TL;DR
- Network-wide collection, acquisition and monitoring tool for use in DFIR engagements
- Designed for enterprise networks (150k+ Deployments aren’t unheard of)
- Boasts many features that your commercial EDR has, and a few more
- Flexible querying language that can adapt to new threats and encourages community creation
- Allow DFIR Responders to act quick and leverage forensic analysis over an entire network to halt attackers in their tracks
Introduction
Velociraptor is an open source and free-to-use Digital Forensics tool from Rapid7. It can be used to assist in the collection, analysis and monitoring on Windows, Linux and Mac systems. It is designed to handle large-scale deployments, making it suitable for enterprise networks.
Essentially, Velociraptor provides precision optics in a minefield. You can have sight of an entire stack of endpoints and cut through all the noise to find the single malicious process on a handful of malicious endpoints, all in a matter of commands. To do this manually, using traditional digital forensics methods just isn’t possible when you’re under an active breach. Velociraptor is far quicker at getting answers, and honestly, it’s easier.
It is fast to roll out and is bolstered by an active community that contribute to a growing repository of EDR features and current threat hunts.
In this post we give on overview of some of the capabilities of Velociraptor, and also how we have leveraged them to conduct some real-time threat hunting shedding light on how it can equip security teams to proactively safeguard digital environments.
Overview
A key objective of Velociraptor is to incorporate DFIR knowledge right into the platform, so you don’t need to be an expert in Blue Team operations to make use of the core functionality. Velociraptor has routines baked in that can answer high level queries without much knowledge of the platform.
It can provide great file-system level visibility over every endpoint in the network, giving a wide-array of capabilities.
Once deployed it can obtain key forensic artefacts across the network or perform remote disk acquisitions where we suspect a compromised host. But it is also a sensible idea to consider using it as a proactive measure.
Want to see what applications are running? In need of a way to collect event logs or sensitive files remotely? Want to see who is using a “my passwords.txt” file for all of your mission critical information? Simple queries in Velociraptor can give you answers in seconds.
It provides full filesystem access and the ability to retrieve files. Suffice it to say having this securely pre-deployed on your network (protected by suitable access-control) in the event of a ransomware or other malicious attack can give you a huge head start on detection and remediation.
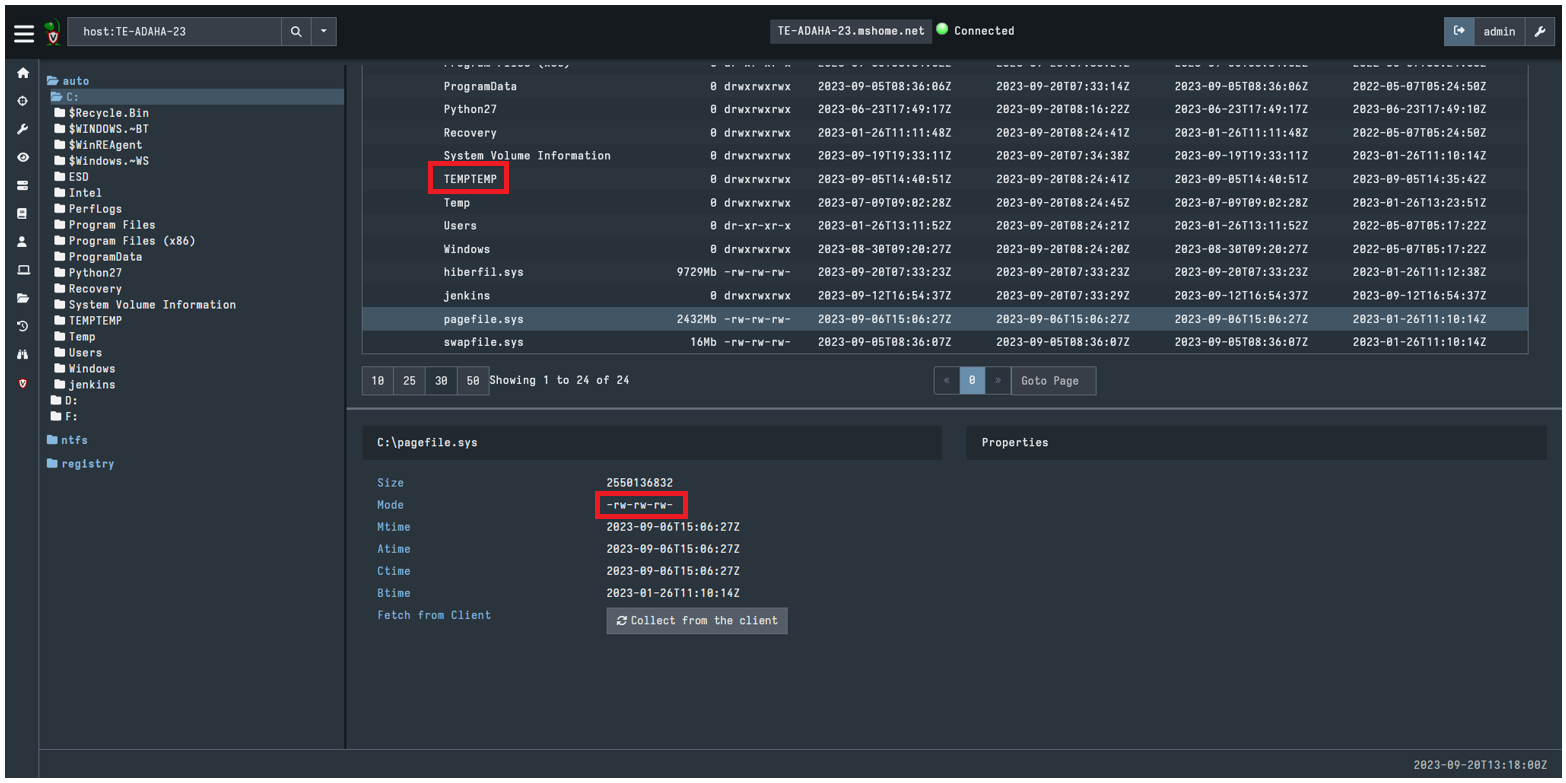
The platform comprises two parts, a server (hosted locally or in the cloud), and a series of clients that are deployed to the endpoints on the network – remarkably, it is the same binary file that can be setup to act as either, keeping things simple for a rapid deployment.
A single server instance can handle upward of 15 thousand clients. Any more than that and the scalable nature allows for a multi-frontend setup.
The server collects and records the results of queries. It is up to each client to “do the heavy lifting” and aggregate from all the potential data sources, though some would argue it would actually have a lower footprint than some of the big-name commercial Endpoint Detection and Response (EDR) suites.
Once the clients have been deployed across the network via a method of your choosing (for example Intune or GPO), the queries and threat hunting can begin.
Paleo-programming. The Velociraptor Query Language (VQL)
This is the real beauty of Velociraptor, and the secret behind its extensibility is the “Velociraptor Query Language” (VQL). It is central to the tool, and facilitates the collection of data from hosts, controls the monitoring and actions taken on them, and even manages the Velociraptor Server itself.
In the developers own words; “Velociraptor is simply a VQL engine”. This gives it its true power.
Created VQL queries are packaged in “Artifacts”, and Artifacts are what run over the clients (hosts) or Velociraptor server. Here are some examples to give you an idea:
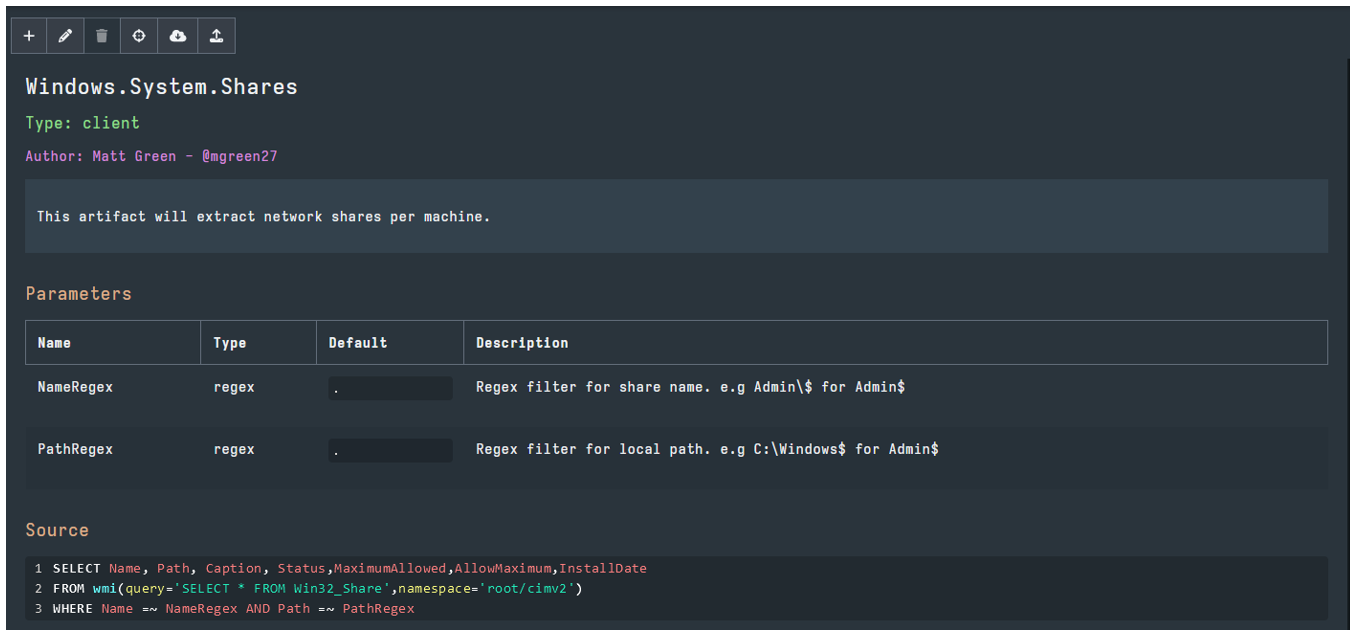
The artifact above has been created to list all system shares on a Windows OS. Note the raw VQL:
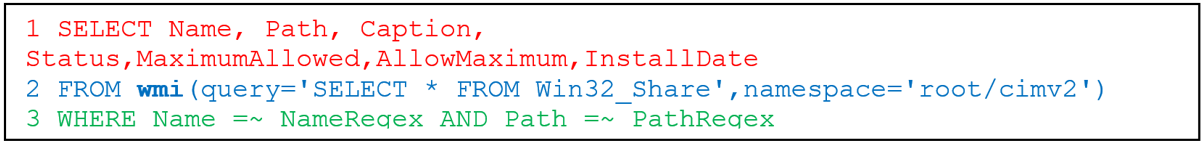
Or…
SELECT X, Y and Z FROM *WMI command to run* WHERE *Regex variables*
Or even more simply…
Give me the names and paths of all Windows System Shares, as provided by running this WMI command, where the share name includes the search term “Admin”.
This query can be run against a single host, sub-groups based on variables such as OS type, computer name, or the entire estate. AND it can be paired with other artifacts to almost automate an entire hunt and remediation sequence.
As I mentioned, even operations conducted on the Server alone are still orchestrated using VQL. The below VQL artifact is responsible for reporting on the details on a conducted Hunt:
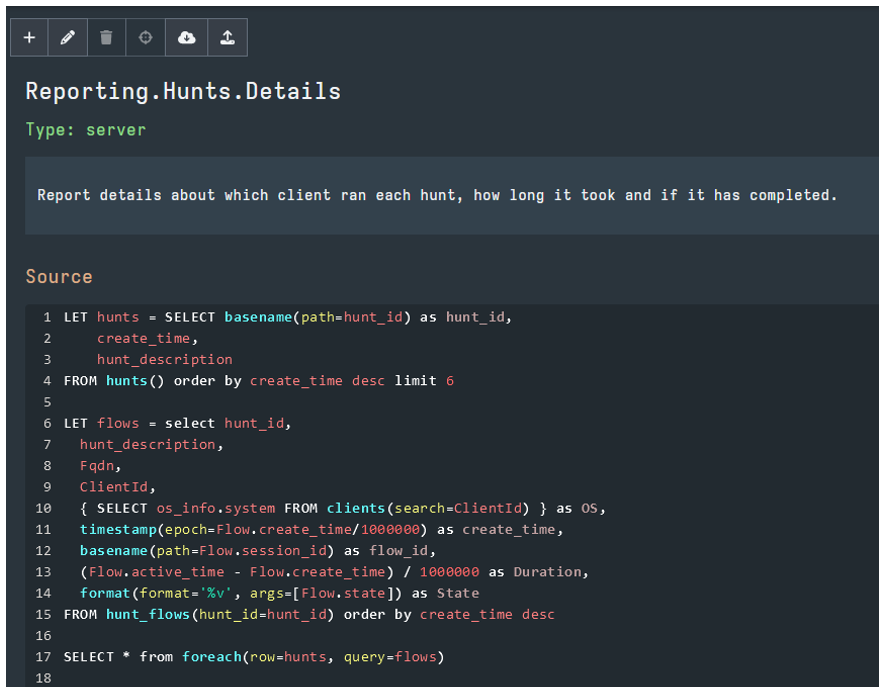
We won’t venture any more into trying to teach an entirely new language in a short blog post, but once the VQL fundamentals are mastered, the capabilities of Velociraptor in Incident Response scenarios becomes clear.
It’s this ability to create, amend and pair up queries into artifacts that keeps the tool at the forefront of DFIR, as artifacts can be constructed quickly to identify the IOCs of emerging threats or new Advanced Persistent Threat (APT) groups.
The team behind Velociraptor actually host an “Artifact Exchange”, allowing the sharing and dissemination of community developed artifacts for free.
Typical Velociraptor use cases:
- Endpoint file collection
- Custom scans across the network
- CVE / IOC impact Assessments
- Malware Hunting (YARA, SIGMA)
- Continuous monitoring and conditional detection alerts
- Forensic artefact sweeps (.EVTX, web history, registry / config files)
- Full Disk and Volatile memory forensic Imaging
- In-House Incident Response Platform – Ready. To. Go.
Introductory example. Network-wide forensic triage
This is probably Velociraptor’s most useful function.
We deal with a lot of CVE remediation. A recent DFIR engagement had us investigating a vulnerability caused by a supply chain attack in the popular video conferencing software suite 3CX. There were hiccups in the company’s vulnerability disclosure, and our clients were scrambling to determine how many hosts on their network were potentially vulnerable, and if so, were any under active exploitation?
There are 4 easy ways of quickly determining the presence of the 3CX Desktop on endpoints using forensic artefacts:
- File / Hash searches – Not bad. Not guaranteed to find all hosts.
- Process Memory – Searches for a live 3CXDesktopApp running on a system.
- AMCache – Gives evidence of process execution on a system.
- Yara rules – searches known install paths and applies YARA looking for binary attributes such as version numbers and the dodgy DLLs in question.
Using pre-constructed VQL artifacts; each of the above can be queried using the relevant Velociraptor artifacts across an entire estate in a matter of minutes, with the output of affected endpoints displayed nicely in a webUI.
What is even better, is that the Velociraptor community had already constructed an artifact to search and identify all of the above.
From there it was trivial for us to ‘label’ and group together the infected hosts for further queries, grab the volatile memory and pertinent log files to allow us to perform a deeper-dive examination on the boxes to see if they were under attack. This image shows Hunts and Monitoring Queries:
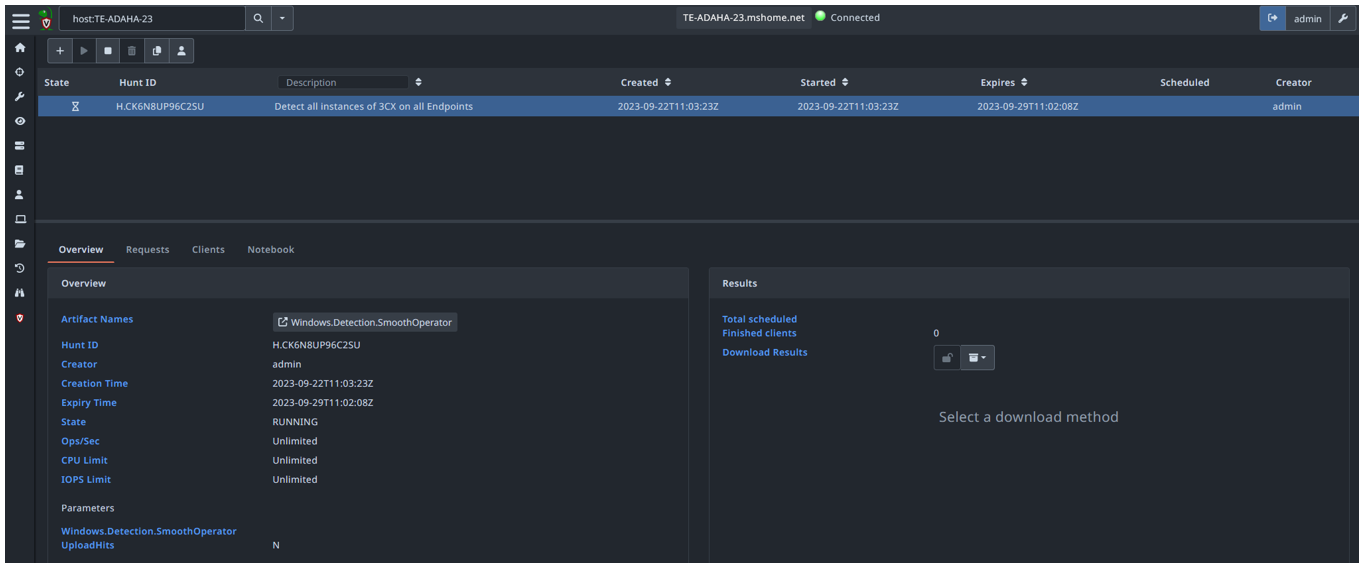
For a free tool Velociraptor offers some really neat features that even some EDR suites lack.
One that may be of interest is the ability to gain a shell (OS specific) into any host in question, allowing you to bypass the VQL and get direct access to a terminal (though Velociraptor implores that VQL should not limit you in any real way!)
It also gives you a “Host Quarantine” facility, altering local firewall rules on a host to deny all connections save for communication to the Velociraptor server. I should add here that there are caveats and limitations to this capability, but it is promising stuff.
If you’ve found yourself right in the middle of a breach, and a commercial EDR has not been deployed, Velociraptor can be used to give you eyes everywhere, and focus in on the malicious indicators. Some examples of the power it provides are given below…
Real-time incident response. Monitoring, detections and alerts.
This is really cool. A portion of the VQL language allows for the persistent monitoring of endpoints for, amongst others, changes is registry files, certain event log IDs, and Windows processes.
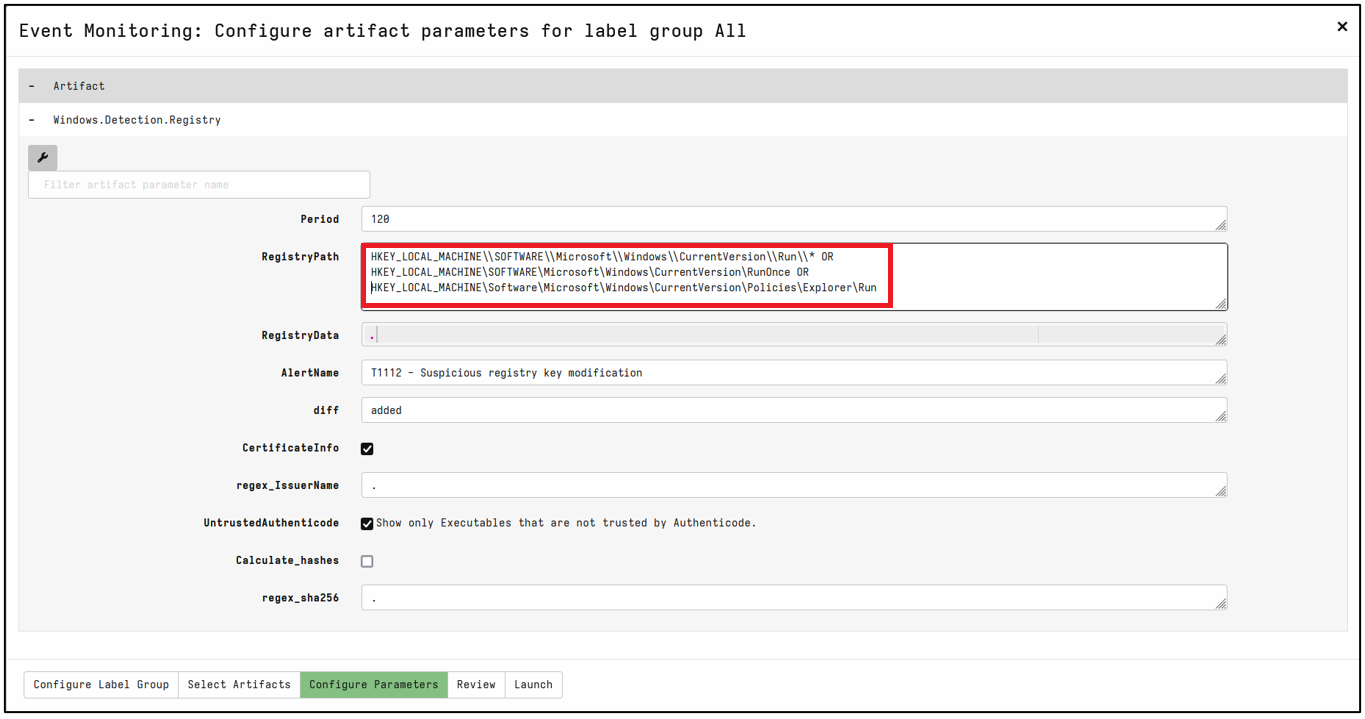
A simple check might be to identify persistence mechanisms in the form of changes to the Windows Registry. Of course, a simple query can be made to see other affected hosts, but by using the ‘Event Monitoring’ artifacts, this gives you oversight over any new hosts that may get popped further down the line. This image shows Detection Artifact creation for common registry locations for malware persistence:
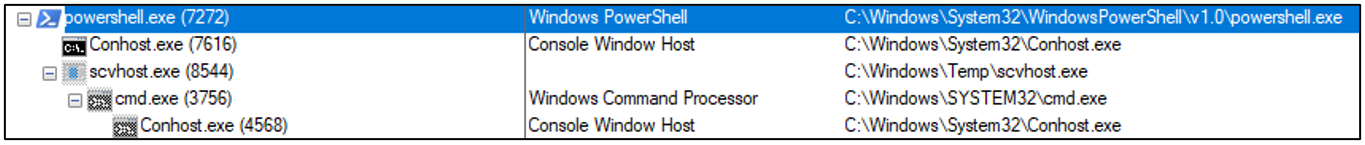
In almost any IR we deal with, the typical footprints will be lateral movement using something like PSExec, followed by a call out to a C2 server for the retrieval of a payload. And then finally the execution of a suspicious executable. This is usually apparent when viewing the compromised systems processes. This image shows scvhost!:
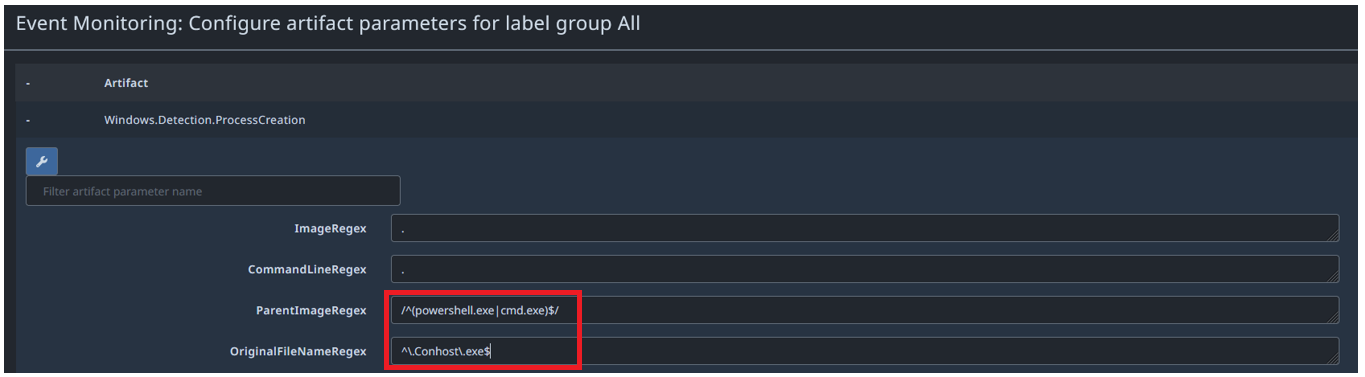
What we’d like to be able to do here, is monitor and detect the creation of, say, the creation of the Conhost.exe process, with a Powershell.exe parent. Not something that should be happening on an employee’s workstation without us being aware. Image showing PowerShell OR Command as the parent process:
Let’s go one further again and consider tracking Windows Event Log records. One of the most useful things I have found in IR investigations is the ability to map out, from a network perspective, the lateral movement over time. This gives you clues about what access levels a threat actor has, and what their exposure to your data they may have had.
Event ID 4624, logged in the Security Log records such movement by user account. You could, for example, create a monitoring artifact to track all 4624 events that contain the pattern “svc” (short for a service account) to detect the use of service accounts utilising RDP to move between computers.
Or monitor the same event but for any user, (except for a Break Glass Account) making an RDP connection onto any hosts with a “Domain Controller” label. We don’t want to see privileged Service Accounts hopping around using RDP:
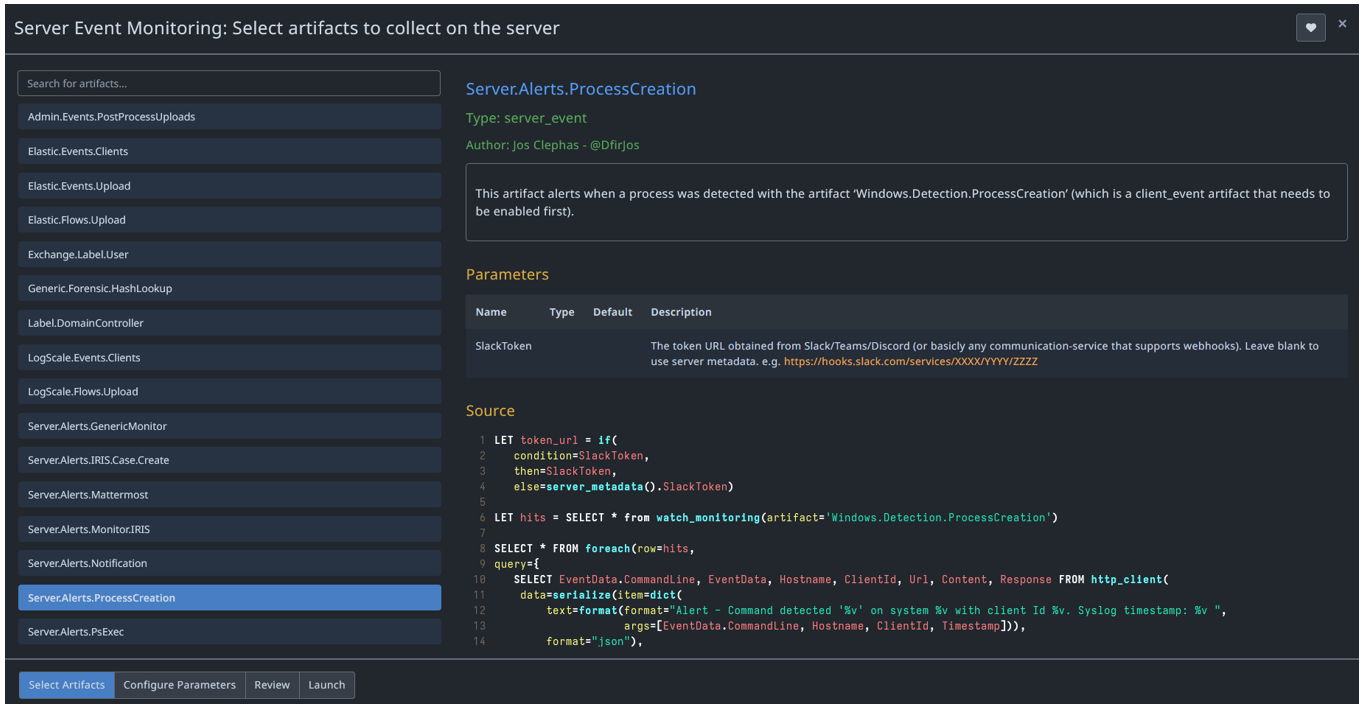
You can combine this with an ‘Alert’ artifact to monitor the detections server-side and notify you via Teams, Telegram, Slack, even Discord (basically any communications service that uses Webhooks).
Finally, to stop anyone in their tracks, configure the “Remediation Quarantine” artifact to kick in automatically as a result of the above detections, and lock the attackers out of the system.
IMAGE 10
What else can be tracked?
The following examples are already baked into Velociraptor for monitoring for changes, but in truth any detection you can think of can be implemented using VQL, for example:
- Service Creation
- PSExec Usage
- WMI Process Create events
- USB device usage
- DNS Queries
- Kerberoasting
Conclusion
Velociraptor has grown over the recent years to be a powerful DFIR platform, free of charge and with minimal setup. Its open-source nature and adaptable query language framework make it a valuable asset for organisations of any size.
It can be rolled out in minutes following a breach, or securely maintained as an endpoint monitoring tool for BAU tasks.
You can also make use of Velociraptor to conduct Compromise Assessments on networks that can’t use other EDR solutions. Or in sensitive locations where an airgap needs to be maintained, harnessing their offline collector tools.
You may already know, and it’s worth repeating, preparation and oversight of your network is vital if you want to get on top of a breach as quickly as possible. Having Velociraptor on tap will be immeasurably helpful in the golden hour of Incident Response.














