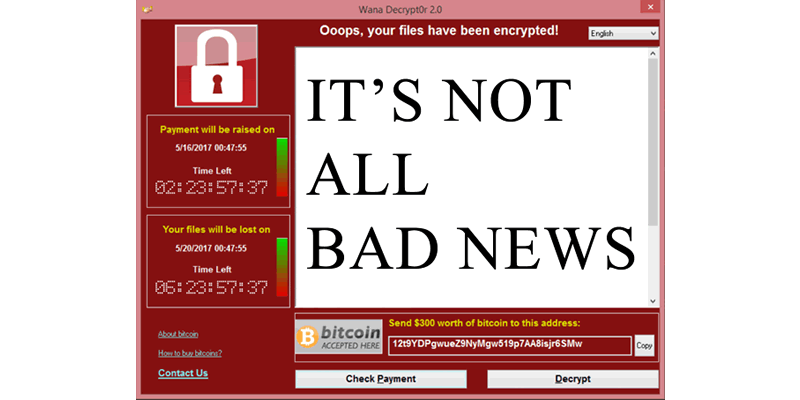
After all the press coverage, one would think the sky was falling in. Rather than regurgitate the same bad news as everyone else, let’s have a look at some of the good things that will come out of this incident.
It was only ransomware
It could have been used for exfiltration of data, yet it doesn’t appear to have been.
As a result, everyone is now patching MS17-010 and the chance of it being used for data theft is much reduced.
Yes, data was encrypted and it’s a royal pain for patients, the health service and business, but it doesn’t look like data was stolen.
Someone quipped on Twitter that ‘at least NHS patient data is now encrypted’.
It wasn’t targeted
The NHS infection was chance. Despite the rantings in the press, our health service wasn’t targeted.
The scammers didn’t understand the workings of the NHS so didn’t have the opportunity to make this incident a whole lot worse.
Imagine if the private NHS network, the N3, stopped operating completely…
Imagine if the core patient records systems were compromised, backups wiped and data taken.
WannaCry wasn’t great malware
The malware itself wasn’t great.
The kill-switch domain slowed down the spread of the malware very quickly. Why was this in there? Some suspect it was to detect sandboxes (as some sandboxes resolve all domains regardless).
The malware had little in the way of obfuscation or techniques to prevent reverse engineering, allowing many people to pick it apart quickly.
Had the malware been written well, then this incident could have been a great deal worse. What if it dropped a back door on every system it infected?
Above all, as it stands, even if you pay, you can’t decrypt your files. Word of this quickly spread, and has likely limited how much cash they will net from this.
As of now, the BTC wallets contain only about $50K but you can keep tabs on the values here:
https://twitter.com/actual_ransom
Image source yle.fi
Microsoft have supported an unsupported operating system!
There is now even a patch for the unsupported XP, 2003 and Windows 8 (vs 8.1) OSes.
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ as well as the supported ones https://technet.microsoft.com/en-us/library/security/ms17-010.aspx.
That’s great news – clearly when the issues are bad enough, MS will help. That shouldn’t be relied upon though; it’s no excuse not to patch and upgrade.
MalwareTechBlog crippled WannaCry early
Without this awesome researcher registering the domain and stopping the malware, this could have been a whole lot worse. We owe him and many other researchers a debt of gratitude.
Might be nice if the UK government actually recognised this in some way. The guy deserves a medal, pizza, and a lot of beer!
Backups, upgrades and patching will improve
Probably the easiest and quickest way to recover from ransomware (other than paying the ransom!) is to roll back to an earlier clean backup. (Do not expose it to the network until it’s patched, or you might be doing the same thing again in a few minutes).
Yeah, you’ve got backups, right?
Everyone has an incentive to ensure their backups are frequent and effective. WannaCry will help this happen and get traction at Board level.
Consumers and businesses get a massive wake up call to prioritise patching. Now the IT security manager can finally go ‘this is why we told you that patching was important’.
Hopefully Boards will now properly fund patching activity and software upgrade programmes.
Government will now have to take patching and software upgrades more seriously. Their IT service delivery partners will be pressured to actually do the job they’re being paid to do. Some government sources stated that they ‘asked the NHS to get the patching in order’ – but that’s not enough – one needs evidence to prove it’s been done.
“We’re spending around £50m on the NHS cyber systems to improve their security. We have encouraged NHS trusts to reduce their exposure to the weakest system, the Windows XP.”
Fewer than 5% of the trusts used XP now, [Fallon] said.
“We want them to use modern systems that are better protected.”
“We warned them, and they were warned again in the spring. They were warned again of the threats.”
I’m sure every pen tester out there has been back to a client (both government and business) a year down the line after a test. Nothing has been done – one might as well have changed the date on the last test report and handed it back to them. Will this be the stick that ensures this doesn’t happen again?
Will spy agencies start being more careful about hoarding exploits? It’s so tempting to keep zero days to oneself, yet they will leak eventually. The NSA deserved the rap they received from Microsoft.
Will embedded software in complex medical devices be supported for longer? Perhaps; there’s a greater chance of this if buyers mandate extended software support as a result of the WannaCry issue.
Now is also the time to start thinking about how to segment the network so that ransomware can’t spread freely through computers and network shares, as well as working out how to get visibility and control over any future network worms.
Will WannaCry be the impetus that gets the business to fund that segregation project you’ve been banging on about for years?
Advice
If you are infected this post from BleepingComputer will help:
https://www.bleepingcomputer.com/virus-removal/remove-wannacry-wana-decryptor-ransomware
There is also this from NVISO Labs, on Corporate sinkholing – set your DNS servers to return an internal server when the machine asks for the C2 domain and make sure the internal sinkhole server has a functional webserver:
https://blog.nviso.be/2017/05/15/wcry-ransomware-additional-analysis/
Conclusion
I’m in no way trying to downplay the whole thing. It is expensive, disruptive, and stressful for many, many people.
If you want doom and gloom about WannaCry there is plenty out there, but there is also a silver lining of sorts.
Sadly, it’s often only events of this magnitude that prompt the behavioural changes that we’ve been going on about for years.
What worries me is that, in a weeks time when the press coverage has died down, business and government will settle back in to their old, bad ways.