We’ve looked at smart Xmas lights before; whilst they were vulnerable, there was no consequence to the hack other than making them flash in a different order!
In 2018 we looked at the all-new Twinkly smart festive lights. We found a number of security issues, reported them to the vendor and to a large retailer who stocked the lights.
Whilst the vendor ignored us, the retailer was actually very supportive: they demanded that the vendor fix the issue and, when they failed to, delisted the product.
However, it seems that the vendor has finally listened: version two of the smart lights that arrived on my desk last week now uses a much more secure System-on-Chip.
The lights
Twinkly branded lights are the product of a Kickstarter campaign from 2016. The game changer is that the phone camera can be used by the mobile app to program individual lights.

It’s easy to program cool moving designs and much more.
Nice!
Hacking your home network through your Xmas lights
Version one of the smart lights could easily be connected to your home Wi-Fi network. In order to do that, the lights needed your Wi-Fi key.
We dismantled the control box for the lights and found an ESP8266 Wi-Fi module.
Now, we know this module well from our research in to the iKettle 2.0 from a couple of years ago. The ESP8266 is a bit of a fail for IoT – it has no trusted execution environment, no secure key storage, basically no significant security features at all.
Much more secure modules were available at the time, but I guess the Twinkly team chose the cheap option.
The waterproof control modules for outdoor lights are usually…. outdoors. Hence, a passing hacker can open the control module, attach a couple of logic probes and could recover the Wi-Fi PSK key from the Xmas lights.
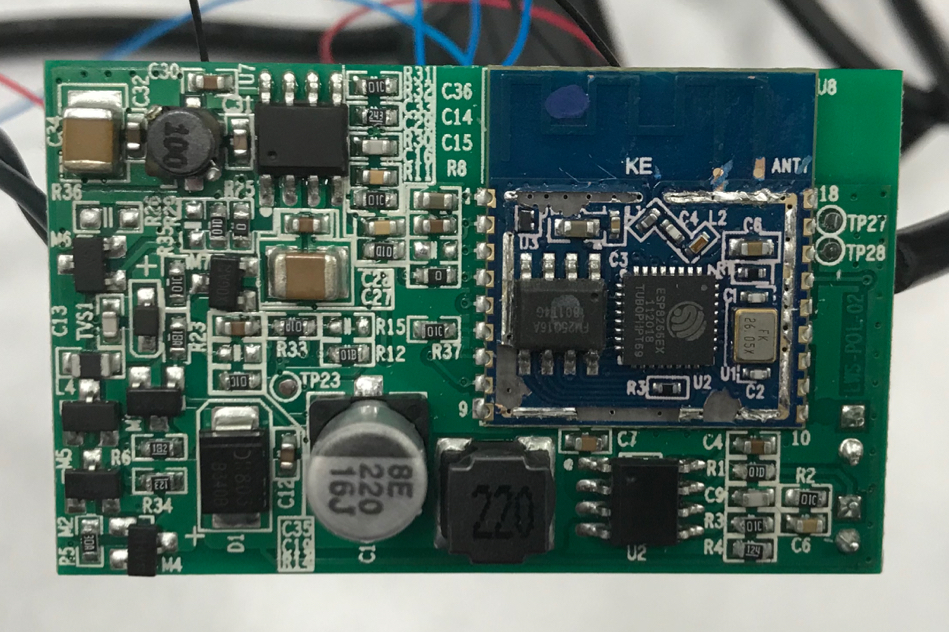
We achieved that in a couple of minutes.
Oh, and it was easy to find homes with these lights installed: the ‘wigle’ war driving database lists numerous sets, which will no doubt increase dramatically over the holiday season.
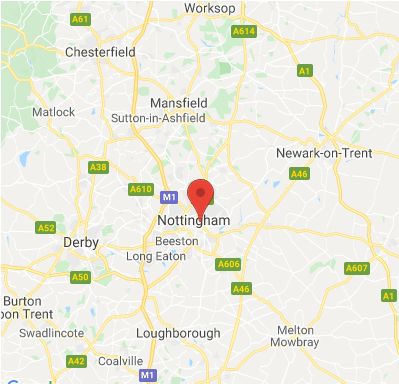
https://wigle.net/search?ssidlike=Twinkly%25 – note that you’ll need a free account in order to run this query.
That’s not all
During the process of initial connection of the lights to your home network, the PSK key was sent over the air.
You would hope that it was strongly encrypted, wouldn’t you…
Sadly not. It used RC4 with the Wi-Fi MAC address as the key. Trivially cracked.
It’s 2019, what changed?
Anyone would think that the vendor, LEDWORKS, had read our blog at the time, where we suggested that the ESP32 was a much more secure module than the ESP8266.
So imagine my surprise when @cybergibbons opened up the control box:
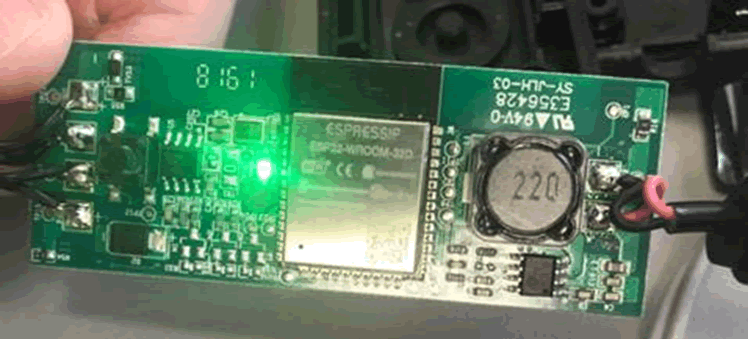
Now the ESP32 isn’t perfect (e.g. https://limitedresults.com/2019/11/pwn-the-esp32-forever-flash-encryption-and-sec-boot-keys-extraction/) but it does raise the bar somewhat over the ESP8266.
Conclusion
This is progress. Baby steps, but progress in the right direction.
The retailer involved has now relisted the lights, which shows that commercial pressure on manufacturers can generate results for consumers.
In future, it would be wonderful to see more manufacturers following basic security guidelines & more retailers refusing to stock products that don’t comply.
In the UK we have the Department for Culture, Media and Sports ‘Secure by Design’ Code of Practice for Consumer IoT Security that details simple security requirements. I recommend that all smart product manufacturers read this!














