TL;DR
- Issues commonly arise when clients provide an application which is unsigned or does not meet device requirements.
- Installing an application can be challenging without a Mac, access to Xcode or if the client is having trouble signing the application manually as this is normally done by the app store upon release.
- There are a number of methods that can be used to load unsigned or fake-signed applications on the device: Tweaks, sideloading platforms and on-device sideloading.
Introduction
In certain circumstances it can be challenging installing client applications for testing. Situations arise where the application could be provided unsigned or requires self-signing. As a result, the application cannot be directly provisioned to the device. Installing the application can be challenging without access to a MacBook and Xcode or if the client is having trouble signing the application.
There are several methods that can be used to load unsigned or fake-signed applications on jailbroken or non-jailbroken devices. This article aims to outline these methods and highlight the pros and cons of each. The various options of sideloading can be separated into three categories for the purposes of this blog: Tweaks, sideloading platforms, and on-device sideloading.
How iOS apps are signed
Apple requires mandatory code signing during development and before distribution. Once the kernel has started on the device it controls which user processes and apps can be run on the device. To ensure that all apps come from a known and approved source (such as the App Store) and haven’t been tampered with, iOS requires that all executable code is signed by using an Apple-issued certificate. This includes apps provided on the device and third party apps.
Developers can choose a number of methods to deliver apps to devices for testing. Most commonly, iOS apps are delivered via distribution platforms such as TestFlight (by Apple) which requires Apps to be signed. A pre-signed iOS App Store package (IPA) file can also be provided.
What is sideloading?
Sideloading is installing an application on a device outside the Apple ecosystem. This can be done on jailbroken and non-jailbroken devices.
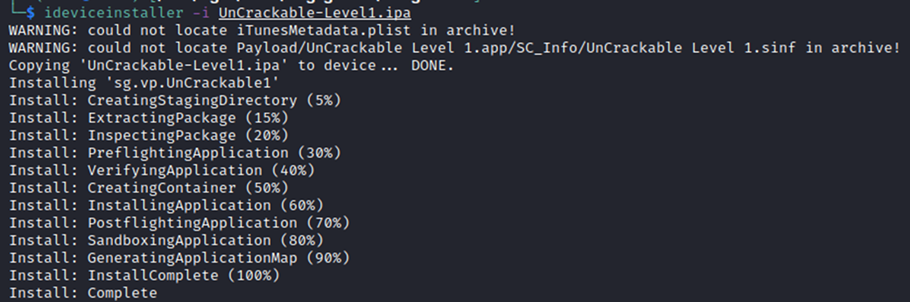
Normally when receiving a signed client IPA file it can be easily installed using a tool such as ideviceinstaller on a jailbroken testing device. Ideviceinstaller makes use of the libimobiledevice library which allows communication between iOS devices and non-Apple operating systems.
OWASP provides a series of vulnerable mobile applications. These are the UnCrackable Apps for Android and iOS. The UnCrackable series of iOS Apps was used here for demonstration purposes.
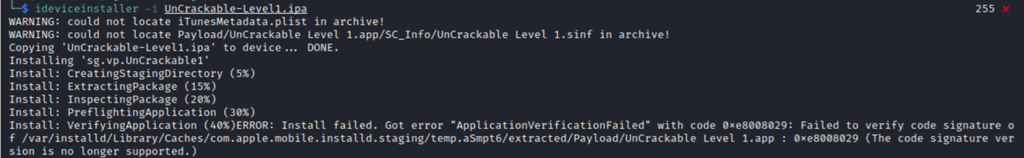
When attempting to sideload the application using ideviceinstaller, the following error is returned, which details that an app was not signed and the provisioning profile was not found:
Sideloading methods
A number of methods to install unsigned iOS applications exist, which all require different pre-requisites. We will look at sideloading apps on jailbroken and non-jailbroken devices. Non-jailbroken devices typically have limitations on testing in general, but they can be useful under specific circumstances. The methods listed are not exhaustive but represent the most common techniques used during mobile app testing.
Tweaks
On Jailbroken iOS devices,Tweaks allow customisation. They are extensions, written in Objective-C or Swift, and can provide useful functions during an engagement, such as bypassing Jailbreak detection.Tweaks can be obtained once successfully jailbreaking a device, depending on the jailbreak method these can be accessed via third-party package managers such as Cydia, Sileo or Zebra, which are installed once the device has been jailbroken. The Sileo package manager can be viewed below.
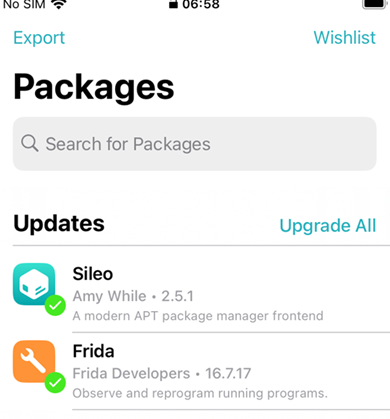
Tweaks can be accessed by adding a developers repo to the device within the sources tab.
AppSyncUnified
AppSync Unified (AppSync) is a Tweak that allows for the installation of fake-signed IPA packages on an iOS device.
Requirements:
Jailbroken device: iOS 5 to 18
AppSync is split into two separate dynamic libraries AppSyncUnified-installd and AppSyncUnified-FrontBoard. AppSync Unified utilises Cydia Substrate’s dynamic hooking function MSHookFunction() to bypass installd’s signature checks.
If the app in question has valid signing information, AppSync Unified will not make any modifications to it, and simply pass the information along to the original Apple-implemented function, letting the app installation process carry on as if the system was not modified at all.
However, if the app contains invalid signing information, AppSync Unified will generate the appropriate signing information and pass it along to the system.
AppSync Unified 90.0 introduced a second dynamic library that injects into the FrontBoard and FrontBoardServices private frameworks. This is done in order to bypass a set of signature verifications that are performed at app runtime, generally used for timed app expirations.
To obtain theTweak, it has to be downloaded via the browser or pushed onto a jailbroken device using scp to a writable directory such as /var/tmp. Ensure the version that is downloaded matches your device’s architecture.
Once on the device, the package can then be installed using dpkg.
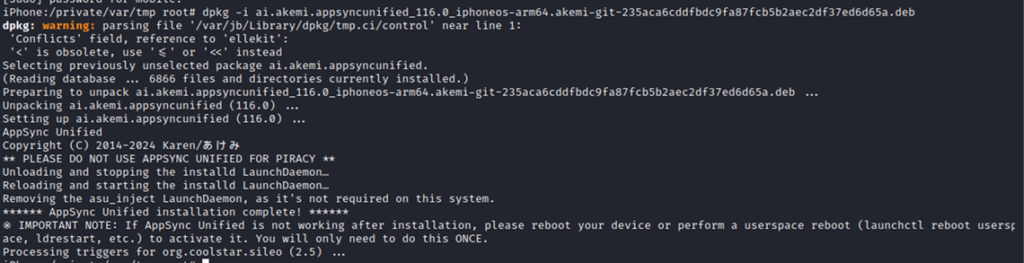
Then by entering the package manager (in this case Sileo) it is possible to view theTweak on the device.
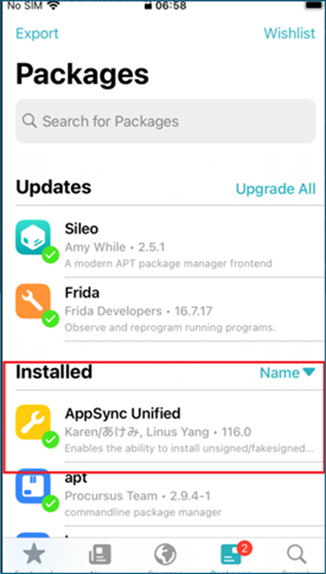
It is then possible to sideload applications without any issues.
Advantages:
- No timebound signing issues.
- IPA can be directly loaded on the device.
- No Apple signature required
- Broad iOS version support
Disadvantages
- Requires a Jailbroken Device.
Sideloading Platforms
A number of sideloading platforms also exist that allow installation of unsigned or self-signed IPA files. These platforms such as Altsore and Sideloadly use Apple’s personal development provisioning method to perform the app signing and installation process. As both methods require a free Apple ID certificate, apps signed and loaded using this method are only valid for 7 days, however this is normally sufficient for the duration of an engagement. After 7 days, these applications have to be refreshed to continue using them.
Altstore
Requirements:
- Computer (Mac or Windows) to run AltServer
- macOS 10.14 (Mojave) or later
- Windows 10 or later
- iTunes and iCloud (from Apple)
- iOS device on iOS 12.2 or later
- Apple ID
Altstore is an alternative app store for iOS devices that allows users to install apps outside of the official App Store without requiring a Jailbreak. It uses a user’s Apple ID to generate a code signing certificate which is required for sideloading apps. Altstore requires a companion app, Altserver installed on a Windows or macOS device. It communicates with iTunes and iCloud to interact with Apple’s provisioning system.
The platform has a 3-App Limit allowing 3 active sideloaded apps at a time. This can be bypassed using the MacDirtyCow exploit.
Altstore also offers a premium service (Altstore PAL) which is only available to EU residents due to Apple’s regulations.
Installation instructions for AltStore are detailed on the website, however the process has been summarised here for setup via Windows.
- Download and install the latest version of iTunes and iCloud directly from Apple (not the Microsoft Store).
- Extract AltInstaller.zip and run Setup.exe.
- Go to search in your Windows task bar, then type in “AltServer” and click “Run as administrator.” Make sure to allow access to private networks if prompted. AltStore will appear as an icon in the taskbar.
- Open iTunes, then enable “Wi-Fi sync”.
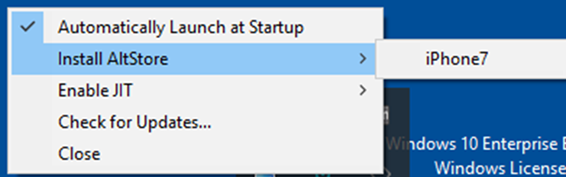
- Click the AltServer icon in the bottom right taskbar. Then go to “Install AltStore” and choose your iOS device.
- You may need to disable “Real-Time Protection” in Windows within the “Virus and Threat Protection Settings” or the app installation and refreshing mechanism will be blocked.
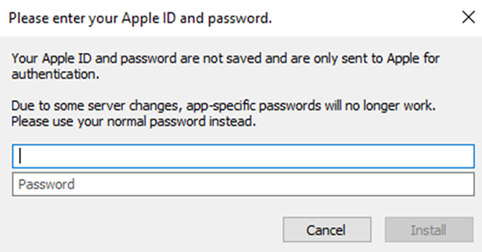
- Enter your Apple ID email address and password. This will allow AltServer to authenticate with Apple and configure your account to support sideloading apps.
- Wait a few seconds, then an AltServer notification should appear saying AltStore has been successfully installed onto your device.

- On your iOS device, go to Settings -> General -> Profiles & Device Management. Tap “Trust [Your Apple ID],” then tap “Trust” again to confirm.
Once your target app is on the device, open AltStore and press the “plus”, select your target application.
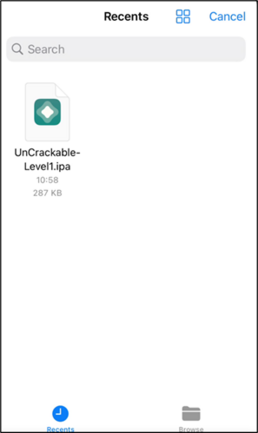

The app will then be loaded onto the device.
Advantages:
- A jailbroken device is not a requirement.
- Broad iOS version support
- User friendly interface
Disadvantages:
- Apps signed for 7 days only, however this can be auto refreshed.
- 3-App-Signing Limit (although this can be bypassed)
- MacDirtyCow requires iOS 14.0-16.1.2 (excluding 15.7.2)
- Requires an AppleID
Sideloadly
Requirements:
- iOS device in a jailbroken or non-jailbroken state, on iOS 7 up to iOS 18.3.
- A valid apple ID or developer account.
- Windows or MacOS.
Sideloadly is a standalone app for Windows and macOS that sideloads apps via USB and Wi-Fi. It also uses Apple’s developer provisioning system and allows the installation of apps on iOS devices. Unlike AltStore, it does not rely on a background server.
The application requires users to select the IPA file via the app which can be transferred over USB or Wi-Fi.
Once the application is installed on your Windows or MacOS host, the following steps can be used to install an IPA file.
- Open Sideloadly
- Connect your iOS device to your PC using a USB lightning cable.
- Drag and Drop or open the file in the tool.
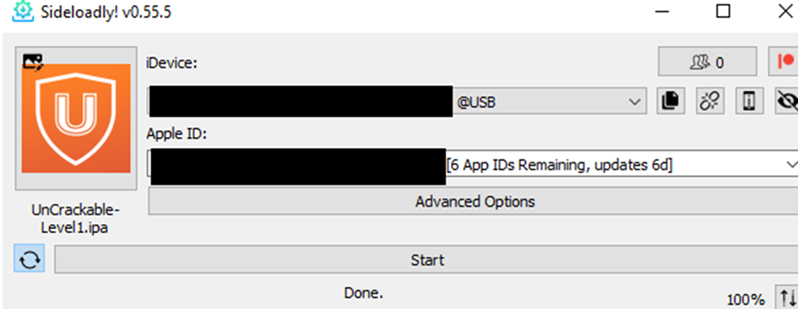
The app also has several advanced options, such as different signing modes, dynamic upload,Tweak injection and plist modification.
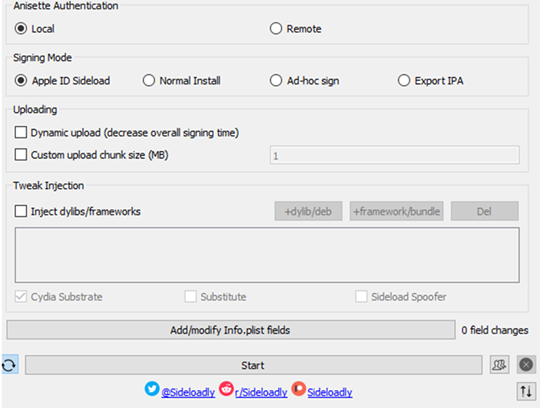
Once an IPA file is selected users are prompted to enter their Apple ID credentials, and the app is loaded onto the target device.
Advantages:
- A jailbroken device is not a requirement.
- Advanced signing features,Tweak injection, multiple signing modes,
- No background server required
Disadvantages:
- Apps signed for 7 days only; however this can be auto refreshed.
- 3-App-Signing Limit
- Requires an AppleID
On-Device Sideloading
On-device sideloading methods also exist, such as TrollStore. This allows users to install and sign IPA files natively through the device itself.
TrollStore
Requirements:
- iOS device running (iOS 14.0 – iOS 16.6.1, 16.7 RC (20H18), and 17.0)
TrollStore is an on device sideloading tool with the ability to permanently sign apps without necessary entitlements. It is used to install applications that are permanently signed.
TrollStore uses a CoreTrust exploit. This is only possible through exploitation of a CoreTrust bypass, which allows bypassing code-signing checks. The original TrollStore used the CoreTrust Root Certificate Validation Vulnerability, whereas TrollStore 2.0.0+ uses the CoreTrust Multiple Signer Validation Vulnerability.
iOS 17.6 and 18.0 introduced a mitigation that prevents binaries not running as root from spawning binaries as root (using the com.apple.private.persona-mgmt entitlement). This means even with a CoreTrust bug, TrollStore may not work anymore on these versions despite a CoreTrust bypass, because it relies on a root helper for several tasks.
The installation of TrollStore varies based on the iOS version running on the device. The process is extensively documented here. However the following steps are generally followed.
- Install a TrollStore installer on the device (such as TrollInstallerX) using a sideloading method.
- Run the installer on the device
- Download the chosen IPA file onto the device.
- Import the IPA via the TrollStore application, using the “plus” icon within the app. In this case installing via an IPA File.
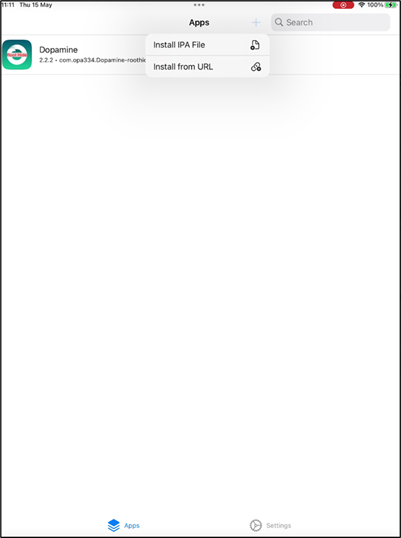
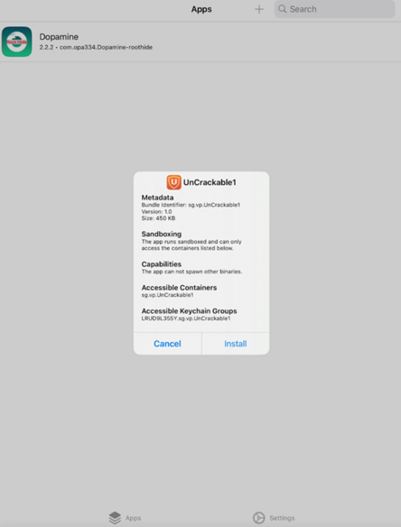
The installed app can then be viewed on the device.

Advantages:
- A jailbroken device is not a requirement.
- Permanently signs IPA files
- No background server required
Disadvantages:
- Restricted by version and availability of the CoreTrust exploit.
- Requires sideloading the installer before being able to use the app and permanently sign and load IPA files.
Conclusion
This article has detailed a number of sideloading methods that may be able to assist when receiving unsigned or fake-signed applications. Tweaks such as AppSync provide an easy and streamlined method to install IPA files on the device, providing compatibility with a large range of iOS devices. These require the device to be jailbroken.
Sideloading platforms can easily allow users to load apps and provide advanced signing features. However limitations exist with app signing length and the requirement of an AppleID. Finally, on-device sideloading solutions can provide permanent app signing for jailbroken and non-jailbroken devices.