How we went from a telematics control unit in a vehicle to domain admin on a corporate network
We’ve tested numerous telematics control units over recent years and gathered many of our findings in to some good practice guidance here.
However, just occasionally we find something that blows our mind. The ‘lining up of the holes in the Swiss cheese’ if you like.
This story is one of them.
We were asked to review the security of a TCU for a vehicle. Unsurprisingly, it makes a data connection over cellular.
One of the threat models we considered was whether an attacker with a vehicle, or with access to a vehicle or TCU could exploit the TCU service and back end systems.
The first line of defence was a private APN. That’s a great idea, as it means that only authorised SIM cards can make a connection. That’s good, though we have some guidance for private APN security here.
However, if your attacker has possession of the TCU or the SIM/eSIM in the TCU, then they’re probably already able to access your private APN.
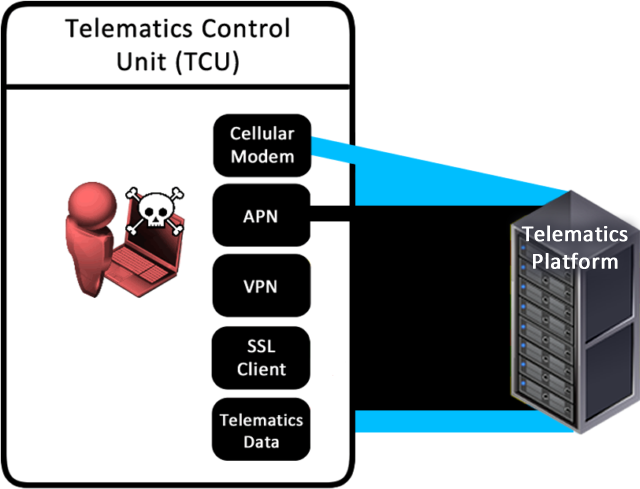
Once on to the APN, the provider wisely created a VPN from that to the corporate network.
Next, traffic to the APN server was further secured using SSL. The follows defence in depth, which is good – layer upon layer of security.
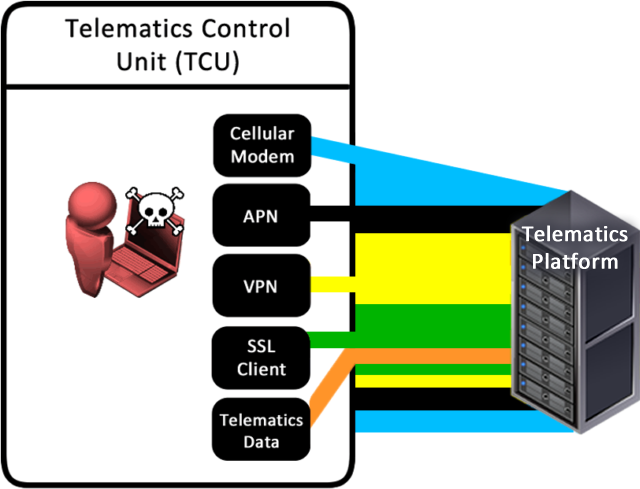
Plain text HTTP requests can then be sent through the SSL tunnel. Nothing untoward at this point.
What we found next was the surprising part: the VPN connection to the telematics platform had no significant segregation from the rest of the corporate network.
This meant we could access other servers within that company’s internal network; servers outside of the TCU back end. We had a connection from a vehicle to the corporate network!
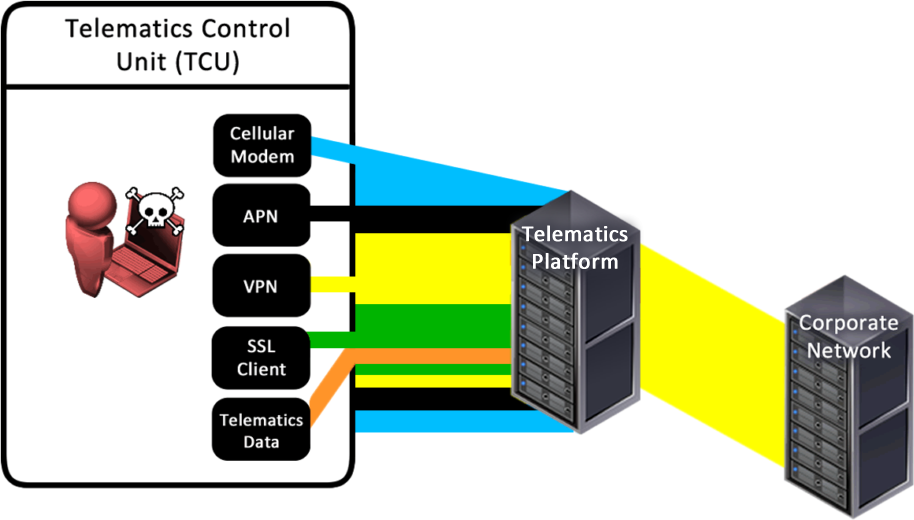
Simple network segregation of the VPN, restricting access to the telematics platform back end, would have mitigated this. Thorough hardening of the TCU back end systems would be wise too.
At this point, we had a discussion with our client and asked how they would like us to proceed. Fortunately, they were very forward-thinking and asked us to see how deep the rabbit hole went.
This led, fairly quickly, to us discovering Domain Admin credentials from systems outside the TCU environment that gave us DA on the entire corporate network.
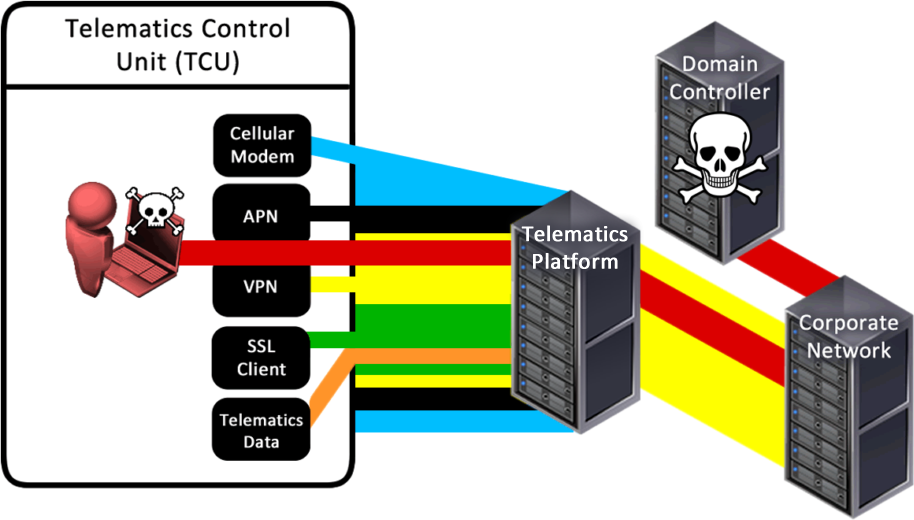
To summarise: we took a telematics unit from a vehicle, pulled the SIM card from it, put it in a USB modem connected to a laptop, connected to their internal network and compromised the entire domain it from the outside.
Pulling a physical SIM is probably the easiest way of achieving this, though it’s possible to ‘break out’ of eSIMs too, and it’s sometimes possible to use the TCU itself as a network bridge to the back end as well.
Advice
It’s important to consider all potential threats and threat actors when reviewing security of vehicles. An unhappy or inquisitive owner can be a threat, as can someone who has purchased a used TCU.
Whilst there may be some legal recourse and a trail of cellular breadcrumbs to follow when investigating a breach of this variety, the negative press coverage is likely to be more damaging. The consequence of ransomware injected in to a network with DA privilege is quite scary.
However, no-one expected to get Domain Admin from a telematics control unit, least of all us!