Introduction
We’ve written about the appalling security of smart sex toys over the years. Finally, an invite came to give a talk on the subject to a TEDx audience.
I debated whether to give the talk with colleagues, as we’ve never wanted to be pigeon-holed in this space! But we felt that public awareness of the lax security was one of the ways to encourage the toy manufacturers to improve.
Issues such as precise position leakage of LGBT+ people in countries where they were persecuted by authorities were simply too concerning.
Unfortunately, perhaps predictably, YouTube made the talk video age-restricted so you’ll need to sign-in to watch it. We think this is the first ever TED talk to be age-restricted 😊 I’ve written up the script of the talk here for you, should you prefer not to watch the video.
The talk script
I’ve often been shocked how poor the security of smart devices is. A few years ago we looked at a smart, interactive talking kids dolly. We discovered that it could be used as an audio spy bug and could also be hacked to then swear at children.
More recently, we discovered the area of smart sex toys. Many of us don’t feel comfortable talking publicly about such private and intimate matters. Partly because of this, I believe that smart adult toy manufacturers are not properly held to account for poor cyber security of their products. That’s why I think we need to talk about this subject.
But I did discover that buying smart kids dolls and smart sex toys gets you some very weird online shopping recommendations!
Teledildonics
So let’s talk Teledildonics. This isn’t a new term. It was coined nearly 50 years ago by a guy called Ted Nelson, a pioneer of IT systems. He’s much better known for a more familiar term: he came up with ‘hypertext’ – you use it every day on the internet http: hypertext transfer protocol.
Now Teledildonics describes virtual or remote sex interactions. One example might be a couple who are separated by a significant distance, perhaps during the pandemic lockdowns. At one end is one smart device and a smart phone.
At the other end is another smart device and another smart phone. One can control the others device and interact with audio, video and chat. The two smartphones apps do all the work, communicating via the manufacturers systems.
You might be surprised to know that these smart sex toys are remarkably popular. Sales grew hugely during the pandemic as people who love each other were separated. But there are many markets and uses, including online parties, camera modelling, products that are particularly for LGBT+ markets and many others. All users of these sex toys are entitled to security and privacy by default.
What about privacy?
I think the single biggest cyber security problem is that of the users location. Many of these apps leak the precise GPS location of the user, right down to the room in a house.
Some leak it deliberately, in order to allow users to find others nearby. Others leak the location accidentally, through really bad security.
Why does location matter? Remember I talked about people separated by lockdowns? One of the most popular markets for these sex toys is in the military. People who love each other could be separated for months at a time as one of them is posted overseas on military service.
Relationships have undoubtedly been saved by the ability to maintain an intimate relationship whilst half way around the world. So we are accidentally leaking GPS location of military personnel on active service. We also have the potential to extort the same personnel.
Remember the Strava heat map that unintentionally revealed the location of military bases and running routes of service personnel? Location data can be important.
Genuine personal danger
But it gets worse. Some adult toys appeal particularly to gay men. Some of these toys leak their location too.
Yet, here is real data that my colleagues discovered, showing precise location data of device users. Location data that could expose them to abuse, arrest or torture. This is horrifying.
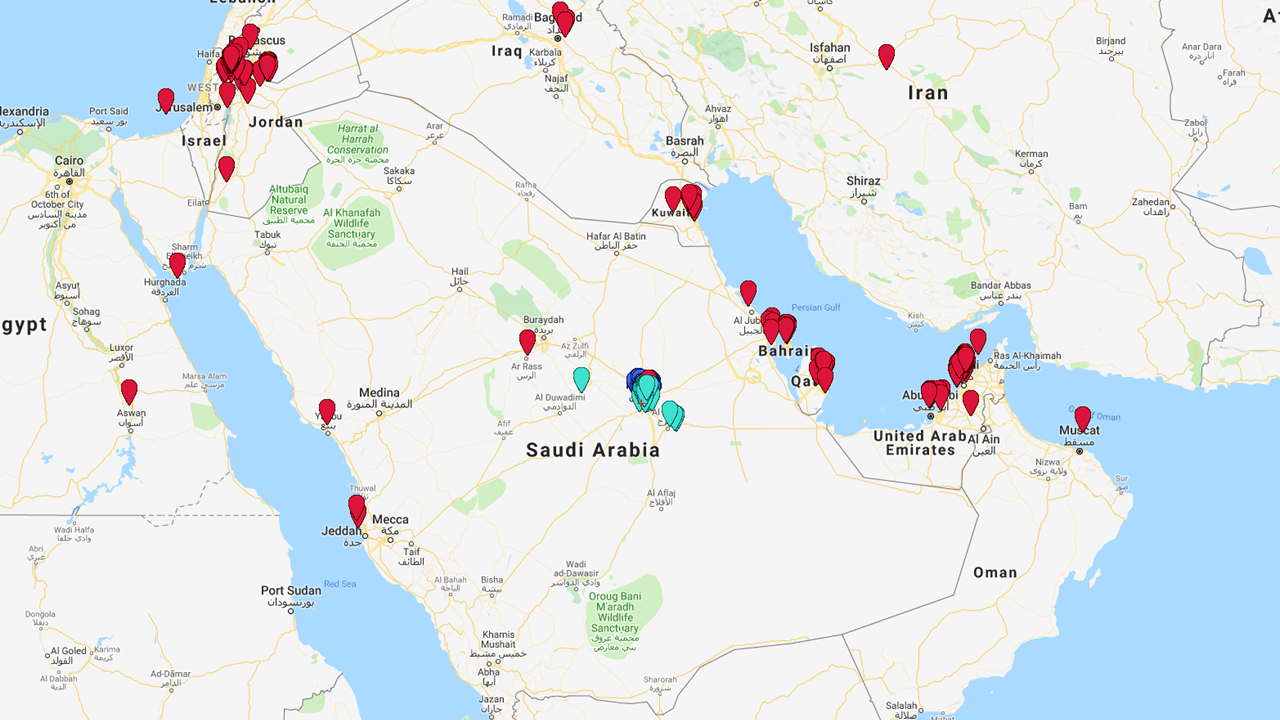
Fortunately, some of the issues that led to this have now been fixed, but not all.
The next problem is what we call ‘advertising’ data. I don’t mean advertising commercials, it’s a technical term with Bluetooth. First let’s look at one sex toy that uses Wi-Fi.

This toy is now switched on. If you all get our your mobile phones and open the Wi-Fi settings, some of you should see Siime Eye in the list, like the image on the screen.
Now you know that I’ve got a sex toy over here. You even know what sex toy it is, just by it’s Wi-Fi name. We’re going to come back to this sex toy.
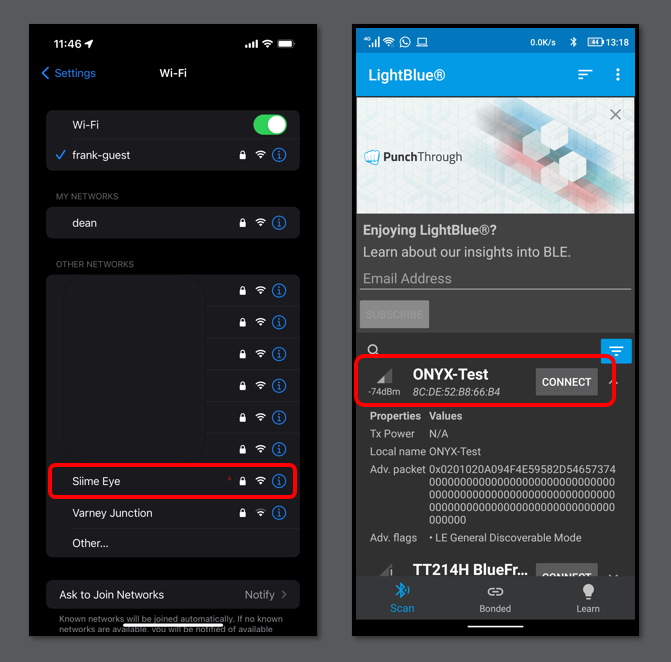
There’s a similar issue with Bluetooth sex toys. Using an Android app called LightBlue which just looks for Bluetooth data from any device, you can see all sorts of sex toys.
So what? If you know what you’re looking for, you can see that your neighbour is using a smart butt plug.
Just by being within say 20-30 metres, you can see what your neighbours are up to.
It gets worse though. It’s not just location data. Some apps leak more than that.
Your photographs
Here’s an example of a hookup app. You can see that the app leaks very personal information and …. photographs. This is the most suitable photo we could find!
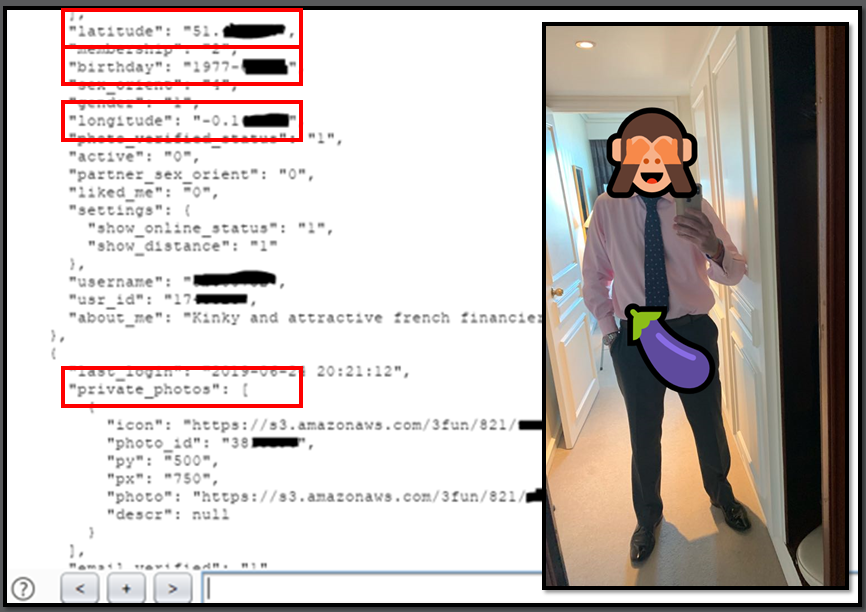
The security and privacy controls are terrible. Consider how easy it would be to extort or ransom someone
The photo problem gets worse though
Here are two words I never thought I would see together: Vibrator endoscope. This is the toy you saw on Wi-Fi just now. It’s a vibrator with a camera in the end of it.
Amazingly, the Wi-Fi password is 88888888. You probably know that 8 is a lucky number in China. It can’t be changed.
That means anyone nearby can connect… at the same time as you are using it…. and connect to the camera and see what you are doing.
We looked further at this toy to find out why its security was so bad. We looked at the code running on the chips inside it. We were a bit surprised to find that it had code for controlling propellers.
Cheap code
It turned out that the vibrator manufacturer had re-used code for a camera drone toy.
Why? Because it was cheaper than writing new code. Privacy and security isn’t important for a drone. Who cares if you can see the camera. But privacy is a whole lot more important for a vibrator camera.
There are also issues around hijacking these sex toys. This isn’t as concerning to me, as one could simply stop using the device if it starts behaving oddly.
But for men, there is potential to become stuck.
Another cool researcher found some issues with the smart butt plug. He discovered that he could change the code running on it. For example, it may be possible to cause the battery to overheat, whilst it was in your butt.
Smart chastity device
The final issue I want to talk about is a male chastity device. The idea is that one can clamp the device on to your manhood and electronically lock it in place using a mobile app.
Where it becomes a chastity device is that one can send the digital unlock key to someone else with the app. Now, only they have the ability to release you.
What we discovered was a security flaw that meant we could prevent anyone from unlocking anyone else. The wearer became locked in and couldn’t release themselves.

That’s a hardened steel clamp, so the only way to release yourself was to stick a large screwdriver in to the device and lever it off, whilst clamped in.
Eventually, the manufacturer listened to us, but only after we involved the media. They finally fixed some of the faulty code. The seemed more interested in releasing a version 2 that includes the ability to give the wearer an electric shock!
We need to stop laughing
“We need to stop laughing”. These aren’t my words, they’re the words of an awesome security researcher who goes by the handle Render Man. You can find him on Twitter @ihackedwhat.
We laugh because we are so surprised by these unusual sex toys and so surprised by the way that some are used. Some kinks and fetishes aren’t familiar to some of us, so we are surprised and a natural reaction is to laugh. But every user of every sex toy is entitled to privacy and security, so laughing doesn’t really help anyone.
Renderman runs a web site called the internet of dongs and gives great advice to sex toy manufacturers. Unfortunately not all listen to him and there aren’t enough researchers who are prepared to spend time in this rather niche, but rather sensitive area of smart devices.
Several of my colleagues do great work in this space, as do a small number of other cool researchers.
There is hope
There is a little hope. There are laws emerging that cover all smart devices and mandate some basic cyber security standards. Unfortunately, we need to talk about the problems for lawmakers to pay attention. We need to complain about poor security if laws are to be enforced. Which means we need to be prepared to talk about sex toys.
My hope is that by me talking about sex toys and cyber security, you might talk to your friends about sex toys and cyber security. And they might talk to their friends. Maybe talk about some of the issues I’ve talked about today.
By talking about it we draw attention to the poor cyber security of smart sex toys. Attention will help make things better. We can ensure that we get security and privacy by default.














