How cleartext session tokens are stored in an unsecured directory that can be stolen and used to impersonate a Teams user.
TL;DR
Microsoft Teams stores unencrypted session tokens and cached conversations in users’ roaming AppData, which can be used by an attacker to gain access to the victim’s Teams account without having to authenticate or contend with potential conditional access policies.
This is a design choice by Microsoft as the folder is located in \AppData\Roaming\, which is a folder designed to be synchronised with folder redirection and similar technologies for user convenience. Imagine the frustration IT departments would be faced with if their Citrix users had to log into Teams every single morning. You can almost hear the angry mob with torches and pitchforks.
We leveraged this on a client engagement when I compromised a central file server, which held users’ roaming AppData.
Figure 1 – Compromised file server
Before I kick off, credit where credit is due. Vectra’s research into the Teams cleartext auth token issue first broke via BleepingComputer, and covers the ins-and-outs of Microsoft’s (soon to be sunsetted) Electron framework. This blog will cover this topic from a different perspective with more of an emphasis on exploitation and it’s potential use cases.
Introduction
Microsoft Teams stores a multitude of files within the following file path C:\Users\UserNameHere\AppData\Roaming\Microsoft\Teams, which includes configuration files, preferences, log files, application related files, and cleartext session tokens within an SQLite file.
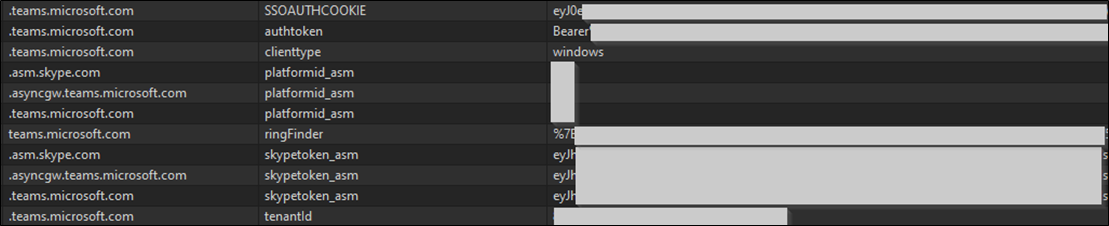
Figure 2 – Sample content from Cookies database
The cookie sqlite database contains the following cookies:
| Host | Cookie |
| .asm.skype.com | platformid_asm |
| .asm.skype.com | skypetoken_asm |
| .asyncgw.teams.microsoft.com | platformid_asm |
| .asyncgw.teams.microsoft.com | skypetoken_asm |
| .bing.com | MUID |
| .c.bing.com | SRM_B |
| .login.microsoftonline.com | CCState |
| .login.microsoftonline.com | ESTSAUTHPERSISTENT |
| .login.microsoftonline.com | ch |
| .office.com | MUID |
| .officeapps.live.com | timeZoneId |
| .tasks.office.com | PlannerWebSessionId |
| .teams.microsoft.com | SSOAUTHCOOKIE |
| .teams.microsoft.com | authtoken |
| .teams.microsoft.com | clienttype |
| .teams.microsoft.com | platformid_asm |
| .teams.microsoft.com | skypetoken_asm |
| .teams.microsoft.com | tenantId |
| .youtube.com | CONSENT |
| .youtube.com | VISITOR_INFO1_LIVE |
| apps.powerapps.com | PACookieRolloutBucketProd |
| forms.office.com | MSFPC |
| login.microsoftonline.com | SSOCOOKIEPULLED |
| login.microsoftonline.com | buid |
| login.microsoftonline.com | fpc |
| outlook.office.com | MicrosoftApplicationsTelemetryDeviceId |
| outlook.office.com | MicrosoftApplicationsTelemetryFirstLaunchTime |
| pentestpartners.sharepoint.com | MicrosoftApplicationsTelemetryDeviceId |
| pentestpartners.sharepoint.com | MicrosoftApplicationsTelemetryFirstLaunchTime |
| s02-emea.prd.attend.teams.microsoft.com | MicrosoftApplicationsTelemetryDeviceId |
| s02-emea.prd.attend.teams.microsoft.com | MicrosoftApplicationsTelemetryFirstLaunchTime |
| s03-emea.prd.attend.teams.microsoft.com | MicrosoftApplicationsTelemetryDeviceId |
| s03-emea.prd.attend.teams.microsoft.com | MicrosoftApplicationsTelemetryFirstLaunchTime |
| shared.officeapps.live.com | DcLcid |
| tasks.teams.microsoft.com | ai_user |
| tasks.teams.microsoft.com | MicrosoftApplicationsTelemetryDeviceId |
| tasks.teams.microsoft.com | MicrosoftApplicationsTelemetryFirstLaunchTime |
| teams.microsoft.com | TSREGIONCOOKIE |
| teams.microsoft.com | storedTheme |
| teams.microsoft.com | deviceId |
| teams.microsoft.com | firstTimeLaunch |
| teams.microsoft.com | MUIDB |
| teams.microsoft.com | clocale |
| teams.microsoft.com | ringFinder |
| teams.microsoft.com | minimumVersionClientUpdateTries |
| ukc-excel.officeapps.live.com | DcLcid |
| ukc-excel.officeapps.live.com | ExcelIsPreviousSessionSimplifiedRibbonOn |
| ukc-excel.officeapps.live.com | PageLoadSkeletonState |
| ukc-word-edit.officeapps.live.com | DcLcid |
| ukc-word-edit.officeapps.live.com | MicrosoftApplicationsTelemetryDeviceId |
| ukc-word-edit.officeapps.live.com | MicrosoftApplicationsTelemetryFirstLaunchTime |
Secure and common standards stipulate that all sensitive files, especially credentials, are encrypted to reduce the threat and likelihood of session hijacking via plaintext viewing.
Technically, using Teams with Edge or any Chromium-based browsers is a stronger choice as they encrypt cookie storage by default. However, Teams cannot encrypt its cookie database file as it needs to follow users around different devices.
Exploitation
Exploitation is simple and does not require the use of any special tools, such as Mimikatz to extract cached credentials from memory. Copy and paste will do, which has the advantage of not alerting anti-virus software.
The following steps summarise the chain of exploitation:
- Extract the contents of C:\Users\UserNameHere\AppData\Roaming\Microsoft\Teams.
- You can optimise this by only copying the necessary files:
- IndexDB
- Local Storage
- Session Storage
- Cookies
- Cookies-journal
- desktop-config.json
- json
- Preferences
- QuotaManager
- QuotaManager-journal
- json
- json
- json
- TransportSecurity
- This optimisation reduces the size from ~2 GB to 43.5 MB in my case
- You can optimise this by only copying the necessary files:
- Spin up a virtual machine with Teams installed.
- Replace your \Microsoft\Teams folder with the victim’s.
- Open Teams.
Congratulations! You now have access to their Teams account for you to search for juicy content or you could leverage this to socially engineer staff into doing your dirty work. Why should I waste computing power attempting to capture and/or crack hashed passwords when I can review internal communications to find credentials, or I could just ask the right people as you.
The remarkable thing about session tokens is that you have already authenticated and satisfied any requirements such as multi-factor authentication, coming from a trusted geolocation or IP address; conditional access policies will not save you. Anti-virus software will not save you.
Figure 3 – authenticated Teams session whilst PowerPoint is unauthenticated.
Snooping. Cached conversations
Teams also caches conversations, both direct messages and channel communications using Google’s LevelDB database structure, which stores .ldb files that can either be parsed or read as is. An attacker with access to multiple users Teams folder could leverage their access to mass parse these files to identify sensitive data such as internal communications and passwords.
Alex Bilz has researched Microsoft Teams from a forensics perspective and has developed tooling to parse these files; you can read more about his thesis work here https://www.alexbilz.com/post/2021-09-09-forensic-artifacts-microsoft-teams/.
Figure 4 – Goodbye Tom!
Conclusion
Unfortunately you cannot mitigate this threat and I don’t believe it will be fixed by Microsoft… The only thing you can do is implement monitoring and alerting for the following file paths:
- Windows: %AppData%\Microsoft\Teams\
- MacOS: /Library/Application Support/Microsoft/Teams/
- Linux: /.config/Microsoft/Microsoft Teams/
It should be noted that access logs within Azure AD do not provide any information as stolen tokens are not subjected to authentication.














