I’m a sucker for a good documentary, but the recent Netflix MH370: The Plane That Disappeared had me shouting at the screen.
The first episode talks about the most widely accepted theory; a tragic pilot-created murder-suicide. The second episode discusses a scenario where Russian special operations potentially hack the plane. The conspiracy theory was that it was to distract global media from the 2014 events in Crimea and eastern Ukraine.
Yes, there is a point at which the journalist presenting states that it is far-fetched, but the visuals of a hacker connecting to the flight control systems in the avionics (Electronic and Equipment or EE) bay are what the audience will remember. I’m talking about this because that narrative is misleading and doesn’t stand up to scrutiny. It also reinforces unhelpful myths about airplane hacking.
Why ‘unhelpful’?
The documentary states that the Boeing 777 has a critical flaw; that the EE bay hatch is located in the passenger cabin. Yes, but so does the 747, the A380 and so do other types.
For example, the upper avionics bay in the A380 is behind a locked door in the starboard side restroom, as per this photo I took a while back:

This is the EE bay hatch in the floor on a 747:

The documentary proposes that one of the Russian team created a ruckus of some description. This was a distraction so that a member of the team could slip forward unnoticed. They then lift a hatch in the floor to access the EE bay. Once inside they close the hatch, and the carpet on top of the hatch magically falls back into place.
While it’s a nice plot development it’s also virtually impossible. We’ve been in and out of enough 747 and 777 EE bays to know that it can’t be done unnoticed. The carpet would be noticeably displaced; a warning sign to trained crew. The hatch aperture is also awkward and cramped, so is not easy to get in and out of quickly.
It’s also worth noting that an EE bay would be an unpleasant place to be in flight. They are extremely noisy owing to cooling ventilation, are very cramped, there are lots of exposed edges and its easy to injure yourself, even when on the ground. Add a bit of turbulence and you’re in trouble:

Back to the story. So now the hacker is in the EE bay, and this is where the story goes bananas. Using a simple, unspecified cable connection they plug a laptop into the plane systems and proceed to do all sorts of fantastical and, in our expert opinion, impossible things to the plane. In the story this one cable connection enables them to make the plane vanish from radar and allows them to take control of flight systems:
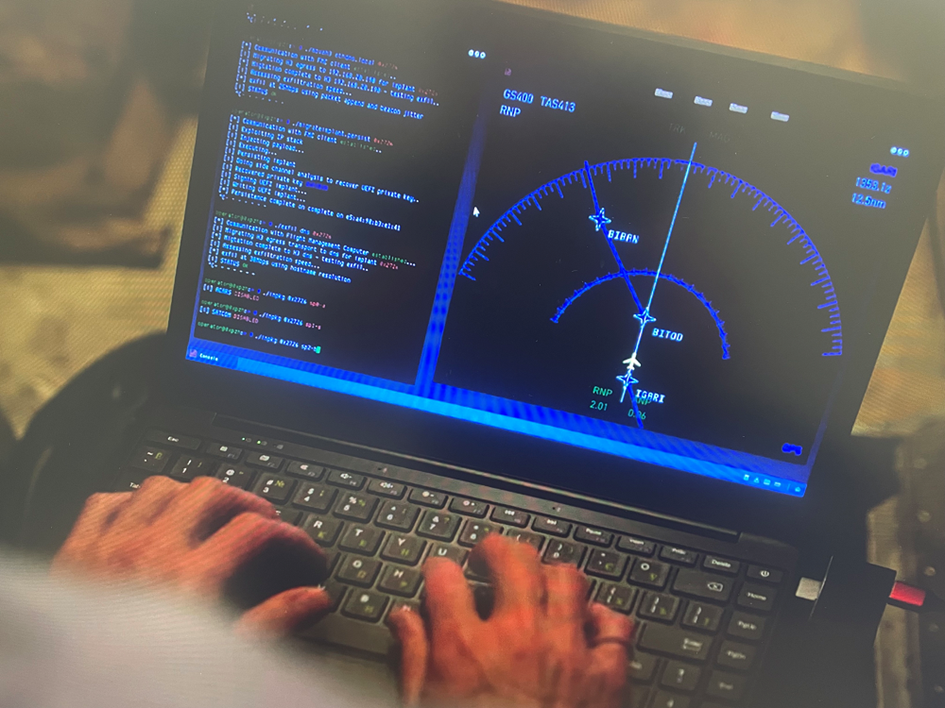
Let’s pull this apart…
The Boeing 777 is unique in that it uses a control protocol unlike any other, ARINC 629. Nearly every other plane uses ARINC 429. Some much newer planes (e.g. B787 and A380) use a newer ethernet based protocol called AFDX or ARINC 664.
ARINC 629 was developed partly in order to reduce cabling weight. ARINC 429 was less of a network, more point-to-point cabling. Hence the cabling weight was significant. ARINC 629 moved to an inductively coupled bus network, offering very significant cable saving.
Being an unusual protocol makes it harder to interface with. Something as simple as a PicoScope can decode ARINC 429. To decode and inject ARINC 629 is another matter. Decoders are hard to source and expensive. We’ve used a MAX Technologies FlexMulti 629 before, but it cost around $30,000 and it’s bulky.
Here’s my colleague, pilot and fellow aviation cyber researcher Alex on an A320 with the FlexMulti a little while back, just before injecting some traffic on a retired plane that was part dismantled. You can just about make out the engines on cradles in the background:

So, decoding and injecting traffic on to a B777 takes more than a laptop. It needs a highly specialised technical device that is about 17.5 inches long, 10 inches deep, and weighs nearly 8 pounds PLUS a laptop, and a selection of cables. It may also require injecting traffic on to multiple networks concurrently, with millisecond precision, owing to the multiple redundant flight control systems.
Back to the story again. In the EE bay the video shows the hacker connecting to a Line Replaceable Unit (LRU). That’s kind-of plausible, except that the connector they show looks absolutely nothing like any available avionics connector.
Could you load new, rogue software on to the LRUs? Very unlikely in the air, as without Weight on Wheels (WoW) i.e. being on the ground, updates are very unlikely to be accepted. Later airframe types will require digital signatures, without which the updates will be rejected by the LRUs. This would also likely require compromise of the onboard Maintenance Access Terminal (MAT) which is usually located in the cockpit of a 777. Here’s a photo:
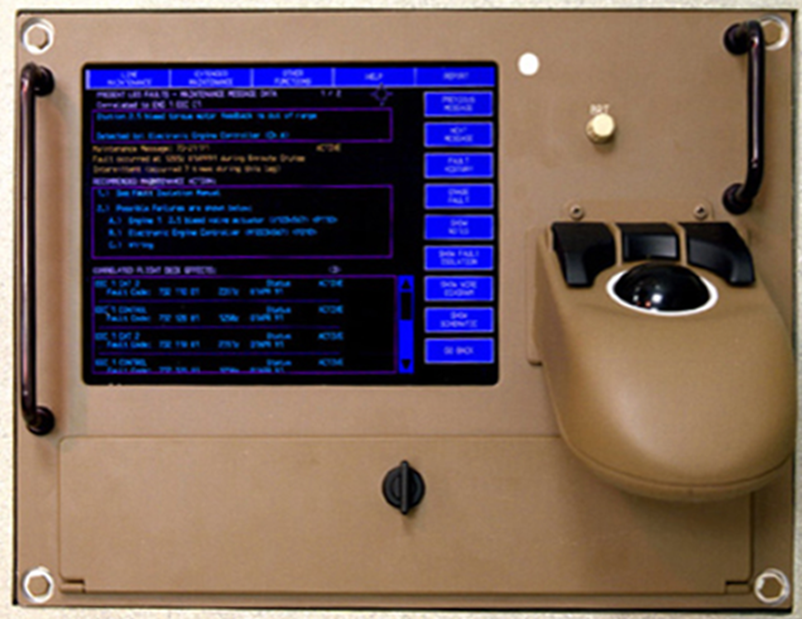
Now, the 777 MAT above is based on a CMC Electronics PilotView CMA-1410 which we found vulnerabilities in when used as an electronic flight bag, but not as a MAT, so no dice there Netflix!
The story also suggests that the hackers made the plane appear to turn south through giving out satellite pings, whilst it actually turned north. The plane also went radio silent and stopped giving automatic position updates. This isn’t easy to do from the EE bay: Simply removing several of the LRUs would have the effect of ‘silencing’ the plane. However, there would be critical ‘tells’ that would alert pilots and potentially ground staff too.
The radio and ADS-B LRU would be easy to unmount However, alerts would ping up on the pilots ‘ECAM’ system in the cockpit. These alerts would almost certainly be sent immediately to the airplane operator on the ground over satellite communications. It wouldn’t be anything like as easy to silence the satcom connection concurrently, as the satcom LRUs are usually elsewhere on the airframe.
The pilots would quickly be alerted to systems misbehaving. A visit to the EE bay would be swift.
Silencing multiple communication systems concurrently without any alert to the pilots or ground stations is, in our opinion, beyond the bounds of possibility.
Overpowering the autopilot
The ‘hack’ suggests that the autopilot had taken control through a compromised laptop. Again, this is where the design of the 777 doesn’t lend itself to such an attack. Boeing aircraft have yokes for the pilots. Now, the 777 does have fly-by-wire systems that are computer controlled, however even these have mechanical backups to certain of the flight control surfaces. Spoilers 4 and 11 are mechanically connected to the yokes and to the speed brake lever in the cockpit.
In the ‘hack’ scenario, it is shown that the laptop takes control of the plane flight systems and autopilot to make it turn. There are safety controls that would prevent this: The autopilot will initially resist the pilots correcting input from the yoke until sufficient force from the pilot is felt. After that the autopilot will disengage. Hence, taking control of the autopilot wouldn’t give the attacker control of the plane.
That laptop screen
Our experience with the equipment, technology, and protocols used in aerospace means that we have a privileged perspective. I appreciate that artistic license needs to be taken by documentary makers, it helps make complex subjects and topics accessible to everyone. It doesn’t mean that the same old hacker tropes have to be rolled out though.
They zoomed in on the laptop screen showing references to ‘UEFI BIOS’ and ‘DNS exfil’ which just aren’t relevant to an attack on an aircraft’s LRU. Those are attacks that would be carried out on a ground-based network, not in an airplane. It would be more correct, and likely more interesting, to show some ARINC 429 or 629 data displayed.
Conclusion
This style of attack is so implausible as to be impossible. Nothing about it stacks up, nor is it supported by technical detail. It’s unhelpful to suggest that airplanes could be hacked in this way.
Worse though, it can come across as misleading. The flying public would benefit from the full story and the truth about how likely the scenarios really are. They need to know about the work being done behind the scenes to prevent even the most fantastic and dangerous scenarios from occurring in the real world.
Netflix, if you want to learn more, read our blog and follow the Aerospace Village.














