It’s increasingly difficult to buy home appliances and other tech that DOESN’T have connectivity. Despite reservations about the security of smart tech, if we want to buy mid to high end devices, we often have no choice but to buy appliances with connectivity.
To quote @Mikko Hypponen:

If it is smart, it is vulnerable

If you follow our thread on IoT security research, you’ll see why!
What’s the problem?
We all know that connecting IoT to the internet can expose us to compromise. So we don’t connect it, either because we don’t want to for reasons of security, or we simply never intended to. It was smart connectivity that we didn’t want, but had little choice.
Yet, leaving smart tech unconnected can leave us almost as vulnerable to hackers:

Consider a smart washing machine. By default, out of the box, it presents an open, unencrypted wireless access point.
This is necessary as the first step of connecting it as a wireless client on your home wireless network. After configuring, it will become a wireless client on the network.
But what if you never connect it? It’s still a wireless access point. It’s still open, still available to anyone nearby.
The SSID format is usually quite specific, easy to find using war driving databases such as https://wigle.net.
Here are a few examples of wireless enabled IoT devices in a default, open state. Bear in mind you’ll need to log in to wigle first:
- Kettles: https://wigle.net/search?ssidlike=ikettle%25
- Hot tubs: https://wigle.net/search?ssidlike=BWGSpa%25
- Google Chromecasts: https://wigle.net/search?ssidlike=Chromecast%25
- LG air conditioners: https://wigle.net/search?ssidlike=LGE_AC%25
- EcoWater smart water softeners: https://wigle.net/search?ssidlike=H2O-6c%25 (a small subset)
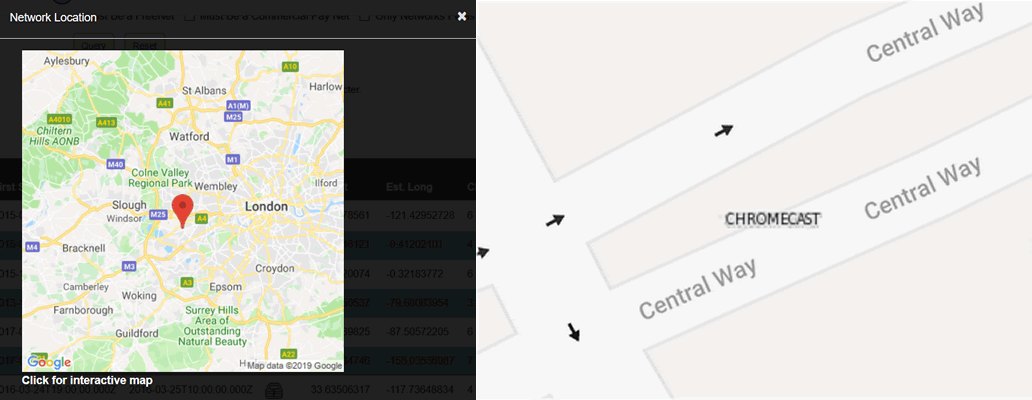
Here’s an open/default Google Chromecast in London (also zoomed-in to street level) for example:
Where it gets really silly is that it requires zero expertise to compromise these devices. Most of them will work both in access point and wireless client mode. So, all your friendly neighbourhood hacker needs to do is download the mobile app, connect to the AP on the smart ‘thing’ and they have control.
No reverse engineering required, just trivial remote control.
So what? Your neighbour can cancel your wash or maybe trash your clothes, or switch off your lights.
BUT
Smart devices in a default state are often missing important software updates as they’ve been sitting in the supply chain for a while. Or they’ve been sat in your home, unconnected for months. That means they’re more likely to be vulnerable and exploitable.
That creates opportunities for rogue firmware to be uploaded. Rogue firmware that potentially eavesdrops on you, modifies the behaviour of the smart device or perhaps worse.
Unconfigured wireless devices with a wired network port can also create back doors on to your network. Here’s an example of using a screencaster in unconfigured mode as a back door on to corporate networks.
Bluetooth is potentially worse than Wi-Fi

Whilst BLE may have a lower range than Wi-Fi, we’ve seen numerous devices that have no process for authenticating or authorising a new mobile device. Hence, anyone nearby can connect to your ‘thing’ and trivially take control.
Note, often the pairing process for lots of IoT is performed sideways to BLE – where the app call a backend API to state that it owns the device. So if you just send the raw data this is no defence – the device doesn’t care who owns it.
Some examples of extra steps for pairing over BLE:
- We’ve seen some devices that lower the transmission power during pairing. This means that you have to bring the device really close during pairing
- GoPro uses BLE security, requiring that the device is bonded – which means that encryption keys have been exchanged to do anything useful with it
OFF by default
Various regulatory frameworks are being introduced around the world. However, as far as I know, none specifically deal with the issue of unconnected devices. The UK IoT Code of Practice rightly addresses default passwords, but does it address open wireless access points in unconnected IoT?
I’ve seen a few IoT products that explicitly require the user to press a button to enable wireless connectivity, but they’re pretty rare.
I’ve seen a few that require a button press to enable Bluetooth during pairing.
But, the vast majority simply broadcast open access points over Wi-Fi whenever they’re powered on.
My proposal? All IoT devices should have their RF radios switched OFF by default

As connectivity becomes ubiquitous, consumers MUST actively choose to enable this. In its default state, the device is therefore much safer.














