Maritime Testing
Both new-build vessels and existing ships must comply with maritime cybersecurity guidelines, and the process typically focuses on key areas like risk identification, systems connectivity, network segmentation, and the resilience of IT and OT (Operational Technology) systems.
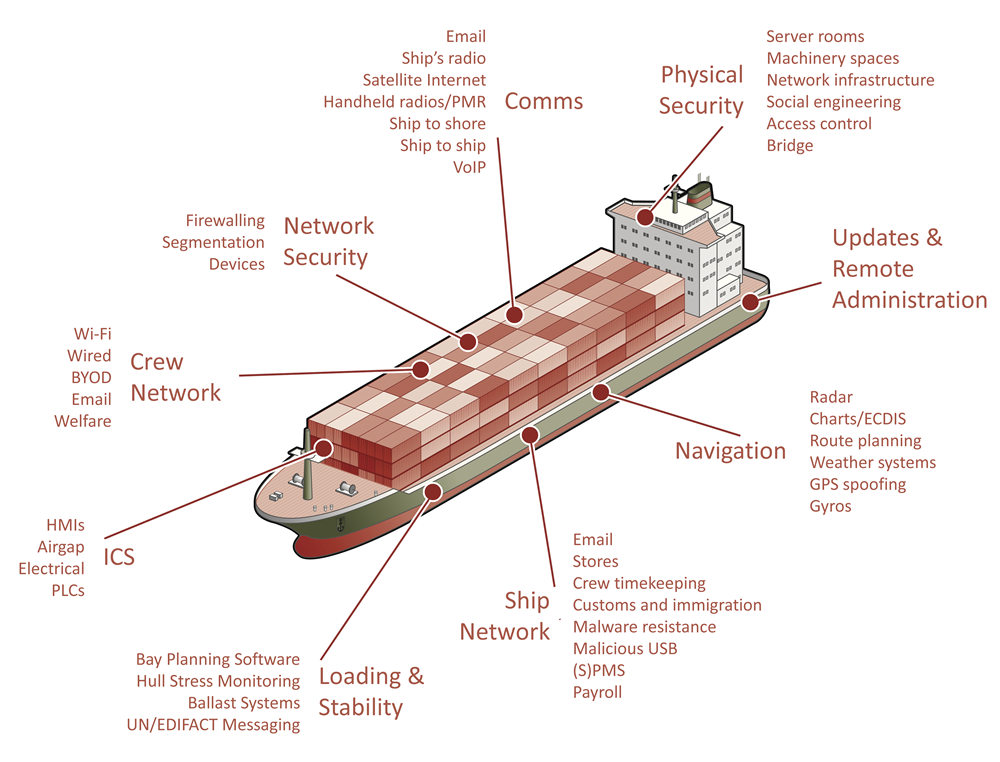
Existing vessels
Existing vessels generally must follow MSC.428(98) and MSC-FAL.1/Circ.3/Rev. “GUIDELINES ON MARITIME CYBER RISK MANAGEMENT”. This is very high-level guidance that focuses on using risk management within the 5-point framework of Identify, Prevent, Detect, Respond, Recover framework. In turn, it references Flag Administration’s guidance, BIMCO “The Guidelines on Cyber Security Onboard Ships” and IACS “Recommendation on cyber resilience (Rec 166)”, ISO 27001 and the NIST framework.
New-build vessels
New-build vessels are also now subject to IACS UR E26 and E27. These place a strong emphasis on the same 5-point framework, but formally establishes the responsibilities of the ship owner, systems integrator (the shipyard generally), suppliers and classification societies. It covers the design, construction, commissioning and operation phases. E26 concerns the vessel as a whole, with E27 covering subsystems provided by suppliers. Simplistically, the goals are for most subsystems to be E27 certified by classification societies, connected together securely and in a documented manner under E26.
The major classification societies have all published guidance for new-build vessels and class notations for existing vessels. All of these place a strong emphasis on understanding the systems on board – what they are comprised of and what they are connected to. This can be challenging for older vessels, where documentation is lacking, and many changes have been made over the years.
In terms of Identify, Prevent, Detect, Respond, Recover, maritime has focused on “prevent”, with very little effort expended on the other phases. Fundamental to all points are documentation, oversight, and understanding interconnections between systems.
If you have an existing fleet of vessels, it is recommended that initial efforts are spent on identifying the systems onboard and then determining how exposed to risk they are.
We always focus on high-impact, high-likelihood attacks during these initial engagements. An issue that could impact the entire fleet from the Internet is clearly of higher risk than one that impacts a single vessel when the attacker needs to be onboard.
Corporate systems
We still believe that corporate systems compromise is the most significant risk – for a vessel to operate, email and other IT systems must be available. Without email, how will the vessel receive orders? Without being able to complete cargo paperwork, how can the vessel sail? The corporate network is a significant risk due to a combination of factors:
- A large pool of attackers are familiar with Windows, with many off-the-shelf tools and techniques available for attack.
- Complete Windows domain compromise can impact an entire fleet, not just a single vessel.
- Security awareness is often weak, with many poor-quality passwords being used and phishing attacks often succeeding.
- The loss of corporate systems often has extreme impact on operations.
- Breaching IT systems is often the first step towards gaining remote access to OT systems.
In terms of impact, we consider the following:
- Immediate safety of the vessel and crew – can an essential or safety critical system be affected? Examples would be steering, propulsion, generators, power management system, ECDIS etc.
- Operational impact – can we stop or hinder day-to-day operations of the vessel? Cargo management systems, corporate machines, and offboard communications are good examples.
- Regulatory impact – can we affect the vessel by breaching regulations? If the vessel is detained by Port State Control or electronic logs are deleted, what is the outcome?
- Environmental impact – can we cause direct environmental impact or associated regulatory impact? Disabling exhaust gas cleaning systems or tampering with oily water discharge logs could be a trigger.
Vessel security in a nutshell
We have extensive experience working with existing and new-build vessels and believe that the following core areas are key to the security of a vessel:
- Oversight – every vessel is unique, and it is important to understand what is onboard, how it is connected, what impact it has if compromised, and how change is managed.
- Network segmentation – modern vessels often have multiple gateways between IT and OT and it is crucial that these are secured.
- Perimeter security – for an attacker to have deep impact, they need to carry out attacks from afar and across multiple vessels, bypassing perimeter security such as firewalls and malware detection.
- Windows domain security – although IT should not have direct impact on OT, initial access to OT is nearly always obtained by compromising a Windows account.
What does a testing engagement involve?
If there has been no previous penetration testing carried out, it is recommended that a sample of vessels are tested. Initially, a “typical” vessel should be chosen and examined in-depth. This will often identify issues that could impact the entire fleet and can be solved fleet-wide with simple fixes.
A typical engagement would involve the following stages:
- Assessing the maturity of the company in terms of the identify, protect, detect, respond, recover framework, normally using interviews and documentation review. This helps to direct further testing.
- Gaining understanding of the systems onboard the vessel. This would normally use a combination of documentation review, interviews, network exploration, and physical survey of the vessel.
- Network segmentation testing to ensure that IT and OT are adequately isolated. This would normally involve basic checks alongside efforts to compromise any gateways between systems.
- Testing of the core network on the vessel the satellite communications equipment, firewalls, switches and other infrastructure.
- Testing of any Wi-Fi networks available, confirming that network segmentation is in place, and passwords are adequate. Alongside this, a survey for any rogue devices will be carried out.
- A conventional Windows IT infrastructure test, normally aiming to achieve widespread compromise, starting from either an unauthenticated or normal crew account.
- Proportionate checks of OT systems to ensure that they do not present excessive risk. It is acknowledged that many OT systems are poorly secured, and focus should generally be on preventing initial access using network segmentation.
- Checks of the external attack surface of the vessel, such as exposed external IPs and Wi-Fi.
- Examination of any third-party systems, as far as is possible, to understand the risk they present. This would typically cover maritime specific software and some IT / OT gateways or monitoring devices.
Testing will always be carried out using a risk-averse approach, aiming to avoid causing disruption or making permanent changes to any systems. Continuous risk assessment is used, involving the crew where required.
Pen testing still carries a risk of disruption. If possible, work should be carried out when there will be minimal impact. Ideally this would be during a drydock or layup. Accommodations can be made for when the vessel is in operation or underway, but this will generally slow down testing.
The number of days required to test a vessel varies. Good coverage can be obtained on a conventional cargo vessel in 5 days, whereas more complex vessels such as dynamic positioning or scientific research may require 8 or more.
A debrief is strongly recommended to aid in understanding and answer any questions.
What’s the risk profile of a cruise ship?
Cruise ships have a unique risk profile. This is due to the huge number of guests on board, highly complex hotel systems and payment systems, mixed up with very involved OT and safety management systems.
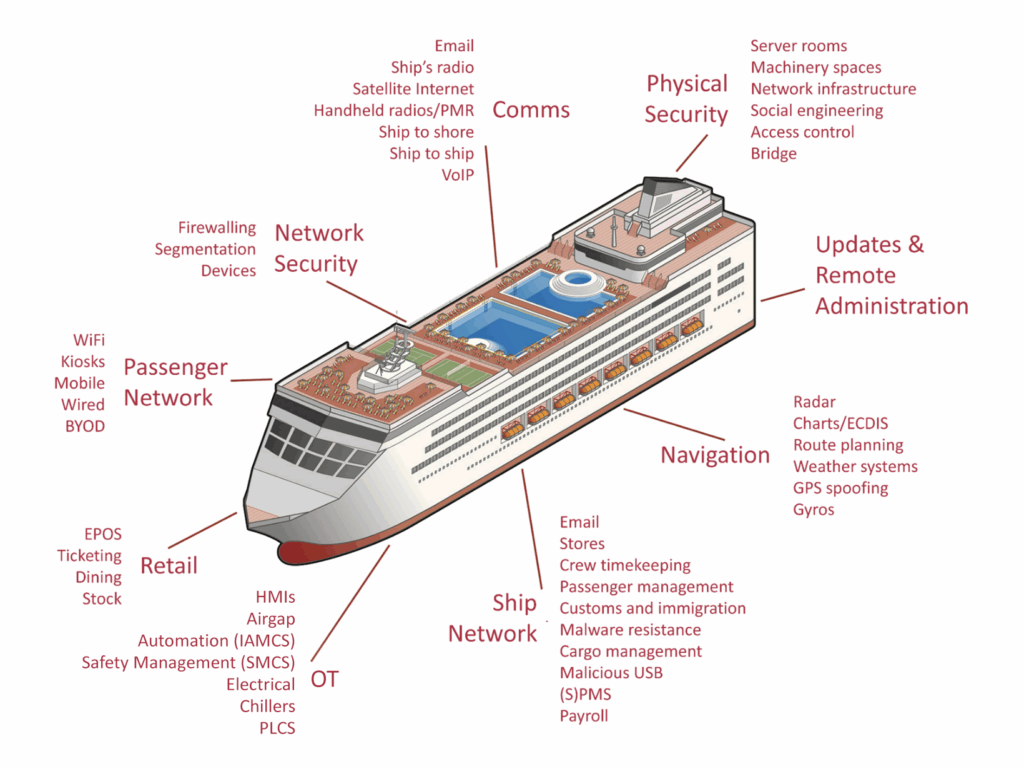
Testing perspective
One of the most important aspects is assessing the security of the vessel from the perspective of a guest. There are many networks exposed to a guest, such as Wi-Fi, TV, VoIP, cabin control networks and so on.
The main aim would be to compromise IT systems to obtain free services, although IT / OT segregation would be considered: compromise from a cabin through to critical OT systems has been achieved many times in the past.
Although OT systems are normally better isolated than IT systems, the impact if they are compromised can be extreme. Therefore it is proposed that they are examined at a design level and comprehensive testing performed. This would focus on those that are deemed vital to operation of the vessel from regulatory, safety and operational perspective.
Threat actors emulated in tests include:
- A guest who wishes to obtain free services, such as internet, or food and beverage service
- A member of crew who has access to the corporate network, or has run out of their internet access allocation and wants to bypass controls to get unmetered access
- Credit card data theft or tampering with hotel systems, such as mixing up or locking room doors
- Advanced attackers who can compromise OT and navigational systems, causing power outages or possibly even collisions
- Ransomware groups seeking to disrupt service to a vessel, or move laterally to other ships, or to the corporate on-shore domain
Testing conditions
Typically, work would be carried out under ‘light-grey box’ conditions, with as much documentation, credentials and access permitted as possible. This helps accelerate testing and keeps costs manageable.
Often, third party maritime technology suppliers refuse to support or comply with requests to provide information or access. The operator or owner’s assistance is often needed to remind these suppliers of their obligations to support their clients and their desire to provide security assurance to their vessels!
Testing is time-boxed and will focus on the higher impact and more connected systems. More risky testing, particularly against OT systems, is typically carried out when the vessel is in a safe condition, such as alongside or still in the yard as it approaches launch.
If the vessel is operational and / or underway at the time of testing, then more risky tests may need to be deferred. Risk assessments will be performed with crew throughout to ensure that no unsafe actions are taken.
OT methodology
Testing would use a risk-averse OT methodology, ensuring that no changes are made to systems. We have significant experience of many different maritime OT systems, which means that many vulnerabilities and typical weaknesses can be determined by low-risk techniques.
Impact assessment
Someone very familiar with the vessel, such as the chief engineer or technical new build team should be available to assist in assessing impact. This may also require someone with deep knowledge of the classification society rules and any typical port state inspections carried out.
It is common to find that there are single points of failure that can cause significant impact but do not have adequate security controls around them.
Which OT should be checked?
The following OT systems would be expected to be checked, but more or less may be included based on the vessel design:
- IAMCS / Automation
- Navigation / conning / ECDIS
- Safety Management System (with expected links to fire detection, watertight doors, VDR, ICMS etc.)
- Vessel performance monitoring
- Scrubber monitoring
- Remote engine diagnostics / monitoring
- UPS systems for any systems onboard
- VDR (if TCP / IP connected to other systems)
- Fire detection system
- Watertight doors
- PA / GA system
- Cabin control system (potential control of heating, water temperature, lighting and access control to cabins)
- Access control system for bridge, engineering and other restricted spaces, potentially including a physical key tracking system
- Firewalls and gateways associated with any OT systems
- Remote access mechanisms for any third party vendors, ensuring that compromise of a low-impact system such as theatre stage automation cannot impact high-impact systems such as ICMS. We have seen this in the past!
Alongside this, we generally recommend that an audit of the physical security of the vessel is carried out. This would involve looking at how spaces are secured using electronic access control and keys and performing a full walkthrough of the vessel.
During past engagements, issues have been found where spaces such as HVAC or swimming pool plants are inadequately secured, allowing access to IAMCS. From this perspective it may be possible to significantly impact machinery onboard.
Purple teaming
Over the life of a vessel, it is expected that new systems and equipment will be added and connected to networks. Whilst some of these will be fully approved and designed, we have often found unauthorised or poorly documented systems implemented.
For this reason, we are often asked to perform a “purple team” exercise, where we will use defined TTPs that should trigger any alerting or monitoring.
Ideally, the SOC would detect the presence of a new connected system, and then crew should have adequate tools to track down the system. Examples of such techniques would include placing a new gateway into various network locations and generating unexpected traffic such as TeamViewer from existing OT systems.
What else is tested?
Alongside the above enhanced testing, the following testing is often carried out:
- Connect to Wi-Fi and exposed Wired networks to check that they are adequately segregated from each other. Particular attention will be paid to the more easily accessible networks such as the guest and crew Wi-Fi.
- Investigate the quality of passwords used around the vessel, including the Wi-Fi, corporate machines, bridge systems, and external systems.
- Determine how passwords are stored on the vessel.
- Investigate how passwords are rotated when crew leave and join.
- Connect to the business network and investigate the connections back to shore, looking to compromise the Windows domain either from a position of no or low privilege.
- Check that vessel-to-vessel attacks are not possible
- Perform a network and physical audit of the vessel to discover any undocumented or unknown systems, looking for bridges between different network segments or unauthorised remote access.
- A vulnerability assessment of the onboard PCs and servers in the corporate domain
- A vulnerability assessment of TV / broadcast networks onboard.
- Check that the external attack surface of the vessel is minimised.
Expertise that you can trust
Vessels are one of the most complex environments we are asked to test the security of. Testing requires significant expertise in both the maritime and hotel domains, which is why several of our team are ex ships engineers or officers of the watch. Contact us today to discuss securing your vessels with our experts.
Transport

Free Pen Test Partners Socks!!!
Pen Test Partners socks are THE hot security accessory this season, if you're a security professional get yours now!