What is it?
Keeping on top of a dynamic internet footprint is hard; your attack surface is continually changing. Development, cloud, unmanaged & managed change, mergers & acquisitions, even 3rd parties can change your attack surface at any time. Data leaks, exposed credentials & plenty more can change your risk profile in real time
That’s where Attack Surface Management (ASM) can really help: keeping a track of your footprint, continuously looking for changes, with human pen testers involved to help you assess & mitigate risk. We proactively alert you to changes.
Depending on your needs and risk appetite, we can instantly start various complimentary services to assess & manage that risk.
How does it work?
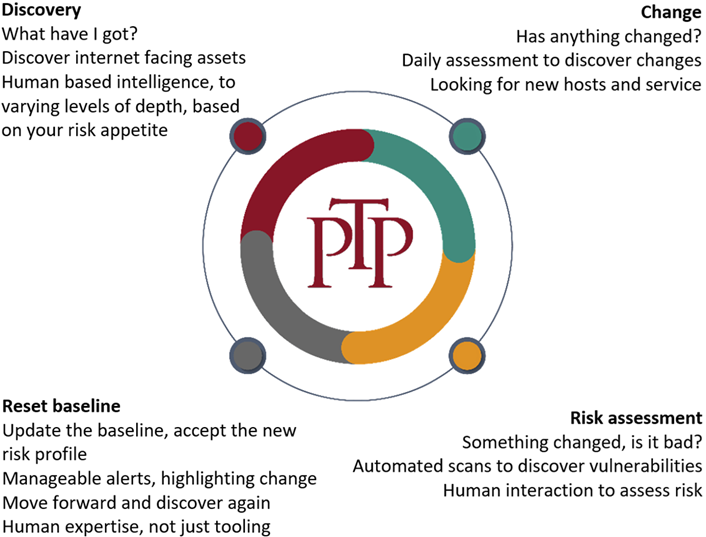
First: Set a baseline
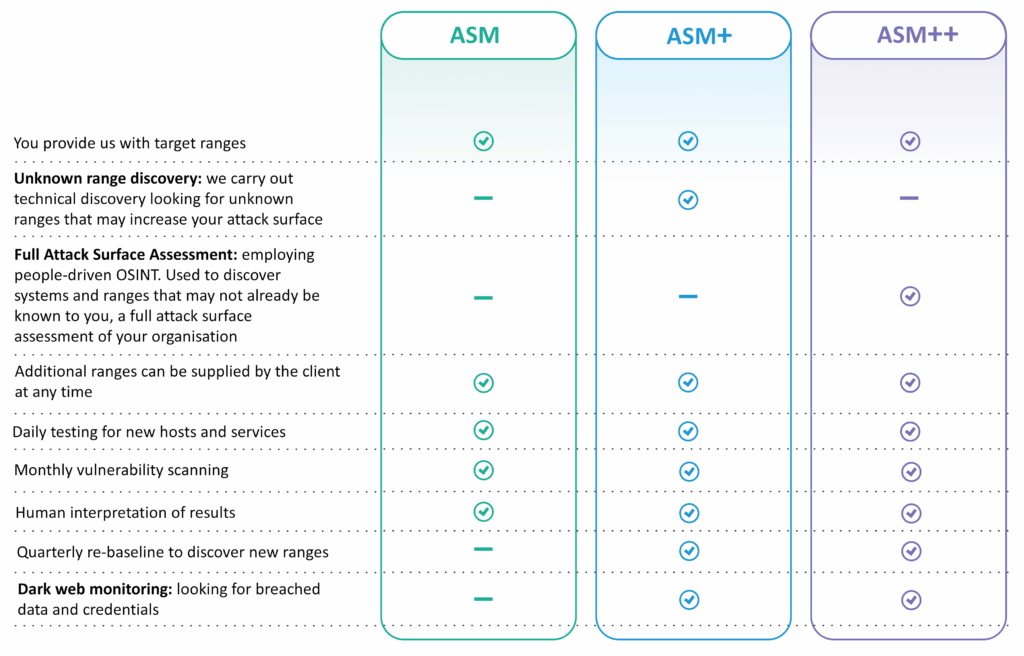
Option 1: Host discovery: an entry level option. You provide us with your internet-available hosting ranges. We will discover all hosts on these ranges & set a baseline from which changes such as new hosts or new services will be discovered
Option 2: Range discovery: a more involved option. Provide us with what you know, we add to this using tooling & human technical expertise to discover ranges & systems that you may not be aware of. We will present our findings to you before agreeing a baseline from which changes will be monitored
Option 3: Attack Surface Assessment: a fully featured option. Uses open-source information to identify the attack surface. We search the dark web for leaked passwords, intellectual property, & personally identifiable information. We also look for web vulnerabilities, mail weaknesses, unpatched & misconfigured systems, & the exposure of risky services such as remote desktop.
Second: Assess change
Every day, we will test against the baseline to look for changes in your internet footprint. Any new host or service will be flagged to you to ensure that you are aware of the change.
Mitigate Risk
On a rolling basis through the month, we will conduct more thorough vulnerability assessments to look for new vulnerabilities. Any findings will be manually reviewed to determine the best course of action.
Third: Take action
There are a series of proactive options that you can choose to help mitigate your risk in real time:
New host or service discovered: trigger an automatic vulnerability assessment to quickly assess risk.
Manual review & pen test: if the results of the assessment indicate increased risk, we can quickly commission a full manual penetration test (additional cost)
Web site & web application discovery: if a web site or web application is discovered, we will use AI to determine the level of interactivity & complexity of the host. We will raise this to you to determine if a quick vulnerability scan or in depth manual penetration test should be carried out. (additional cost for a manual pen test)
Dark web monitoring: we can also add functionality to your ASM service to include dark web monitoring, discovering compromised or exposed credentials, compromised data & indications of breach. (included in cost of ASM+/++)
Fourth: Reset the baseline
To effectively manage your attack surface, you need to know about CHANGE. Flagging every vulnerability and every service on every host every time is unmanageable. By resetting the baseline each time, we can ensure you can focus on changed assets and the risk they present.
ASM Plans
Test and Simulate

Free Pen Test Partners Socks!!!
Pen Test Partners socks are THE hot security accessory this season, if you're a security professional get yours now!
















