You’ll already know that we have a keen interest in smart home camera security. Our recent work on Swann and FLIR cameras showed how it could be trivially easy to spy on people through their security cameras.
Which? Magazine has a well-earned reputation for providing product reviews for consumers. It’s ‘Best Buy’ recommendations are highly sought after by consumer goods manufacturers.
Which? has also started reviewing smart consumer electronic devices. They recently published an update to their smart home security cameras.
We were therefore shocked to see that their number 1 recommendation was for a camera with SECURITY FLAWS involving video feed compromise.
Yes, Which? Magazine have recommended a smart camera that allows their readers to be spied on
Here’s an extract from the review:
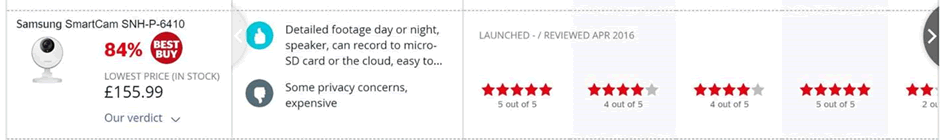
“Some privacy concerns”? Really??
The scores are based on ease of use etc, but also on privacy. As far as we can make out, the privacy evaluation criteria are partly to check whether communications between camera/mobile and app/server are encrypted.
That’s simply not enough to assure security. Just having HTTPS in place doesn’t provide security, it’s only a start.
We’ve shown on many cameras how a lack of authorisation can lead to access to peoples video feeds. The Swann and FLIR cameras that we switched video feeds on had encrypted communications, yet we could still access peoples video.
What’s worse is that these security flaws have been known about for some time
We’ve tested this Samsung SmartCam camera several times for various different organisations, going back to 2015. Obviously, client engagements are covered by non-disclosure agreements, however we worked with each client to report the findings responsibly to Samsung (Hanwha Techwin is the actual manufacturer) for remediation to be carried out.
So, we knew about the issues but had to remain silent for contractual reasons.
In August 2016, command injection vulnerabilities were published for this camera.
More vulnerabilities were published in January 2017.
Then, in April 2018, Kaspersky published a report into the security of …. the SmartCam SNH-P-6410.
This is the report: https://threatpost.com/security-camera-found-riddled-with-bugs/130335/
We expected better of Which? Magazine. Surely, during research for an important review that includes security analysis, someone thought to check online to see if any significant security flaws had been released since the last review?
Simply searching “Samsung Smartcam Security” reveals pages of coverage about vulnerabilities in this exact camera.
What made this even worse was that Which? made a big deal of a single plain text request from the Hive smart camera https://www.which.co.uk/news/2018/08/hive-updates-its-wireless-security-camera-following-which-security-concerns/ – this wasn’t ideal, but to exploit it would require first compromising the users Wi-Fi network, but even then the only data exposed was the users email address.
Yet, they made a ‘Best Buy’ recommendation for the Samsung camera, whose video feed could be accessed by anyone, among numerous security flaws.
There are more vulnerabilities too, still unfixed!
The cameras are still vulnerable to a de-authentication and evil twin attack. Hence, anyone in wi-fi range can access the users video feeds. Nosey neighbour or local stalker?
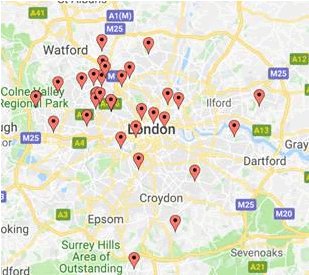
Here are the locations of a few of the thousands of these cameras in the UK, easily found using the war driving database at https://wigle.net
The cameras also have terrible local network security, so if one cracks the users Wi-Fi PSK or has local access, it’s possible to completely compromise the camera. Command injection, total pwnage
…and a few muppets have put their cameras on the public internet: https://www.shodan.io/search?query=iPolis
Why did this happen?
Evaluating the security of smart consumer products is complex: it requires time and expertise.
I can see why Which? may have restricted their privacy evaluation to checking for unencrypted communications, but it simply isn’t a deep enough evaluation to make an informed recommendation to consumers.
Which? either need to significantly upgrade the depth of security testing, or stop making recommendations in the smart consumer product space.
Which? have been involved in the DCMS ‘Secure by Design’ guidance for making smart products secure, yet they haven’t even followed the draft guidance for their own product security review.
How embarrassing.














