VTech recently settled a FTC case for $650,000. It related to the data breach in 2015 involving around 3 million kids details, users of the ‘Learning Lodge’ online application which interfaces with many of their smart devices.
We are particularly interested in hardware security, so I bought a brand new VTech Innotab Max just before Christmas to see if device security has improved.
TL;DR?
It hasn’t.
We found that we could compromise online accounts through the hardware, using hardware vulnerabilities known about for over 4 years.
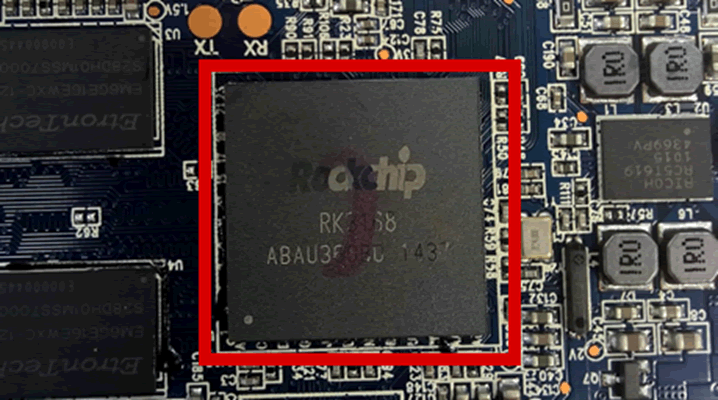
You may recall our work on the Tesco hudl version 1. It used the Rockchip RK3188, which has a flash mode flaw that permits extraction of arbitrary data.
Tesco promptly and responsibly replaced the product with the much more secure hudl2. That was in 2014!
I looked at the Innotab hardware in 2015. Guess what? It featured a related Rockchip CPU with an identical flaw
Here we are in 2018. VTech have been breached, fined and have stated that they take security seriously.
Fair enough, but what is the CPU that’s in the latest Innotab Max? You guessed it, they’re still specifying that vulnerable Rockchip:
Validating the flaw
For this we need rkfkashtool. It has been updated somewhat, so pull the latest version from https://github.com/neo-technologies/rkflashtool.
Kudos to the authors. One can now select a partition by name, making extraction a touch easier.
Getting in to bootloader mode
Connect a USB cable from your laptop running rkflashtool.
Press and hold down the power button for up to 10 seconds. We need the Innotab to be completely powered down.
Press ‘volume up’ and power together for around 3 seconds. Release power but not volume up.
Then release volume up.

Check that a device with the correct ID is attached to your image. The USB IDs for Rockchip are:
- 2207 – the vendor ID
- 300b – the device ID
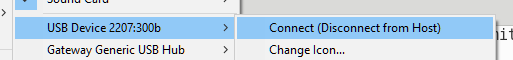
If not, repeat the power down process and repeat the above. It can be a little flaky, so persevere!
Then run the flash tool. You’ll get an image like this:
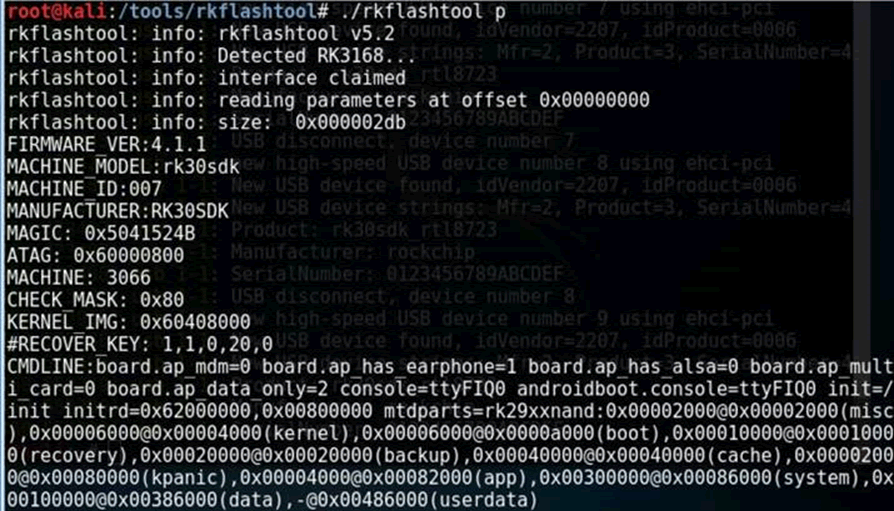
Now you can read the userdata partition, e.g.:
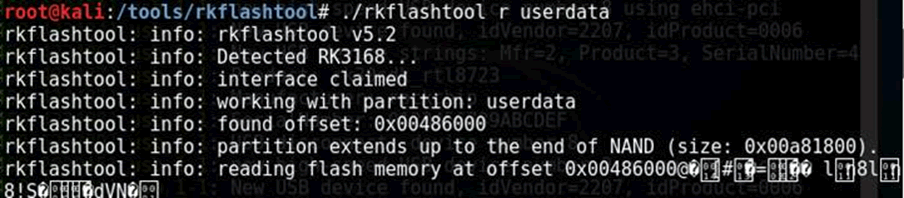
You can read it using hexdump too if you like.
…or you can strings it, but better to just mount it as a file system. Fortunately all the Android file systems we’ve seen are standard ext4. This means that they can easily be mounted under Linux using the loopback mounting facility.
But that’s not all!
There’s a microSD card on the motherboard. It was glued on, but that took seconds to prise off.
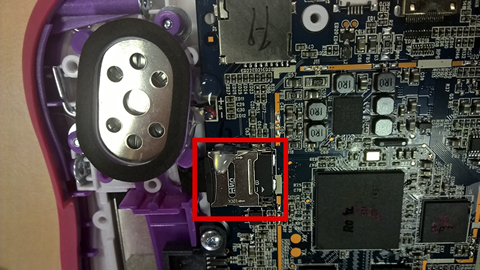
A quick read shows that it’s the filesystem and user data. Yes, really. On a removable SD card. Other than making for another easy route to extract sensitive data, that’s also asking for reliability trouble down the line.
Now we can potentially extract some useful data
E.g. extracting and cracking the device PIN as per the original hudl.
Also, WPA key extraction; just locate wpa_supplicant.conf in the filesystem.
Finally, we’ll be trying to extract the Learning Lodge credentials from the device next, so watch this space.
Conclusion
Are VTech just paying lip service to the FTC and customers? This doesn’t strike me as a kids product vendor that is taking security seriously.
Come on VTech, pull the Innotab Max from the market, update the firmware and provide a product with decent hardware security.














