TL;DR
- PTP: Hey Carlsberg, all your videos and names of people visiting your exhibition can be viewed by anyone.
- 84 days pass
- PTP: Hi…. Any update?
- Carlsberg: We’ve added rate limiting
- PTP: Nope, you can still brute force it. There is no rate limiting…
- PTP: Hello…?
- 90 days in total pass
- Zerocopter: You can’t disclose because we said so…
- PTP: Yeah, that’s not how responsible disclosure works
- 150+ days pass
- We publish
The exhibition
My Wife and I visited the Carlsberg exhibition in Copenhagen in August 2025 and we were given wristbands with a QR code on them. As we went through the exhibition, there were various interactive elements where you could create your own blend of beer, create a video of you dancing in a beer glass, and take pictures of you and your group. These were linked to the QR code so they could be accessed and downloaded later. It was a great exhibition and well worth going to if you’re in Copenhagen!

I noticed that the URL in the QR code just contained the wristband ID and no other extra data. It looked like there were only 26 million combinations. That’s not enough entropy to provide any security for your personal data and videos. I saw that Carlsberg had a public Vulnerability Disclosure Policy with a very broad scope, so I couldn’t wait to get back home to my hacktop to have a wee poke!
Burp is my favourite tool
The URL to access the “memories” was https://homeofcarlsberg.com/memories/ and the wristbands expire after 30 days. The only authentication was the simple wristband ID.
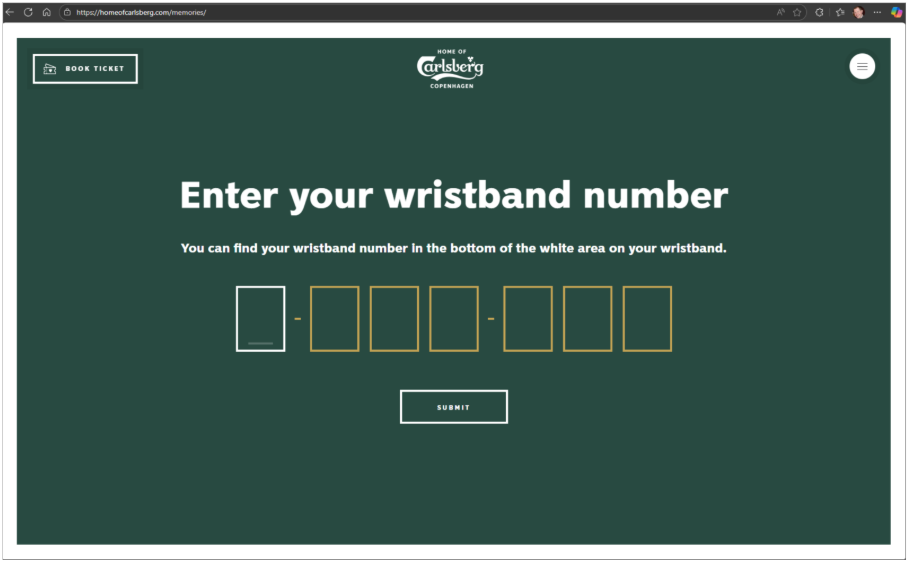
The page converted the wristband ID into a hex string and passed that to a Google cloudfunctions.net URL which returned links to the stored media.
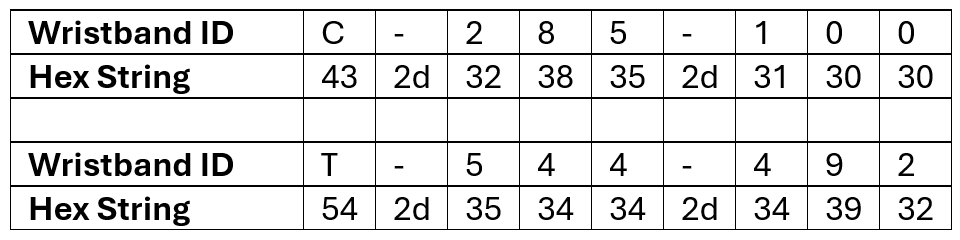
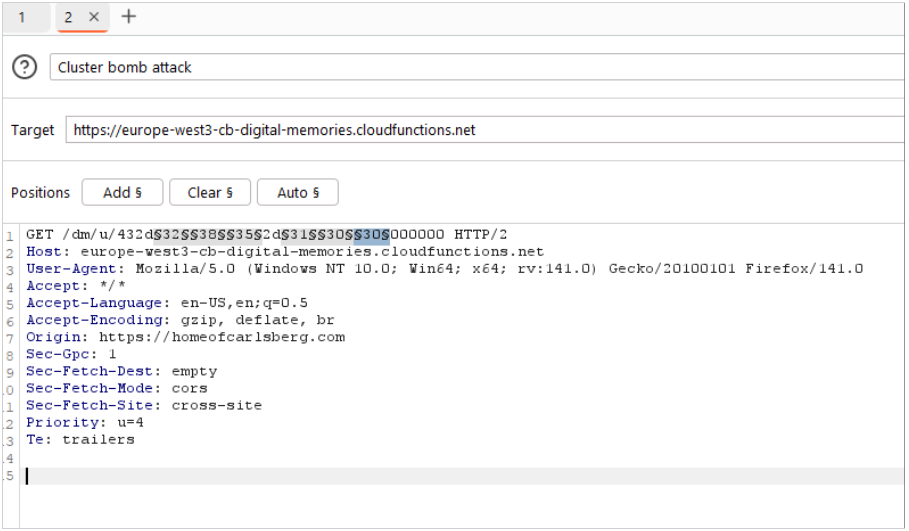
Whilst sticking to the terms of the VDP, I was able to brute force one million wristband IDs in around two hours. It would be possible to gain access to all the valid wristband IDs in around 52 hours from one laptop. From the sample of one million, I validated around 500 wristband IDs, so multiplying that by 26 means that there are around 13,000 people who use the interactive elements at the Carlsberg exhibition every 30 days. Assuming all the letters are used.
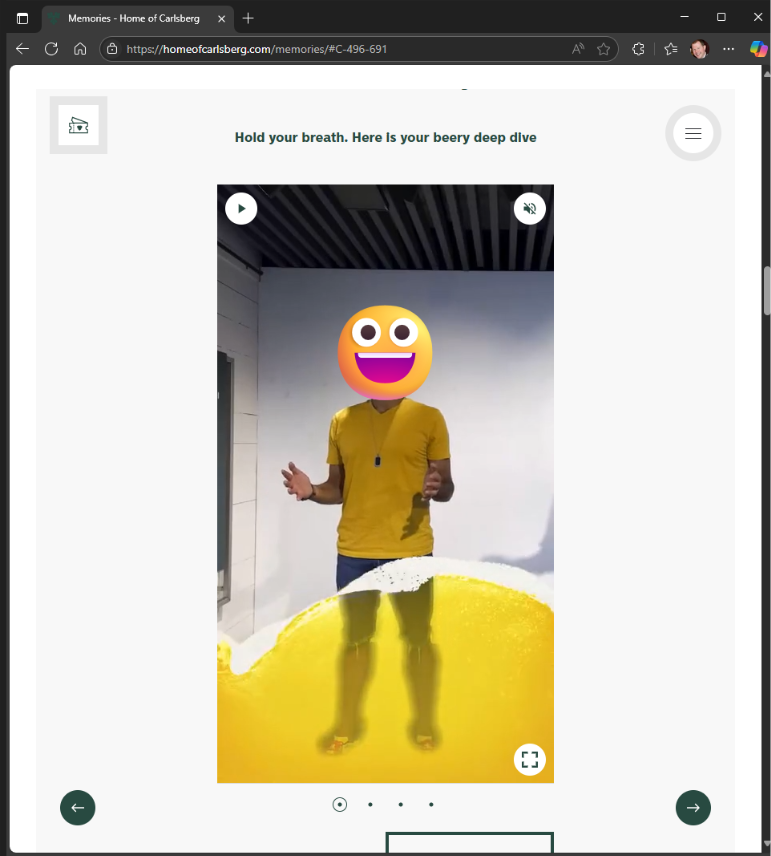
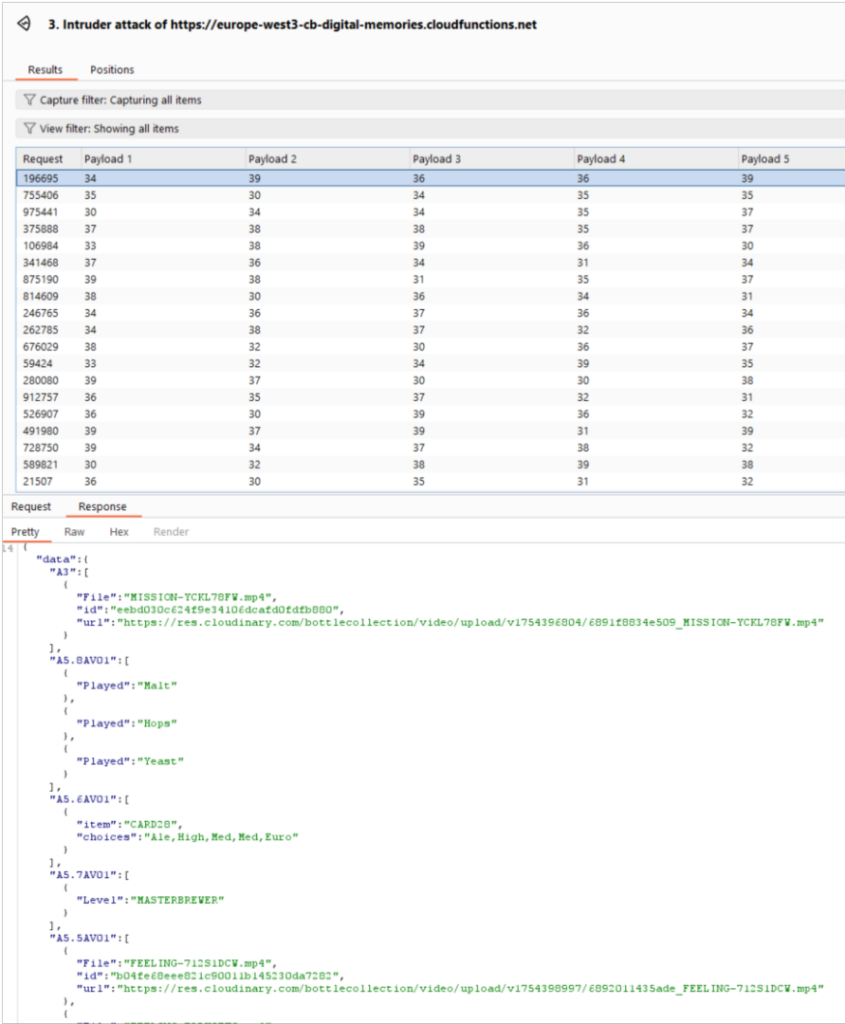
As well as containing videos and pictures, the data also contained the full names of people who participated. This type of information is classed as Personally Identifiable Information (PII) and should be secured under GDPR.
Disclosure…
The Carlsberg Vulnerability Disclosure Policy reads well and encourages disclosure through Zerocopter. They have a list of promises about keeping in contact and even have a cool Hall of fame where they list previous researchers who have disclosed vulnerabilities. Unfortunately, I don’t think I’m going to be on that list…
I submitted a report to Zerocopter on the 19th of August 2025. It was accepted the same day and given a CVSS score of 7.5 (High). A few days later Carlsberg marked the issue as “work in progress”.
And that’s when all three public promises made by Carlsberg started to be broken.
- There were no thanks as promised
- There was no evaluation of the report within 10 business days
- They didn’t keep me informed of progress
A month later I contacted Zerocopter and let them know that we generally disclose vulnerabilities after 90 days and sent them a link to our disclosure policy. We’re very flexible and if companies need time to fix things, we understand. If companies are responsive, friendly, and keep us updated, we’re happy to retest issues free of charge, offer advice, and we’ll disclose when the issues are fixed. Zerocopter replied saying that all vulnerabilities must be kept confidential in line with the Zerocopter confidentiality requirements.
Another month passed and I asked for feedback on the issue. Zerocopter tried to get a reply from Carlsberg, but it went unanswered.
As the 90-day timeframe approached, I asked Zerocopter about the disclosure part of the responsible disclosure they were managing for Carlsberg. Disclosure must be a part of a responsible disclosure policy. A vendor can’t just ignore researchers and force us to be bound by a confidentiality clause. If there is no disclosure, then it’s not a vulnerability disclosure policy. Zerocopter didn’t reply to that, but Carlsberg did… 84 days in! They said that they had applied rate limiting and so the issue was mitigated and asked if I could retest it. I retested the issue, and unfortunately it was still possible to brute force the wristband IDs, so I replied the same day and let them know. That was the one and only message I received from Carlsberg. I offered to help and asked about their timescales for adding more entropy to the wristbands. No reply.
In December I asked Zerocopter again about the disclosure part of the disclosure policy, but they said that a client “is in their rights to take their time” and that I should “please be a bit more patient”! I think my patience has been exemplary, Zerocopter. The problem is that clients can easily avoid public disclosure by avoiding communication. That’s not how to do responsible disclosure. That’s not how to do IT security.
Disclosure timeline
13/08/25 – Visit to the Carlsberg exhibition in Copenhagen
18/08/25 – Initial discovery
19/08/25 – Evidence collection
19/08/25 – Reported to Zerocopter
19/08/25 – Accepted by Zerocopter
21/08/25 – Carlsberg changed the status to work in progress
11/09/25 – Zerocopter let me know that they couldn’t accept a 90-day disclosure policy.
28/10/25 and 31/10/2025 – Requested an update on the issue
11/11/25 – Carlsberg said that rate limiting had been applied and asked if I could retest it.
11/11/25 – I replied stating that rate limiting had not been applied and provided a video of “Dawn” doing a dance as evidence that it was still possible to access these videos.
02/12/25 – Asked Zerocopter about the vendors communication requirements and how was it possible to do responsible disclosure if researchers are bound to confidentiality agreements.
02/12/25 – Zerocopter replied asking me to be more patient and vendors had a right to “take their time”
16/01/26 – Disclosure more than 150 days after reporting the issue to Carlsberg and Zerocopter
Conclusion
I had high hopes for Carlsberg given their excellent vulnerability disclosure policy and their relationship with Zerocopter, but they hid behind silence and Zerocopter tried to prevent disclosure with their confidentiality clauses. There’s always a balance between the criticality of exposed data and disclosure, but after discussions with colleagues, we felt the data wasn’t too sensitive, and this was on the responsible side of disclosure.
So, bye bye hall of fame mention, and bye bye to my soon-to-be-burned Zerocopter account.
Responsible disclosure needs to include disclosure.