One of the biggest challenges with avionics research is simply getting hold of equipment to work on.
Current equipment is frighteningly expensive – think $100,000 and up for some components, reflecting the relatively short production run, high reliability requirement and significant certification costs for many avionics.
Some used components are available from breakers yards, eBay and other sources, but these are typically 10+ years old and not representative of current avionics security levels.
Yes, old components are often backward and forward compatible with newer avionics, but finding that for example a trusted execution environment and signed firmware updates aren’t present on a 12 year old MCDU is hardly interesting.
So, unless you have a friendly airplane or avionics manufacturer prepared to loan you $1M worth of stuff to play with, where do you go next?
OSINT
What can we learn about avionics security from open source resources?
First, the usual: we can discover from vendors press announcements which contracts they have won from which airline.
I’m no fan of security by obscurity, but why make it so easy for the attacker to identify which avionics components are on board in advance?
It’s also trivial to identify members of staff and their responsibilities from social networks such as LinkedIn. Want to coerce an airline avionics engineer? Now you know who to target
But one of the most revealing sources is the Federal Communications Commission. From our work on embedded systems and IoT, we use the FCC site a lot to identify potentially vulnerable components in IoT before we decide to buy the kit to reverse engineer.
For example, we were very interested in the rather cool British Airways smart baggage tag. Before buying it, we wanted to know what was on the inside. Was it going to be interesting enough to reverse engineer?
The FCC ID is NOI-VGIDEBT. The embargo on internal PCB pictures lifted just before the first units shipped to the public, so now we have access to the following images:
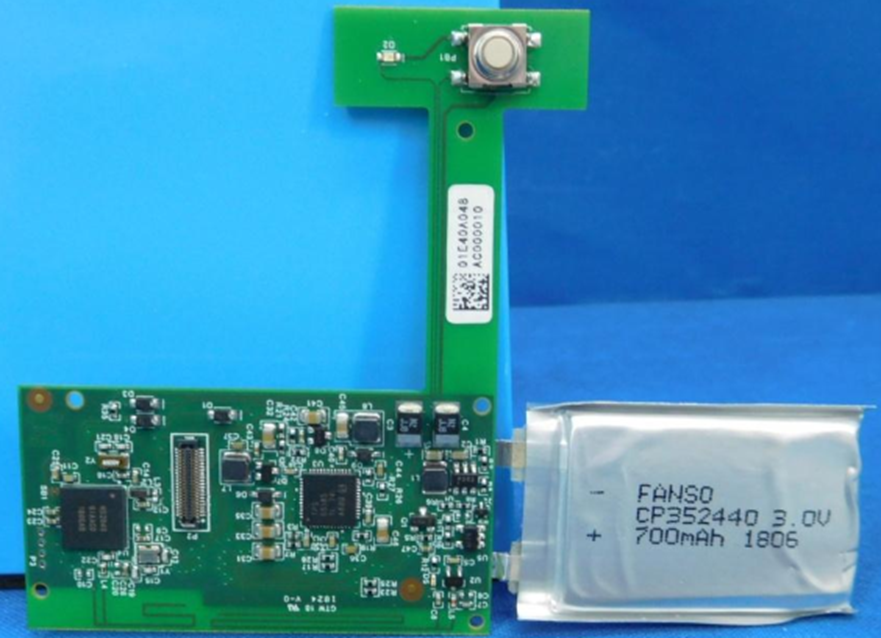
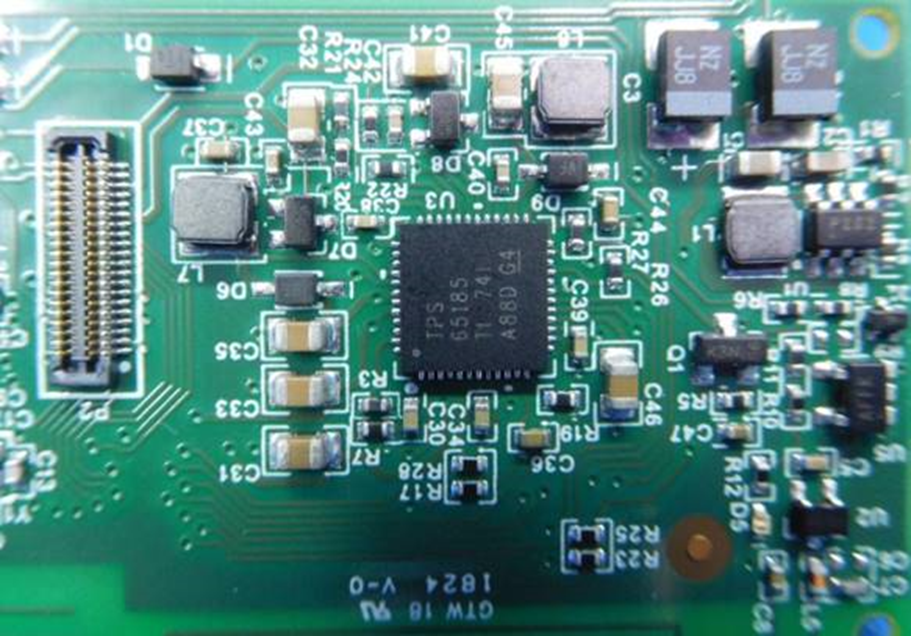
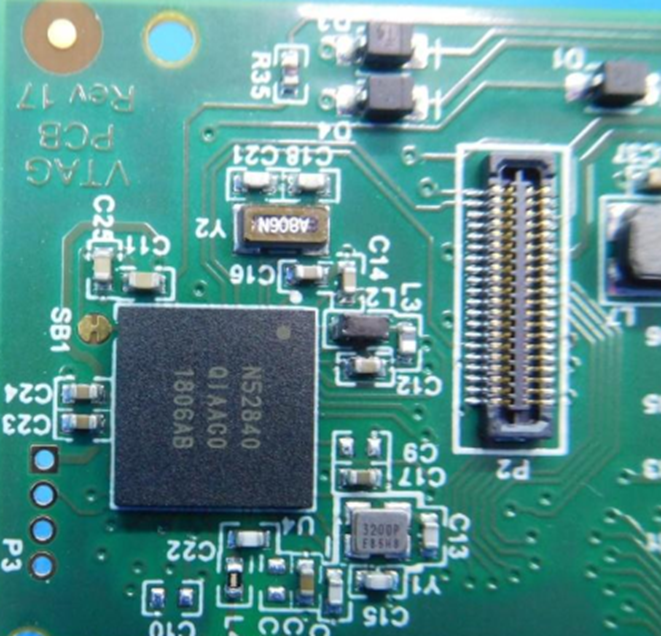
On the bottom left of the 3rd image is a programming port – the four ‘holes’ surrounded in copper. You may notice that the top hole is top squared off, which makes that pin one.
The four holes, and that as it’s a Nordic/ARM chip, indicate that the programming port probably uses SWD as a protocol. The top is +3.3v power and the bottom is ground. The middle two will be SWDIO and SWCLK.
The part numbers on the chips are also useful, as is the type of connection:
TPS65185 – that’s a Texas Instruments PMIC that drives the e-Ink display
N52840 – this is a Nordic Semi nRF Bluetooth chip. This gives us lots of useful information about the protocols in use, the age of the chip and potential vulnerabilities that it might contain
By looking at the back of the board, we can also start to work out trace paths that will be useful when figuring out how the Nordic Semi chip connects. Its pins are hidden from view as it’s a BGA (Ball Grid Array) package.
So, what about avionics?
Any device that emits RF must be approved by through FCC accredited test programmes. During accreditation, a test report is created by an approved test lab.
The test process includes review of schematics, emissions, manuals and photographs.
Believe it or not, useful data is often disclosed in FCC filings, available for all to view. Whilst schematics are usually kept restricted from public view, photographs are not. Occasionally, the manufacturer forgets to file for confidentiality so schematics are available too.
What did we find?
We started by thinking about which avionics components would emit or receive RF. A starting list included: ACARS, ADS-B, SATCOM, TCAS, WQAR, PMIS
Hunting across the FCC site revealed a surprising number of components. Here are a few examples of what we found:
ACARS
A fascinating ACARS receiver from SpectraLux:

ADS-B
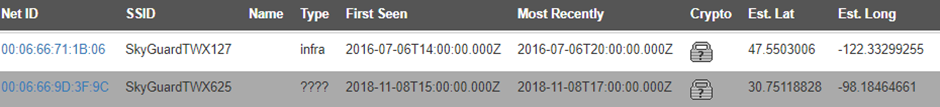
Internals of an ADS-B transponder from SkyGuard (https://fccid.io/R83UAT1000/Users-Manual/Users-Manaul-Rev-4-1997896). This is interesting as it’s an all-in-one package of of an ADS-B transponder (UAT) and GPS “Extended Squitter” (ES) in a portable package which is designed for general aviation use. There is a drive in the USA and EU for private pilots to carry better electronic conspicuity aids, but that the hindrance has been certification and cost of built-in avionics, hence the development of these lower cost portable devices, although this particular one is no longer made or supported (see, aviation has just as much built in obsolescence as consumer gear!).

These devices also have a WiFi hotspot (with no authentication, but I guess there aren’t many people in range once airborne…) which is used for connection into an iPad or similar so the pilot can visualise the traffic data.
Wigle.net shows a couple of the devices, but not at airports for some reason!
Satcom terminal equipment
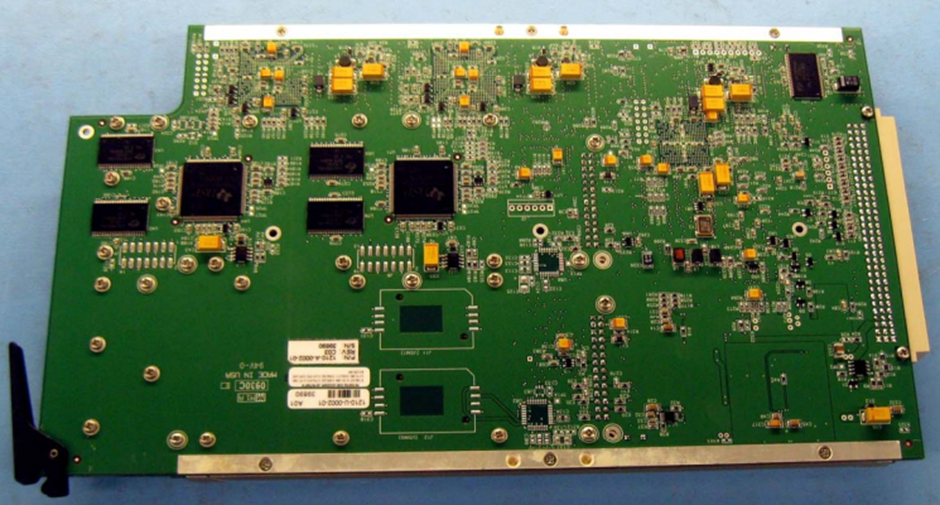
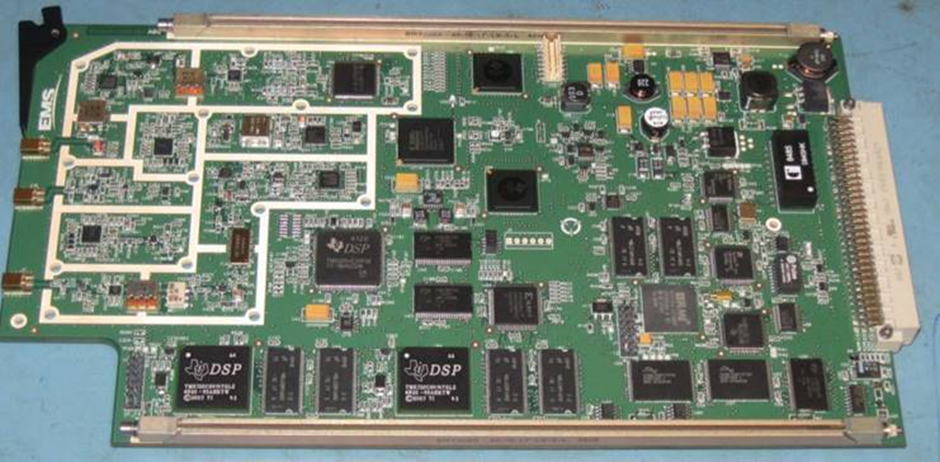
For one SATCOM unit (not one of the above) we obtained a user and installation manual through the FCC sites which made reference to a static, unchangeable, password protecting a local serial interface. Looking through other units by the same vendor, the same credentials are in use across a wide range of their products.
SATCOMs are interesting as they often sit connected to multiple aircraft domains, potentially bridging between the passenger and information/control areas.
TCAS
A Rockwell Collins / UTC TCAS
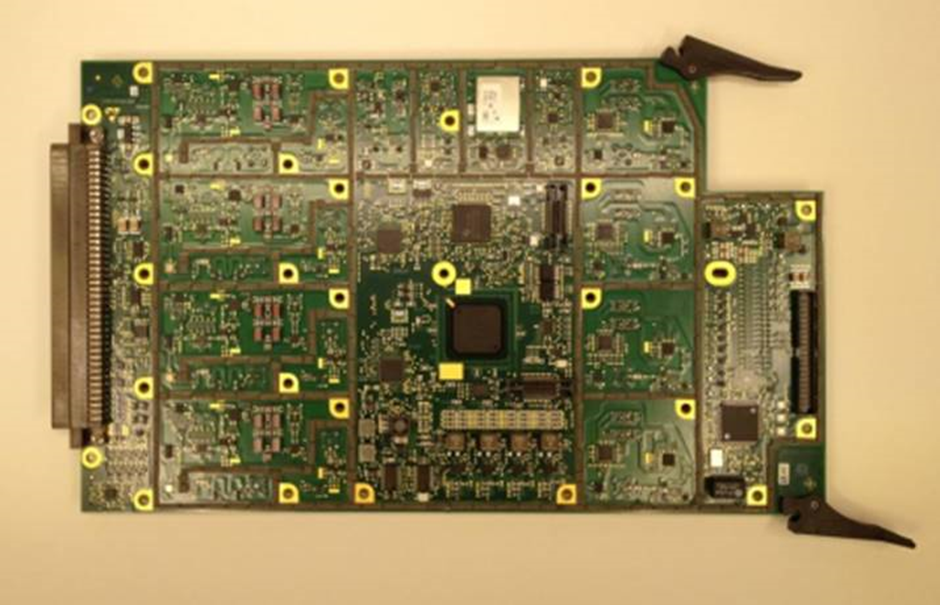
And a Honeywell TCAS
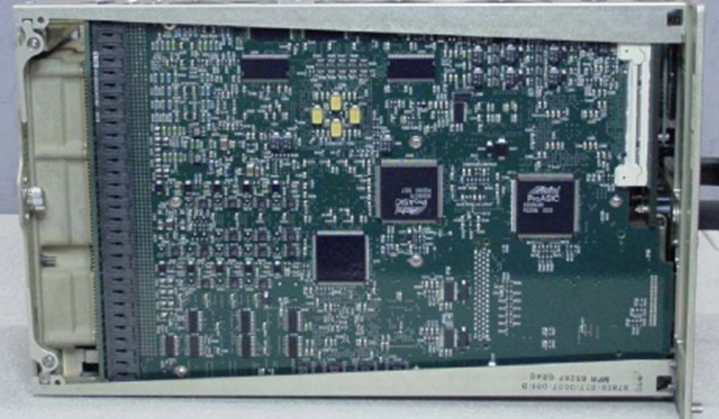
A Garmin GTS8XX

Now, the above images aren’t high enough resolution to determine much, but they’re still useful
Finally a high resolution image of Teledyne wireless Quick Access Recorder (WQAR)

Amusingly, the datasheet for Sierra AirPrime MC8705 modules (the two white vertical rectangles in the picture above) has a large warning not to use them on aircraft either on the ground or in the air ¯\_(ツ)_/¯

Metadata
A number of the PDFs we downloaded contained author and file path metadata inside them. Vendors and test labs should scrub these before submitting them to public sources such as the FCC.
Conclusion
We have only scratched the surface of the public information available about avionics components.
Given the sensitivity of these disclosures, I wonder if the FCC and FAA / CE and EASA should have a discussion about whether avionics accreditations should be suppressed from public access?
It’ll make our life harder, but also the job of the hacker.
Read more about our Aviation Cyber Security Testing services here.














