We’ve been finding vulnerabilities in electronic flight bags for a few years now. Disclosure response from the vendors involved has varied from excellent to radio silence.
In every case we have tried extremely hard to engage with the vendors involved, even where we were ignored. We asked friendly OEMs and others in the supply chain to help encourage those who wouldn’t respond to us, but their efforts were ignored too.
In some circumstances, it would be possible to affect take-off performance and landing calculations, resulting in significant safety events such as those here. It’s now time to publish details of some of our findings. Here’s the first of a series of blogs:
PilotView CMA-1410 EFB
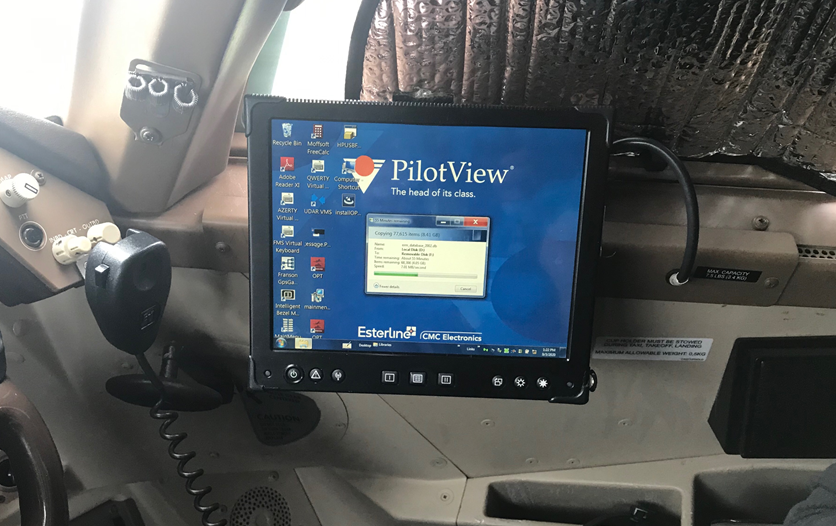
We first encountered the Esterline / CMC Electronics CMA-1410 EFB on a 747. It was stored during the Coronavirus downturn, but has since been retired. It last flew at the end of March 2020. Another of the fleet with a similar fit has flown since.
The EFB carries out the many functions one would expect. That of most interest to us was perf – how much power to apply in order to take off
EFBs are typically either installed, in which case their security will generally be the responsibility of the plane manufacturer, or portable, in which case their security in operation is the responsibility of the device vendor and operator.
This one is a little unusual – it’s arguably portable, but is lockwired in place. There are two EFBs on the flight deck, one for each pilot. They are also networked together and take a serial data feed of the airspeed, so they aren’t practically removable by the pilot, as a regular portable EFB would be. As far as we’re concerned, these are therefore installed EFBs. Having the two EFBs networked undermines a critical security control – both pilots would independently calculate perf, and cross check. The network allows both EFBs to be compromised and both output incorrect, but identical, data. Here’s the lockwiring:

Device lockdown
Now, one would expect such a device to be locked down to prevent pilots, cleaners, maintenance staff and anyone with cockpit access from interfering with them. Bored pilots on long haul routes don’t mix well with weak device security, among many threats.
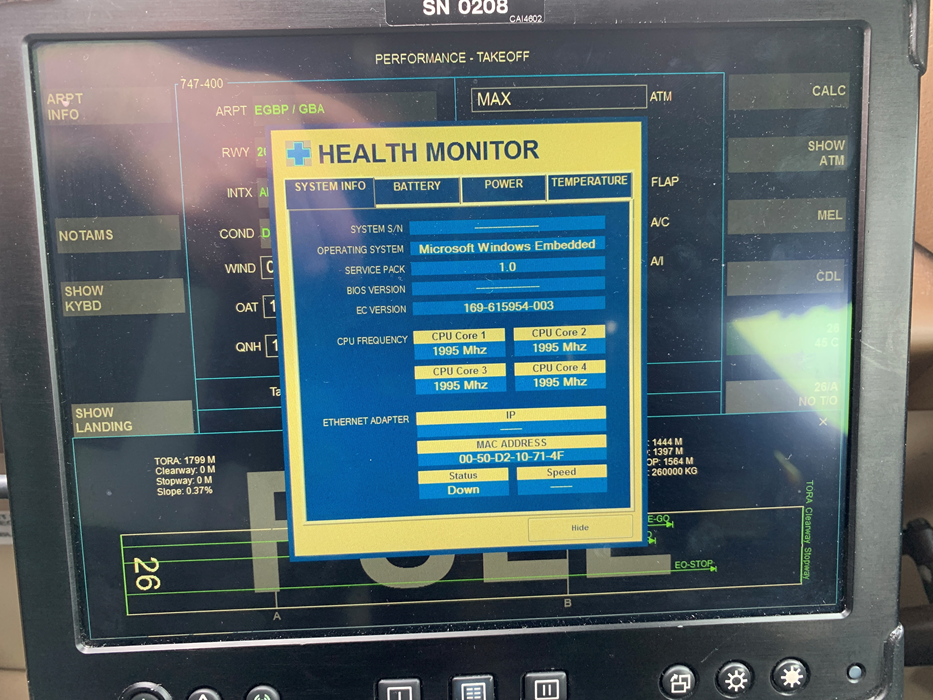
Indeed, there is a soft button with a password to enter an ‘admin’ mode similar to the below image, so the device manufacturer has clearly made some efforts to lock the device down. Unfortunately, that’s where it stops!

Breakout and compromise
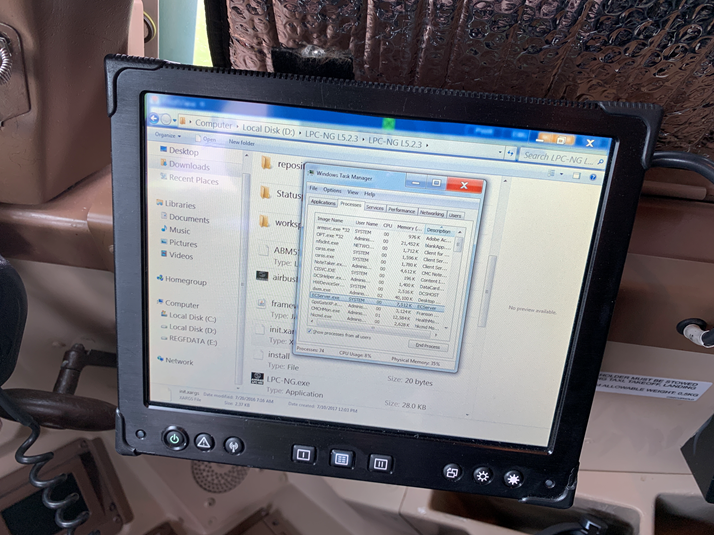
Kiosk breakout was possible using a number of low complexity mechanisms, including pressing Ctrl-Shift-Esc on the Windows virtual keyboard to invoke task manager, and then either killing PilotView or running explorer.exe / cmd.exe directly:
And what’s this? Could the credentials be any less complex?
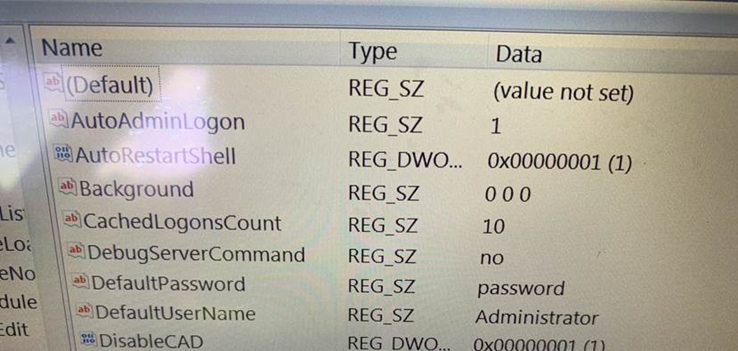
Also, as can be seen here, one EFB can be compromised from the other over the network:
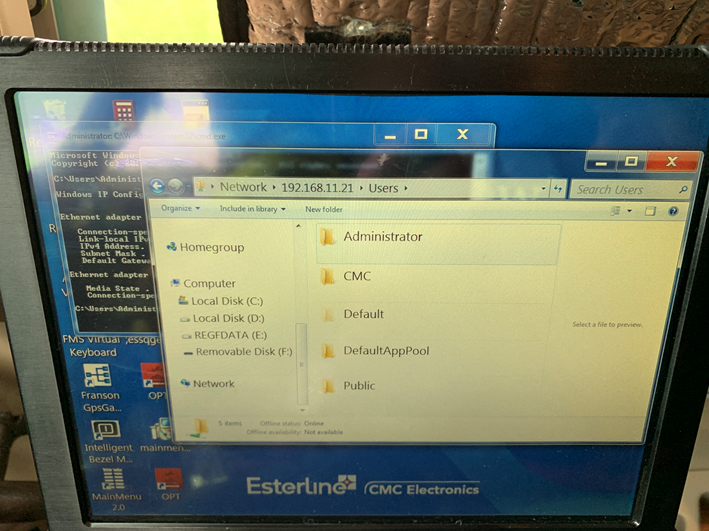
A malicious actor could now modify the performance database and cause incorrect perf calculations. Insufficient thrust could be commanded, so a runway excursion or tailstrike could result
Unsecured USB
It had a USB port too, completely unsecured, but it’s OK, there was a sticker saying not to use it:

There were no physical or other technical controls to prevent a USB mass storage device from being connected. It is therefore possible for an attacker to exfiltrate data, or modify existing files via this route.
The use of a USB “rubber ducky” or “bash bunny” to automate attacks would significantly reduce the amount of time physical access was required.
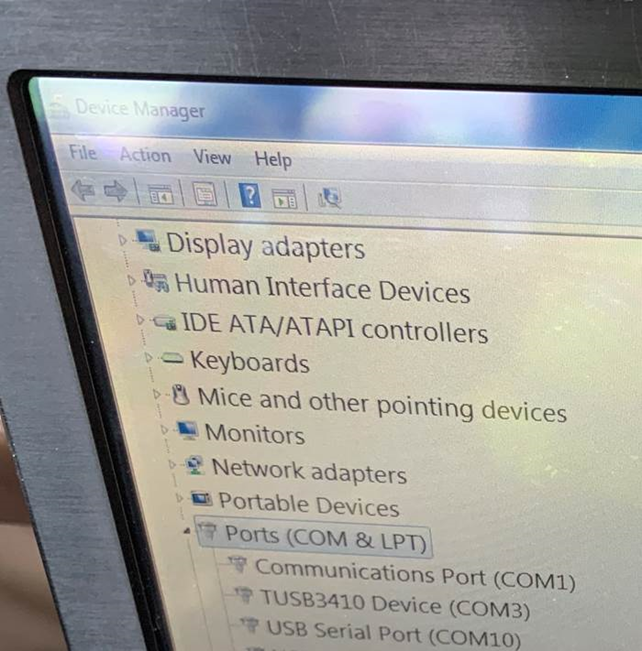
Windows 7 Embedded went end of life in October 2020, yet some of these EFBs are still in use. The device security didn’t appear to have had much attention since it was first built in 2013:

Wi-Fi?
Whilst this device did not have Wi-Fi enabled, we read the vendor documentation which showed that Wi-Fi was usually supported and available. This could have changed everything: this EFB is hard to access, as it’s in the cockpit and protected by the multiple layers of physical security that are present at many airports.
However, with Wi-Fi enabled and the device so out of date, a remote attack from the terminal building becomes much more possible.
Disclosure
We understand that remediation in the airline industry can take a long time. Security can also be a challenge, given differing responsibilities for EFB security between vendor and operator, also the long lifespan of avionics.
That said, we expected to be listened to and responded to, rather than ignored in the case of CMC Electronics.
We were introduced to CMC Electronics through one of their customers in September 2020. We never had a reply to that email.
We tried again on 22nd Feb 2021, 8th March, 4th June. Nothing. So we tried another route and got another intro to a different contact at CMC. That got us to someone else.
24th June, they introduced us to a product manager. 25th June, no response. 27th July, no response.
10th August 2021, we received a response saying that the issue had been raised internally.
We’ve heard nothing more since, despite chasing further.
It’s a shame that CMC didn’t at least engage in a discussion.
Who is responsible?
For an EFB to get to a plane without any serious attempt at securing it is a concern. Whilst we don’t know the detail of who installed it back in 2013, there are clearly failings both at the EFB manufacturer and the operator.
It should not be possible to install a device with such a poor device lock down.
It’s also disappointing to see the response to vulnerability disclosure from CMC. This is at odds with other EFB vulnerability disclosure processes we’ve experience in the aviation sector.














