It seems like a near-weekly occurrence for someone to find a vulnerability in a smart sex toy. We’ve published a few, but I realised after the recent ‘audio recording’ issue <link> that we had forgotten to blog one we found a long time ago.
Those of you who have braved my adult toy security talk at various cons (BSides, BH, 44Con, Steelcon etc) will know about this one already.
The good news is that this one has already been resolved with an updated mobile app. We checked both Lovense Remote and Lovense Wearables yesterday and can’t find direct evidence of it being present any longer.
The issue
The mobile app allows users to take and save photos during video sessions. The images are rendered from BMP to JPEG by the mobile app, presumably for reasons of file size.
We had a look at the APK and found where the temporary image files were being stored during rendering:
Here’s location and file in more detail:
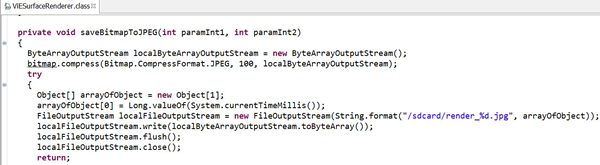
That’s the physical or emulated SD card! For older ‘droids, it’s more likely to be a removable SD card.
Yes, it’s a local attack. It’s not much different in risk to the audio recording issue. It is however yet another reason to be very, very careful with old phones with removable media.
Particularly if you use them to participate in online teledildonic sessions.
Disclosure
We made Lovense aware of this a long time ago. They updated the app and fixed the flaw.
The latest version of the mobile app <list current version> doesn’t appear to have this issue.














