Who we work with
- Airlines, airports, and ground handling organisations
- Ship owners, operators, and maritime service providers
- Rail operators, infrastructure owners, and rolling stock suppliers
- Automotive manufacturers, suppliers, and mobility providers
- Logistics, freight, and last mile delivery networks
- Public sector and regulators that need sector expertise
Why this sector is different
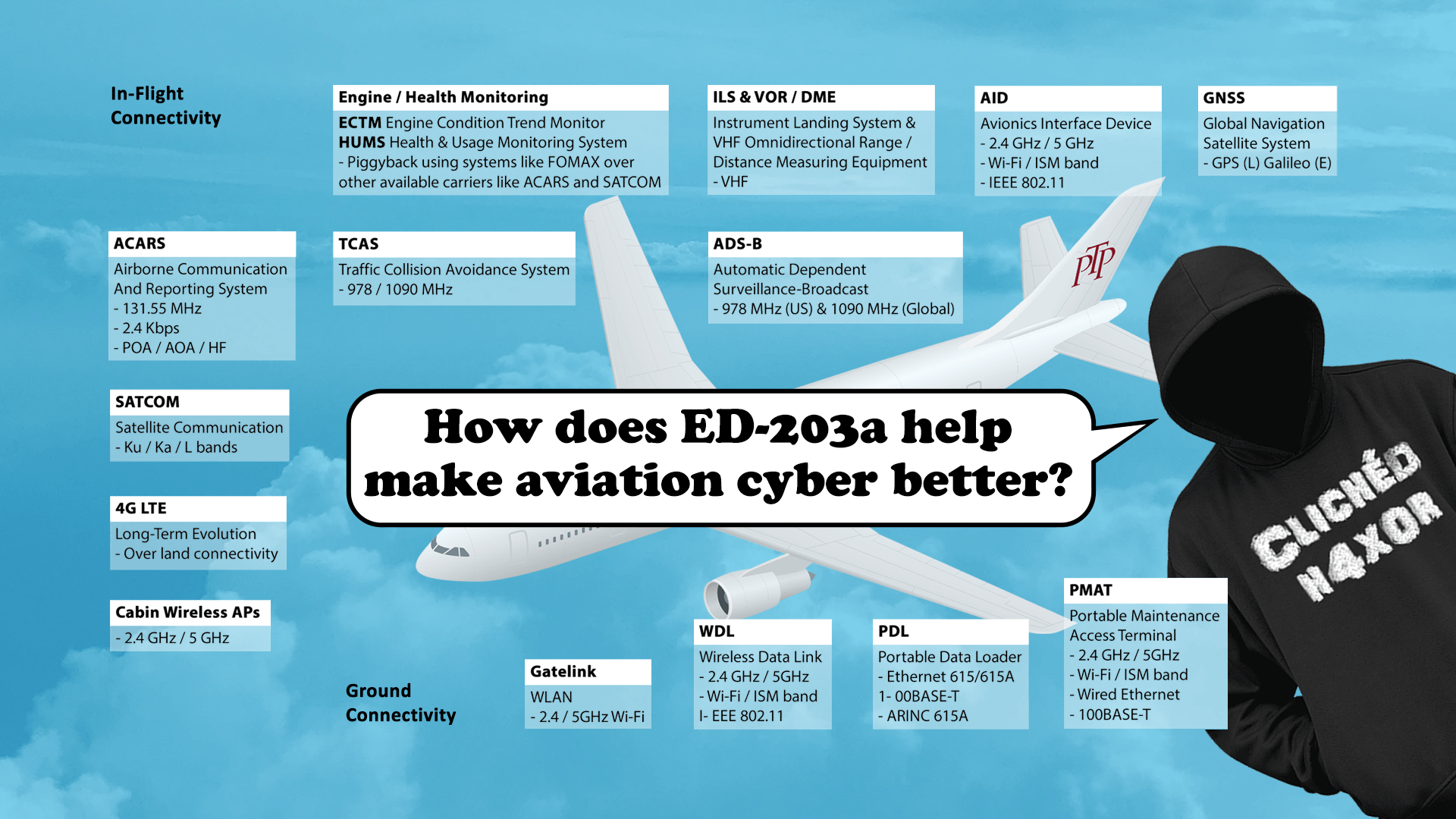
Transport systems are distributed, interconnected, and operationally constrained. Remote access is common, supplier support is baked in, and legacy and modern systems have to coexist. That means realistic security testing needs to respect safety and uptime while still answering the key question: what can an attacker reach, control, or disrupt through real operational paths.
Where we focus
We test the interfaces between onboard or operational systems, corporate IT, cloud services, and third party platforms. This includes the boundaries that tend to drift over time: remote support, integration links, management networks, and the parts of the estate that were never designed to be exposed.
Transport environments rely heavily on remote access for maintenance and support. We focus on the practical routes attackers use most often, including identity, access control, segmentation, and how third parties are onboarded and managed over time.
Where transport systems include operational technology, we design testing approaches that reduce operational risk. That can mean validating OT exposure indirectly, using representative environments, controlled testing, and evidence led assessment rather than high risk intrusive testing on live systems. PTP has written explicitly about this approach in maritime contexts, including the need to avoid destabilising operations.
Transport systems depend on specialist hardware and embedded components. We test devices, interfaces, and communications paths where weaknesses can create outsized impact, especially when they affect segregation between domains or enable pivoting from lower trust environments.