TL;DR
- Electronic Flight Bag (EFB) integrity varies between different airlines and devices
- Aviation cyber security is becoming increasingly prominent with regulators
- EFBs often connect to unsecure networks including public Wi-Fi
- Security measures are not always effective and can be inconsistent
Device integrity
Device integrity generally means ways of ensuring that data is real, accurate and safeguarded from unauthorised user modification.
The integrity of EFBs is essential when it comes to cyber security in aviation. It is fair to say a lot of progress has been made in the last few years. But as with many things in life there are still areas which could be improved.
To ensure cyber security and resilience in key systems (including operators of essential services or competent authorities), the NIS Directive (Network and Information Systems) was adopted by the European Parliament in July 2016.
It is the first piece of EU-wide legislation on cyber security and in 2018 it was transposed into UK law. In the UK, the Civil Aviation Authority (CAA) is the Co-Competent Authority for the regulation of NIS alongside the Department for Transport (DfT).
The CAA created and uses an accredited third-party cyber security audit model called ASSURE. The third-parties involved are ASSURE Cyber Suppliers that are subject to rigorous and continuous accreditation processes.
Aviation organisations which are deemed in scope need to procure an ASSURE Cyber Audit from an accredited ASSURE Cyber Security Supplier. Further details are available here.
When researching EFBs, PTP ensured that conditions in the lab accurately replicated those that would be encountered in the real world. With this in mind, we used licensed airline pilots in our commercial aircraft simulator to help us fully understand and assess weaknesses and any likely outcomes from tampered EFBs. Having modified an EFB performance application, outcomes were demonstrated by the pilots who behaved as they would on a commercial flight.
Who would want to attack an EFB?

An EFB performance app we wrote ourselves, for vulnerability demonstration purposes
It is not uncommon for teenagers to cause data breaches and disruption purely for entertainment, but there are other groups who may want to hack EFBs maliciously. Aviation is a target for climate change activists and it is not uncommon for airports to experience disruption due to noise or airport expansion protests. Other threat actors e.g. state-sponsored hackers shouldn’t be overlooked either.
When backing is funded by a nation state, the potential damage to airlines (and therefore their national governments) through the grounding of flights due to hacked EFBs is huge. Aviation plays a very large part in contributing to the infrastructure of a nation as well as, in most cases, contributing large sums in taxes and economic activity – $1.7 trillion worth in the USA per year.
The implications of airlines discovering that malware had indeed been installed on their EFBs could be wide ranging, but one thing that is likely is the grounding of aircraft until the appropriate security departments have reviewed exactly what had been compromised and what effect it could have. Clearly, the cost implications of this are potentially huge.
It is common for hackers to try and focus their attacks – a one size fits all hack that downs all EFBs worldwide is almost impossible. So to enable them to focus their efforts they often obtain useful information (a.k.a “Enumeration”) that helps them to target their attack. Some very useful information to hackers includes obtaining the hardware, software and versions used on their target device. Given that airlines routinely (and proudly) publish advancements in technology, in the EFB case it isn’t hard to find details of all this information online.
You can readily find out which airline uses what software, its version and what devices they use. What that information and with enough time, it is not inconceivable that a malicious hacker could cause significant disruption, an incident or even an accident.
EFB attack surface
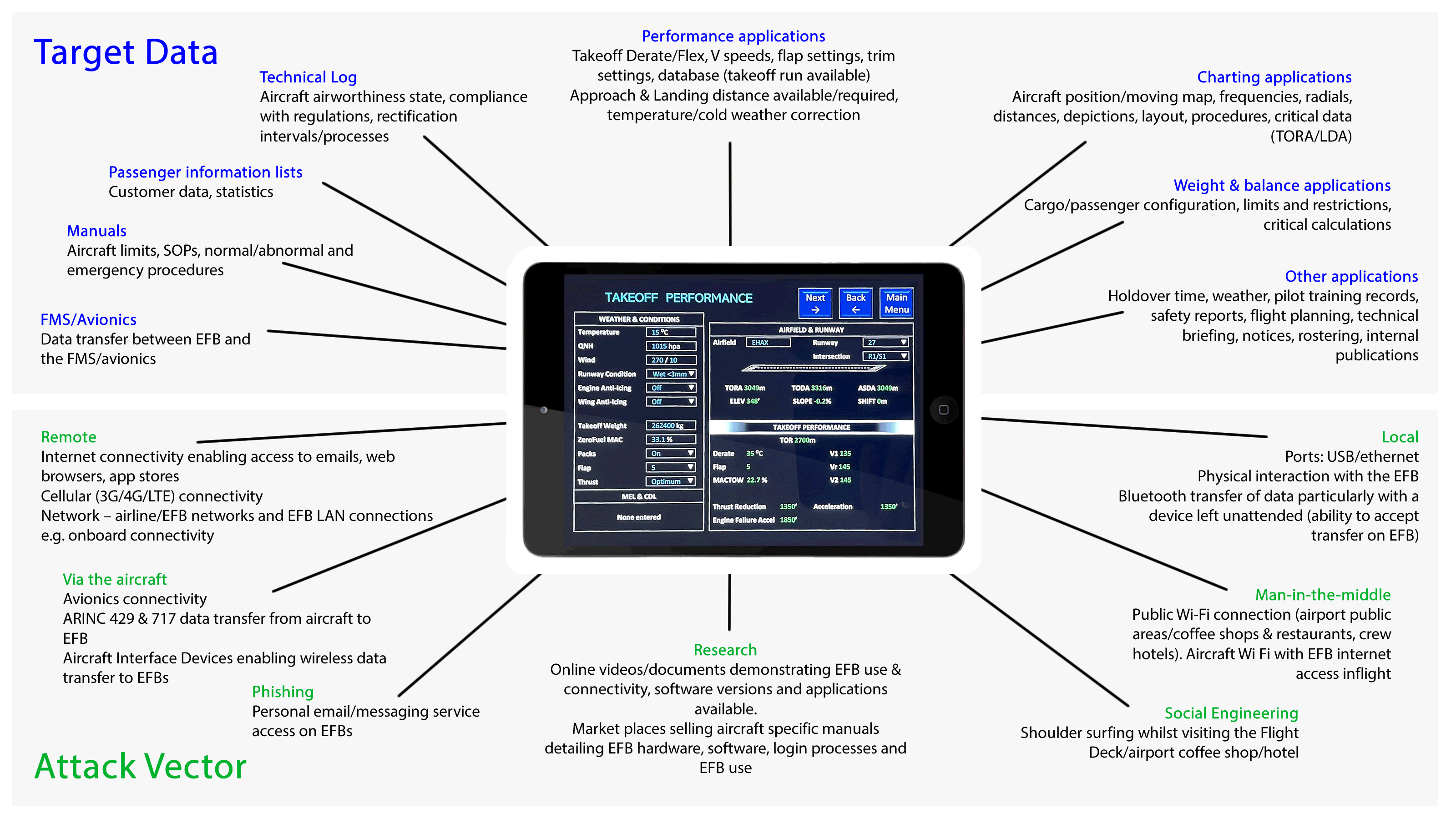
Click image to enlarge – opens in new tab.
Access
The two methods of accessing an EFB are local and remote. We won’t be going into precise methods here, but what is clear is that access methods could be made more difficult with some relatively small changes.
Local Access
Local access to installed EFBs whilst difficult, is not impossible. Installed EFBs are harder to access than portable EFBs as they remain in secure areas (e.g. the Flight Deck or within maintenance areas). As a result, remote access is more likely to be attempted than local access. However, local access still remains a possibility and EFB safeguarding should take this into account. Unfortunately not all methods of EFB safeguarding are necessarily up to the job.
In our lab we demonstrated the local access scenario, including the modification of performance applications, charts and manuals. Performance applications enable pilots to calculate critical data e.g. how much thrust they use to takeoff on a specific runway and at what velocity they safely climb away from that runway (a variety of factors need to be considered including aircraft weight, runway length etc.) Implications of modifying this data will be discussed in more detail later in the blog series.

Many installed EFBs contain ports which are generally used for maintenance purposes. These ports are often not disabled when the maintenance function is not required.
Quite unbelievably, stickers are placed over the ports which state they should not be used, including on one of the newest and most modern commercial aircraft.
Clearly, this is not an effective way of preventing misuse of the device.
Whilst portable EFBs are sometimes fixed to flight decks, it is more common for them to be given to pilots as personal devices.
As these pilots use their EFBs for things like email / messaging / video calls it’s not uncommon to see them being used in public hotel areas.
A misplaced or forgotten EFB in a hotel bar (or a distracted pilot) could easily allow someone with malicious intent the ability to access the device locally.
This raises the question as to whether portable EFBs that are used as personal devices and regularly removed from the aircraft are really appropriate.
Remote Access
The remote access scenario covers many different areas (in particular in the Software section below) and in both the installed and the portable case there are numerous methods of attempting to remotely access an EFB. Almost all EFBs require some form of internet access, and pilots often use this for their personal email accounts and messaging applications.
Bluetooth and cellular data are frequently turned (or left) on and many have 3G / 4G / LTE enabled. When accessing the internet, Wi-fi is generally the most popular connection. The networks used to provide internet access vary and in many cases the EFBs connect to pilot’s home networks, airport coffee shops / restaurants, and hotel networks whilst pilots are away. The security and integrity of hotel Wi-fi could sometimes be described as dubious at best (not to mention public hotspots in airports), yet EFBs often connect to these networks to perform various important tasks such as updating critical applications.
Recommendations
- Use a Mobile Device Management system to remotely manage and update the device
- Enforce strong PINs, supported with biometric authentication
- Have a strong policy and controls for separating personal and business use, with the ability to audit that use
- Restrict ports properly, it’s more effective than stickers!
- Provide cyber security training for all users
- Create and test a backup plan, should the EFB fail or be unavailable for ‘cyber’ reasons
- Get firm evidence from the device and software vendors that the device and apps are suitably secured
What’s next?
There are currently four posts in this series on EFB security:
- EFB Tampering 1. Introduction and Class Differences
- EFB Tampering 2. Device Integrity
- EFB Tampering 3. Take-off part one
- EFB Tampering 3. Take-off part two
Related: EFB Safety Advice for Pilots














