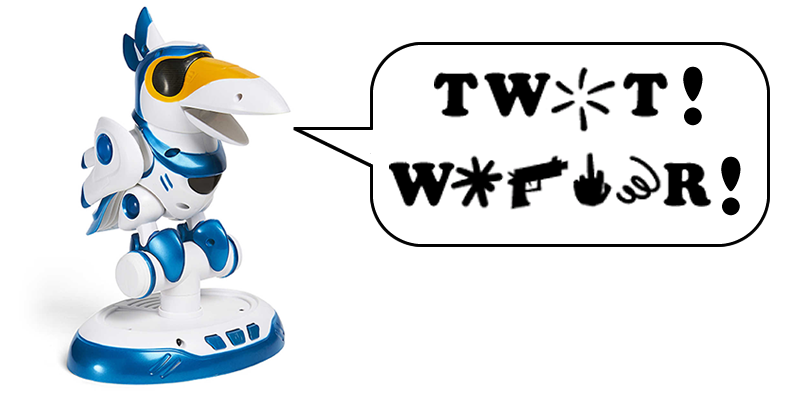
The holiday season is approaching, so retailers are selling plenty of smart kids toys. You’ve probably seen our earlier work, making My Friend Cayla swear.
The manufacturer, Genesis, sell plenty of other smart toys: the iQue smart robot was hacked by our friends at the Norwegian Consumer Council as part of their award winning #toyfail campaign.
Both iQue and Cayla were banned by the German telecommunications regulator a few months back.
BUT THERE IS MORE
I’ve had a Teksta Toucan talking toy for a while, but hadn’t got round to putting batteries in it. It featured on live BBC World News last year, bought last minute from a famous toystore in London.

We knew that the Toucan had much in common with My Friend Cayla and iQue, so had a go at the same attacks.
Here’s the result
In homage to one of my favourite comedy shows, the Fast Show, here’s the Toucan swearing like Unlucky Alf’s parrot
How-to
There are two methods. The easy one first.
The Toucan is a Bluetooth audio device. It has a microphone and speaker.
Just pair it to a Bluetooth audio device (laptop, phone etc) and play some audio through the Toucan. That easy.
Of more concern is that one can use the microphone too. Yes, just like Cayla, a 3rd party can snoop on your kids and your house.
We are in the process of reporting this to the German telecommunications regulator in the hope of another ban being issued.
The complicated method
The Toucan works in a slightly different method to Cayla. The audio files are .mp3 contained in an OBB.
Extract the Android package in the same way that we did with Cayla and simply change the mp3 to a sweary one of your choice.
Advice?
Parents: don’t buy these toys. If you have one already, I suggest returning it to the retailer. If you want to keep it, only allow the toy to be used under close parental supervision and ensure it is switched off when not in use.
Regulators: please ban smart kids toys that allow trivial snooping on our kids!
Manufacturers: if you take even the most basic steps towards securing smart toys, this sort of attack won’t happen.
Further research
Next, we want to have a look at the firmware to see what else we can find. The PCB is quite different to Cayla and iQue.
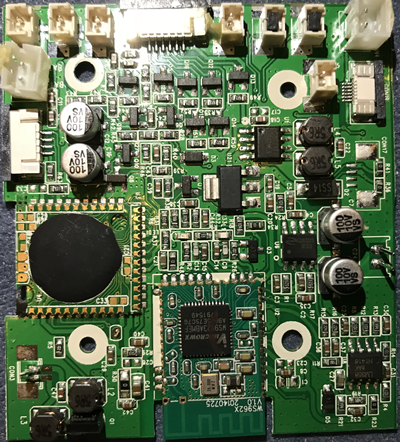
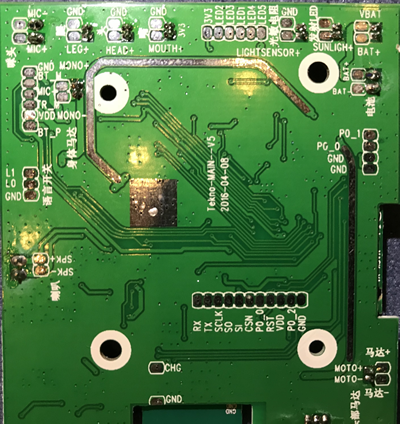
And plenty of test pads, ripe for pulling firmware from.