You may have seen the furore around the Barnacle windscreen-based parking clamp back in January this year. It’s a different approach that allows the clamp to be unlocked remotely, so you don’t need the clamp company to come remove it for you.
If you’re not familiar with the device here’s a video from Kevin Dougherty CEO at Barnacle explaining all. It’s quite entertaining, so worth a watch:
If you park improperly, expect to be clamped and have a fine to pay. However, some students in Oklahoma became enraged by this and started looking at ways to remove the clamp without damaging it or the vehicle.
We were intrigued when we saw that a Reddit user had claimed to have removed a SIM card from the unit and used it to obtain free cellular data!
Clearly, the device uses an API and cellular data connection, probably a mobile app too. Right up our street!
One Friday afternoon in January this year, some of our IoT team spent just 90 minutes looking at the API and cloud servers. However, we were very limited in what we could do, ensuring we stayed on the right side of the CMA.
Did we find any interesting issues? Ooh yes!
So what did we discover?
The service has a dashboard at https://dashboard.barnacleparking.com which references several API endpoints, including https://api.brncl.be/api
Now, those endpoints didn’t seem to be very stable: simply refreshing https://api.brncl.be/.forward 10 times dumped their entire environment including S3, Dynamo, and SES keys. We’ve redacted them obviously:
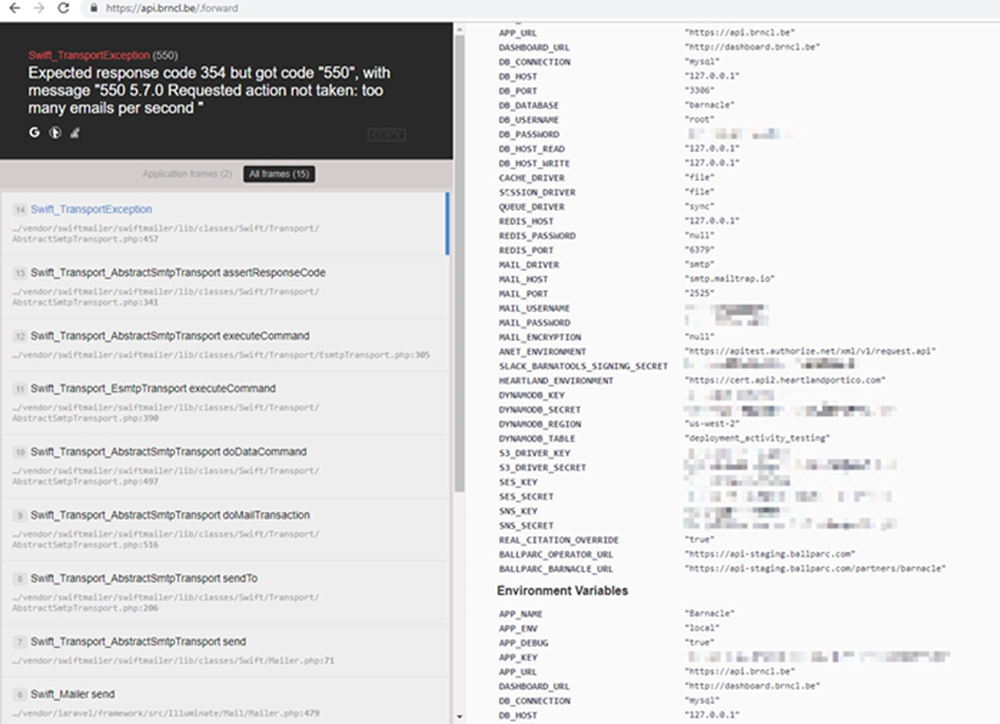
Wow!
So complete system compromise would have been possible at that point. Control of all clamps, leakage of all user data. I’m amazed that no-one else spotted this, given the interest in the system by a large number of students.
Fortunately we appear to have found it before anyone else, so reported it to Barnacle fast, who fixed it promptly.
But there’s more
Amazingly, the payment gateway accepted test credit card numbers, so unlock commands could be generated for free
There’s also a lovely IDOR: https://pay.barnacleparking.com/api/bms/xxxxx where xxxxx is the serial number shown on the Barnacle itself.
Using this, one could find all locked cars, their licence plates and vehicle model.
Whilst the API endpoint issues were fixed, the S3 bucket itself was open and world-readable for a while
https://barnacle-media.s3.amazonaws.com/ was readable, which contained data, helpfully indexed by Google.
Whilst the root no longer lists the content, files are accessible directly. The user manual is a lesson in keeping things succinct 😃
Disclosure
We emailed Kevin at Barnacle, asking if we could disclose the vulnerabilities to him direct on 17th Jan 2020. We didn’t get a reply.
Chris Fox of the BBC Tech Desk covered the original story which got our attention. It was clear from the story that he had had contact with Barnacle. Given the radio silence, I asked Chris if he could introduce us to Kevin.
Chris kindly sent an intro email, to which we had a reply within a few hours. It’s interesting how involving a journalist gets a response…
A word of caution here: We find that journalists respect responsible disclosure processes, but always make sure that you have their commitment first before you share anything!
Anyway, the API issues were quickly fixed, so kudos to Barnacle for taking quick action. We had a nice email thanking us for the findings on the 24th Jan, but silence since.
We tried Kevin at Barnacle by email again on 1st April and again on the 9th. Here we are, 4 months on and not everything has been fixed.
The files in the S3 bucket are still readable, but the data in there isn’t desperately sensitive.
The IDOR is still present. Fortunately there isn’t much one can do with either vulnerability, but it would have been nice to have seen them resolved, particularly after such a speedy fix to the API.














