modified, or deleted. This temporal information can be vital in correlating data movements with other investigative findings, such as login times or network activity.
Data recovery with PhotoRec
PhotoRec is a data recovery tool designed to retrieve lost files from a variety of storage media, including hard drives, memory cards, and USB drives. Unlike traditional file recovery methods that rely on the file system structure, PhotoRec scans the raw disk surface for known file signatures, allowing it to recover data even from damaged, deleted, or reformatted partitions.
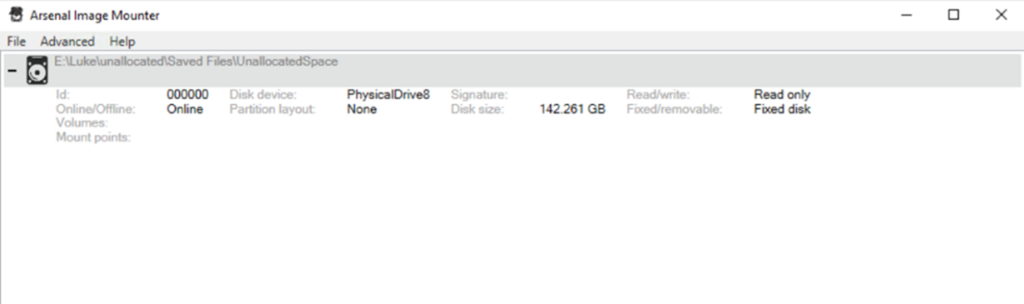
After extracting the unallocated space from the forensic image, the next step involves mounting it as a logical volume. This allows forensic tools to interact with the data as if it were a live file system, enabling more efficient searching and analysis.
Mounting provides a structured view into otherwise raw binary data, making it easier to locate recoverable files and understand how they were used or manipulated. This process is crucial when trying to recover artefacts that are not detected through signature-based carving alone.
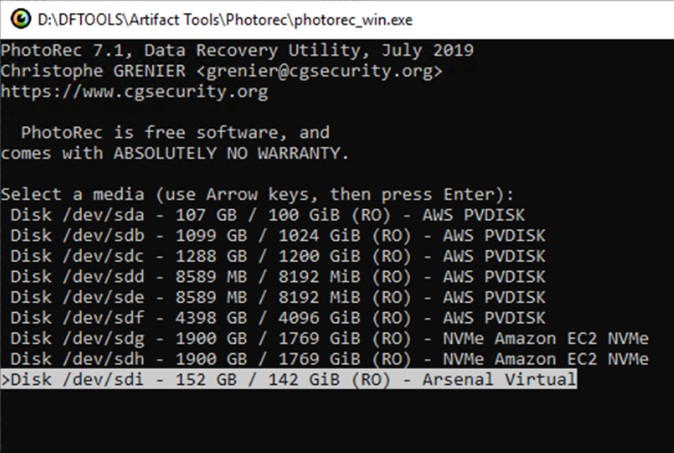
Once the unallocated space is mounted, the forensic analyst selects it within the analysis toolset. This selection ensures that subsequent operations—such as keyword searching, file type filtering, and metadata extraction—are performed on the correct data source. By treating the mounted space as a drive, investigators gain the ability to apply familiar workflows, such as browsing directory structures or conducting targeted searches, despite the fact that the original file system is no longer intact.
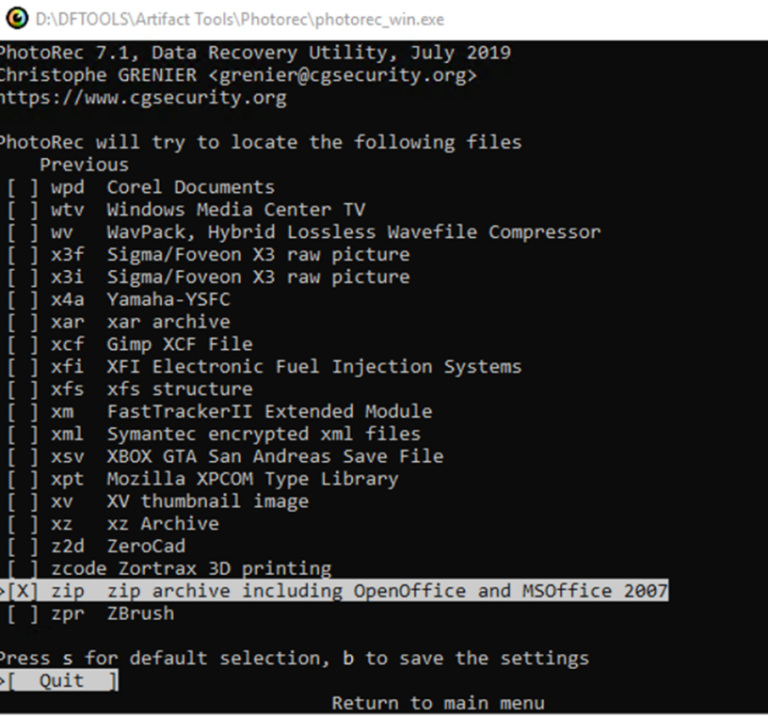
With the volume mounted, the focus shifts to identifying and isolating files of forensic value. In this investigation, the search targets include Microsoft Office documents, text files, compressed archives (ZIP, 7z, RAR), and script files.
These file types are commonly associated with data exfiltration or the tools used to carry it out. For example, confidential information is often stored in documents or spreadsheets, while compression formats may indicate attempts to bundle and transfer large amounts of data. Script files, on the other hand, may reveal automation or obfuscation techniques used by a suspect.
By filtering for these file types, the analyst can prioritise the most relevant content, streamline the review process, and build a clearer picture of any data leakage or malicious intent
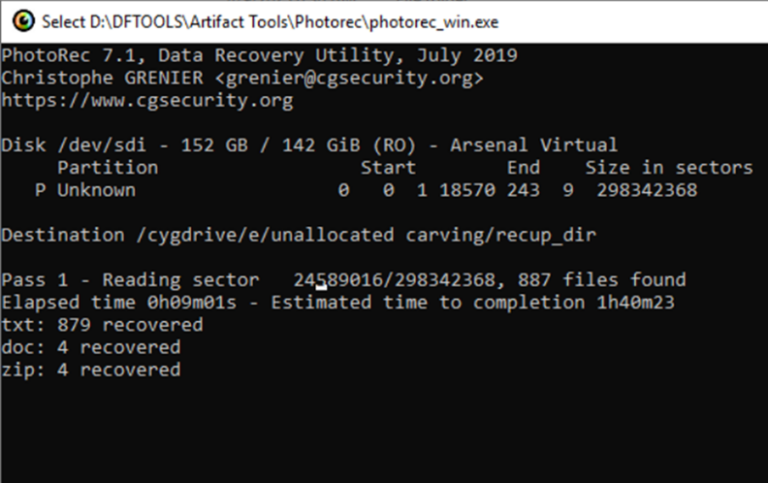
Unallocated space can contain a wide range of interesting and potentially crucial artefacts that are no longer visible in the active file system but still reside on the disk. These artefacts may include deleted documents, spreadsheets, emails, and multimedia files that were intentionally or accidentally removed. In forensic investigations, such data can provide insight into user behaviour, intent, and actions leading up to an incident.
Beyond standard files, unallocated space often holds fragments of application data, temporary files, and internet artefacts such as cached pages, cookies, and browser histories. These remnants can help reconstruct web activity, revealing visited websites, downloaded content, or use of cloud storage services.
Additionally, forensic analysts may uncover scripts, batch files, or remnants of executable programs—often used in automation or data exfiltration. Metadata embedded within these files, including creation and modification timestamps, can help build a timeline of events.
Unallocated space may also retain logs, chat fragments, password remnants, and registry keys from deinstalled applications, offering a glimpse into past system configurations or user preferences. In some cases, even entire file system structures from deleted partitions can be partially recovered, further enriching the investigative narrative.
Conclusion
Overall, the unallocated space serves as a digital graveyard where traces of past activity persist, often containing the most revealing evidence in cases involving tampering, deletion, or attempts to cover one’s tracks.















No Comments yet!