WhosHere Plus is a dating app that uses GPS data to recommend users near to each other, based on similar interests.
PTP constantly researches the state of privacy and security in apps that use GPS data, because the consequences of poor security and privacy are alarming:
- Tracking and snooping on a million kids
- Dating apps that track users from home to work and everywhere in-between
- Group sex app leaks locations, pics and personal details. Identifies users in White House and Supreme Court
- Limiting your exposure to location data resellers
Sadly for WhosHere Plus users it’s no exception.
In April last year BBC Middle East contacted us. They were investigating allegations that the Egyptian police target and persecute LGBTQ+ people using dating apps including WhosHere Plus. The BBC are familiar with our work on trilateration in other dating apps and wondered whether WhosHere might be similarly open to abuse.
There are two versions of the app, WhosHere and WhosHere Plus. Finding the trilateration issue in the first was difficult due to the unusual way it transmitted location data. WhosHere Plus however uses straightforward latitude and longitude co-ordinates, making it far easier to exploit.
Once we’d proved the failings of the app to the BBC they approached the vendor to begin the disclosure process, and encourage them to fix the issues that allowed users to be accurately geolocated. WhosHere’s initial response was appalling (and we’ve seen a fair few strange vendor responses):
“
…my first reaction is to use a technical term ‘bu******’
“
So, let’s dig into how the app works and how it can be abused.
Leaky locations
The app geolocates the device when it’s launched and establishes its location with an API request. This is stored on WhosHere’s servers:
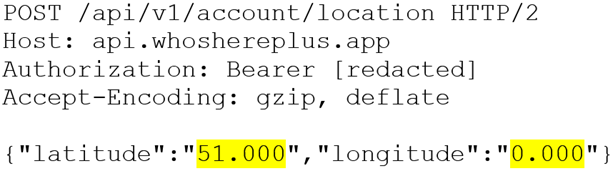
Another request then retrieves the details of nearby users:

The distances of nearby users are returned to two decimal places, or 10 metres.
Trilateration in action
We created our own WhosHere Plus accounts to see if we could determine user locations to around 10 metres.
By sending three sets of latitude and longitude data to /api/v1/account/location we can discover the distance to a target user. Here’s some redacted examples:
x.086022, y.183845 = 14.8
x.068566, y.053801 = 18.3
x.041151, y.064933 = 5.1
These co-ordinates can now be used to estimate the location of a target user.
The API request to /api/v1/search/online gives up other data:
- FriendCode (used internally by the Name)
- Name
- Description
- Age
- Gender
- Photograph
- Last Online timer
This all goes to show that WhosHere Plus is indeed leaking data, and critically for a targeted user, location data.
‘Sort of’ protective measures
WhosHere have provided basic mitigations to the problems. The effectiveness of all of them is limited though:
- Certificate pinning was added to the app after August 2022. This validates certificates presented by a server against an expected list. It makes app data more resilient to interception but can be bypassed on individual devices.
- There is an “approximate location” feature in later iOS and Android versions, but it can’t be relied on as it may not be available to every user.
- Redacting or rounding distances is a partial solution. Because inferences can be made through list ordering and other techniques it’s not effective.
Disclosure timeline
- 26th April 2022: BBC contacted us with concerns that Egyptian police had been using WhosHere to target LBGT+ people.
- 27th April 2022: After looking at the API, we suspect that trilateration is possible
- 3rd May 2022: we film our concerns with the BBC. They confirm that they will contact WhosHere to discuss.
- 8th June 2022: BBC alert us to an updated version of the app, WhosHere Plus.
- 23th June 2022: We conclude research on the latest version of WhosHere Plus, confirming that the API is still vulnerable to trilateration.
- Early December 2022: BBC discloses issues to WhosHere. Vendor responds saying ” …my first reaction is to use a technical term ‘bu******’ “.
- 20th December 2022: BBC complete filming the wider show, we review latest update which features certificate pinning, but is still vulnerable to trilateration.
- 30th January 2023: BBC publishes the findings, highlighting security issues in WhosHere Plus, as part of a much larger story about persecution of LGBTQ+ people in Egypt.
Why are we publishing now? This was going to be part of a series of content to present at Queercon in August, but sadly they’re not running any talks this year.
Conclusion
Handling location data, especially in dating apps, needs to be undertaken with care. Many designers fail to consider the threat model of vulnerable groups when designing their products.
Although end users can do much to protect themselves, it should not be on the user to do this.
App makers should be more transparent about how they store and manage the risks of location data in their products, incorporating security-by-design to defend against both external and insider threats.
The BBC documentary and accompanying article are here:














