This research is by @evstykas with help from @Yekki_1 and @TheKenMunroShow.
Many car insurers insist that smart trackers are fitted to high end vehicles. In the event of theft, the car can be tracked and recovered.
Probably the most well-known is LoJack, also known as Tracker in Europe. We also looked at TrackStar as it is approved by several car manufacturers for fitting by the dealer themselves.
Finally, we looked at SmarTrack. All three trackers were also accredited by the UK’s Thatcham Research vehicle safety & security research organisation. This was set up by many insurers to help drive vehicle safety and security. All three trackers were accredited to the ‘S5’ security standard.
We spent several thousand pounds having the trackers fitted to our own vehicles, so that we could carry out independent security research.
We had fun working with Scott Helme on this project, as he had a TrackStar device fitted to his car.
TL;DR?
All three tracker app APIs had authorisation vulnerabilities, which would allow a hacker or thief to take over the account, track individual cars in real time, suppress theft alerts and extract personal data.
Theft alerts could also be deleted, so if a car alerted as stolen, the thief could prevent further action
One tracking device could be remotely triggered to immobilise the vehicle, stopping it from being driven. Any car with this tracking device fitted could be immobilised, remotely, unauthenticated.
Conclusion: it would be trivial for a smart vehicle thief to prevent the trackers alerting the user that the car had been stolen. It may also be possible to prevent the vehicle being recovered.
The Thatcham accreditation appears to be ONLY about device functionality, not whether it’s effective, secure or introduces worrying vehicle safety issues. Thatcham appeared to be unconcerned about this when we reported it to them
LoJack/Tracker
The Tracker Touch mobile app allows one to locate the car in real time, also setting up a geo-fence. If the vehicle is moved, an SMS and phone alert is triggered.
If the owner confirms that the movement wasn’t intentional, then the police are alerted who go out to track and recover the car. That’s how LoJack get such a high stolen vehicle recovery rate.
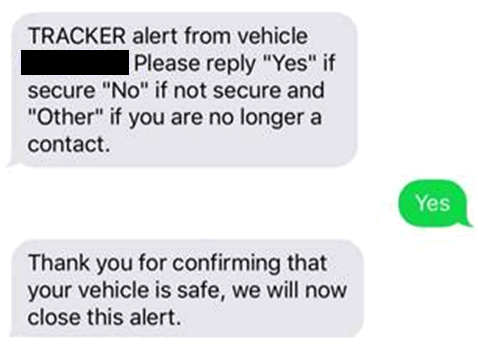
Account takeover
The mobile app API allows users to update their email address. The request to do this contains a numeric field – the ‘ClientId’ – that identifiers the user account. It’s possible to change this ClientId and change the email address for any account. The attacker can then trigger a password reset, receive an email to their own account, and then take full control. Only the thief will get the theft alert!

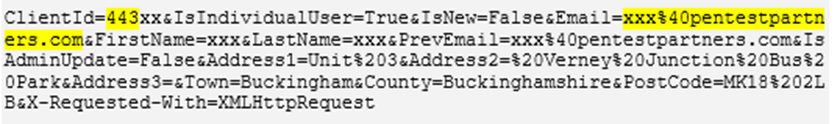
Track any vehicle
Now that the account has been compromised, one can track any vehicle in real time!
The vulnerability is an insecure direct object reference, one of several:
Delete ‘geo-fence’ alerts
If the car is moved outside of a defined area (e.g. your street) then that triggers a potential theft alert.
There’s a similar insecure direct object reference on the POST request for ‘UnsubscribeIndividualAlert’ allowing any theft alerts to be deleted as they’re issued. The case is closed and the police aren’t alerted.


Or you can do it from the web app, given the account is already compromised:
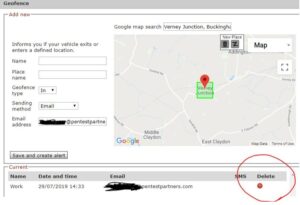
TrackStar account takeover
TrackStar doesn’t have as much functionality as Tracker. We only found one vulnerability on TrackStar, but that was enough. This request didn’t check that the user was authorised:
‘Subscriber_rno’ is an incremental number that gives you access to login, telephone number of all users, and allows you to remove all devices that are associated with the device.
Also, you can add your own device, which gives you the password for the mobile app (which never changes) and full mobile app access to all cars.
Then you can add & remove geofences, locate car, track the user in real time etc, just like Tracker.
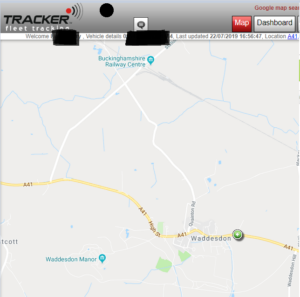
Here’s my car at our office:
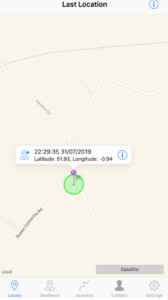
SmarTrack
Like TrackStar, the SmarTrack mobile app doesn’t have that much functionality, but still provides tracking and geo-fencing of your vehicle.
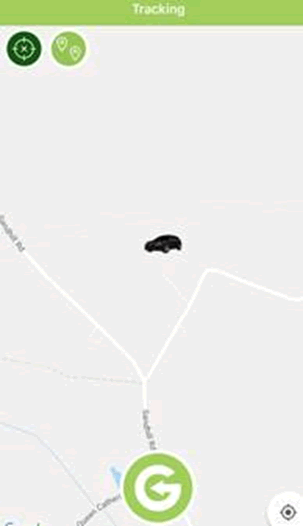
That’s one of our cars at our office.
Delete geo-fence
Here’s a similar insecure direct object reference, so one can simply delete the geo-fence and a theft isn’t triggered.
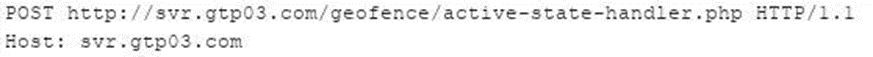

Authorisation checks aren’t applied to this request, so the geo-fence email alerts are switched off. Car stolen? No alert.
Yes, that’s an HTTP request too.
Possible SQL injection
One path on the telematic API endpoint server (https://svr.gtp03.com/1) appeared to host a backup file that was not correctly processed. The code seemed a little naïve in terms of security: raw database requests were passed with no filtering to the underlying database
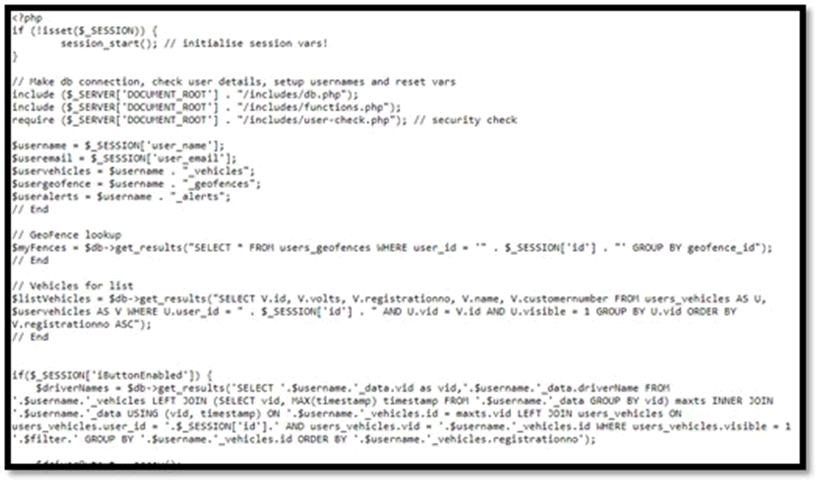
Whilst this is probably a backup to the main site, we’re confident that it would be possible to bypass authentication, but haven’t proved it as we don’t want to go exploiting SQLi without permission
Global fleet immobilise?
This path was a little concerning:
http://svr.gtp03.com/instant_immobilise/instant_immobilise_handler.php
It’s supposed to be the call centre that triggers vehicle immobilising at the request of the police or owner. Based on what we’ve seen already, it should be possible to immobilise EVERY vehicle with this tracker fitted.
To prove the point, we sent the command to immobilise our own vehicle.
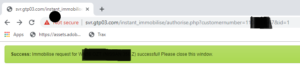
And then our car wouldn’t start. It took less than a second for the immobiliser to be triggered. The only way to resolve this would be to have the tracking device physically uninstalled.
And that’s @Yekki_1 ‘s car remotely immobilised, unauthenticated. I was in Greece when we did this and the car was in north Bucks, UK. Next time @thekenmunroshow asks if we can fit a immobiliser to your car for research, just say no!
This could be a real safety issue for cars with engine stop/start – the immobiliser is activated, the driver pulls up to traffic lights, the engine automatically stops & now won’t start again.
That is crazy – why on earth is this function on a public server?
Disclosure
LoJack were a little slow to respond. We had contacts at the US HQ via our work on the Viper alarm, but we had no response. Then we got hold of the UK operation, who did get back to us.
Viper is owned by Directed inc, who implemented an API from Calamp in the Viper alarm. Calamp own LoJack and also Tracker.
As far as we could make out, the API vulnerabilities were present only in the European implementation of Tracker, probably a legacy issue. The offending API endpoint for LoJack was hosted at calamp-ts.com, which you may remember from our smart alarm work. However, the European environment was hosted separately.
As a result, the LoJack flaw was unintentionally (?) fixed when we reported the Viper flaw back in February, but wasn’t fixed in LoJack/Tracker’s EU environment
Tracker UK took action and fixed the bug in Tracker just prior to public disclosure.
TrackStar is owned by Teletrac Navman, part of Fortive, an S&P500 conglomerate
We sent them an email but had no reply initially. After a little poke on Twitter and one of their execs in the US stepping in, we had a constructive call with the UK operation. The vulnerability was mitigated within 30 minutes.
Cool vendor!
SmarTrack is owned by Global Telemetrics, a UK firm.
We contacted Global Telemetrics by email asking for a response. We then called customer services, who explained that the relevant department would get back to us ‘if they were interested’
We had another reply a couple of days later stating that they had engaged a 3rd party cyber security company to review their security. That’s fine, but it doesn’t address the pressing security issues.
We needled them on Twitter too, which had an unexpected result: we had contact from another security professional who it transpired had just been engaged to review their security.
Once we had contact with him, everything changed: With some serious hard work on their part, all the bugs we reported were fixed in 48 hours.
Independent accreditation by Thatcham Research
The UK insurance industry relies on safety and security ratings given to vehicles. This information issued to set insurance premiums.
This includes crash-worthiness, resistance to theft and even rates cyber security of vehicles.
Hence, Thatcham is seen as an independent body, helping to drive forward safety and security. Much of their work has been of great value, undoubtedly saving lives.
However Thatcham also accredits car trackers, in the case of these to their ‘Category5: Stolen Vehicle Recovery’ standard:
“Thatcham Security Certification is a robust verification programme for the assessment and recognition of automotive security products. The certification concentrates on verifying functionality, design and performance of a product.”
We have serious concerns that these products have been certified by an independent expert body. They do not perform the functions intended in a secure manner.
Thatcham gave this statement to us:
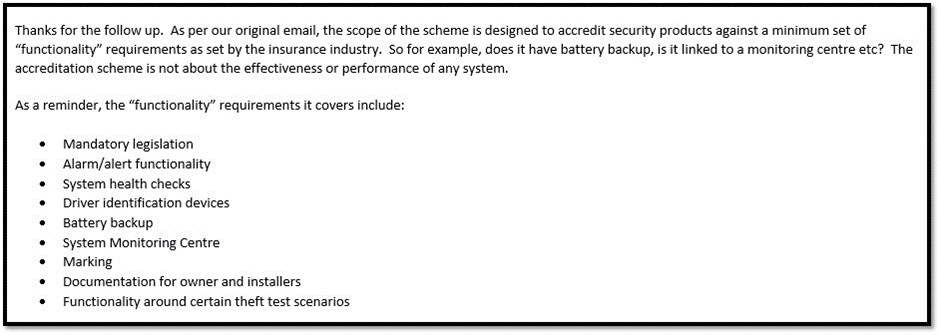
The security flaws were only identified through our intervention. We have only looked at a subset of the accredited tracking devices and have only carried out a limited range of testing.
We are very concerned that Thatcham have issued cyber security ratings for vehicles and question what value these have, in light of the glaring omissions seen above.
We also noticed that Thatcham are now publishing security ratings for cars, e.g.

How can anyone have any faith in Thatcham security ratings given the scope of the immobiliser certification process?
To Do
We haven’t looked at the firmware on the devices themselves, mostly because we didn’t want to accidentally immobilise one of our own cars and get stuck at work, unable to drive home!!
However, now that we’ve completed the API testing, we will likely remove the devices and see what else there is to find.
There are interfaces with the vehicle CAN for example to facilitate remote immobilising of the car.














