For a long time, the primary security model for airplanes has been physical. Airside security controls are there to prevent access by unauthorised personnel.

However, as connectivity with e-enabled aircraft has increased, for reasons of efficiency, safety and passenger convenience, the physical security model has been eroded.
Whilst press stories of ‘airplane hacking’ are often misleading, particularly owing to strong domain segregation, multiple redundant systems and human pilots in the loop, security of avionics and airborne networks is still essential.
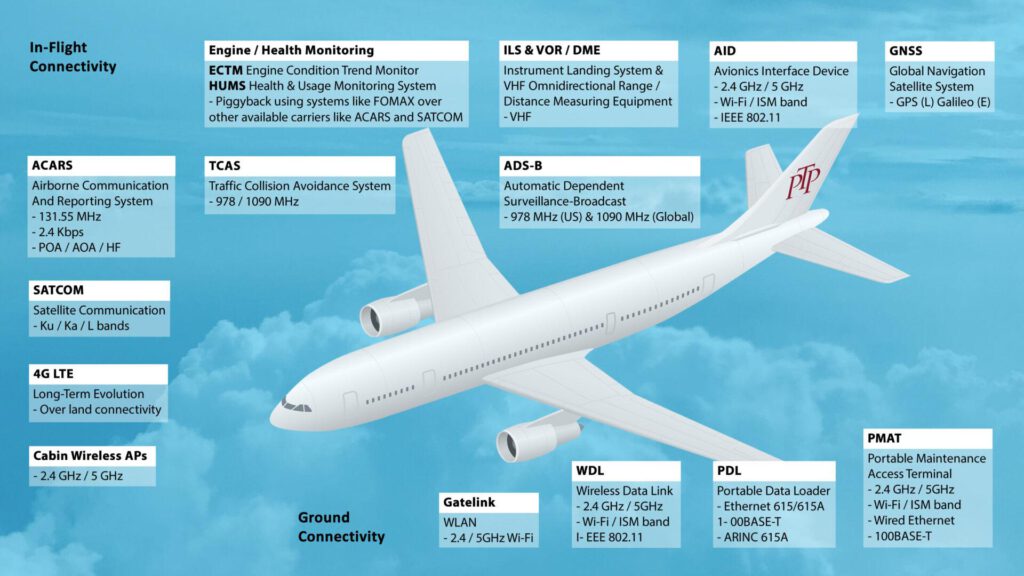
When on the ground an aircraft’s communications with the airport and their company are prodigious, using Wi-Fi and other RF protocols to exchange data, but also simple crew laptops/tablets and phones in the briefing room.

The attack surface of an airport is complex, very complex, and the biggest single challenge with aviation cyber security is the sheer volume of different entities that need access: passengers, crews, airline staff, security personnel, Police, Customs and other government agencies, freight, meal service and many more.
Electronic Flight Bags and Applications
EFBs are now categorised as “portable” or “installed” and can run different “classes” of applications. We’ve written extensively on the topic: https://www.pentestpartners.com/security-blog/efb-tampering-1-introduction-and-class-differences/
Regardless of the type of device it must be robustly secured against tampering and interception, whilst at the same time being available for the pilots to use quickly in an emergency.
Applications need to validate the integrity of data and updates, particularly for performance and weight & balance calculations.
We have loads of experience and can help both OEMs and operators to harden EFBs in line with AMC 20-25.
Aircraft Passenger Domain testing
Airlines, aircraft manufacturers, and avionics suppliers have all increased the availability and choice of equipment used in aircraft passenger cabins. Systems have been added to offer passengers on-board Wi-Fi, movies, live television, and even menu ordering and duty-free shopping. Testing of interfaces and equipment accessible or exposed to passengers is important to ensure the reliability of service, continuity of revenue, and proper segregation between other aircraft domains.
Aircraft Information Services Domain testing
Systems in the AISD are not safety critical but often have connectivity from or into the control domain, for example IFE moving map data and crew terminal access to company messages via ACARS. The AISD can be considered akin to a DMZ on a “traditional” network, however whilst it is common for there to be a network-level security boundary it is often left to individual units to implement their own protections.
It is therefore important to review any exposed interfaces that could potentially allow a pivot between domains, particularly where units bridge across them, such as SATCOM and wireless quick access recorders which can have GSM/4G connectivity for ground use.
Testing both of the above can be conducted in a “grey box” fashion with the penetration tester mimicking the action of a malicious or accidental passenger, but in a controlled fashion, on an active airframe or in a representative avionics test facility. Assessment is typically split into the following phases:
- a scoping and planning paper exercise with the customer to ensure safety and coverage to meet the testing objectives
- a reconnaissance phase whereby equipment, traffic, and interfaces are identified and profiled
- offline testing is then carried out (if possible) of likely targets with the aim of reducing risk to active service
- finally a full proof of concept test using knowledge gleaned from planning, profiling, and offline testing
Testing phases can sometimes be compressed depending on the objectives and equipment under test.
It is not possible to conduct testing of any part of an active airframe or its avionics that impacts on its certificate of airworthiness. Bench testing of avionics systems can still be carried out as long as these are not returned to service.
IFE security review
Seat-back inflight entertainment are the most exposed units to a potential malicious actor and whilst should be relatively standalone, or incorporate one-way connectivity to other systems, hardening of these devices must be performed to limit breakout, denial of service, and lateral movement. Reviews can typically incorporate a “kiosk” mode assessment, exposed ports (typically USB), and assessment of data lines available to seat boxes.
In flight WiFi reviews will examine appropriate segregation between passengers, and from passenger devices to crew devices, the infrastructure onboard (the satellite terminal itself, access points, and any caching appliances), content filtering, and to ensure that any walled-gardens cannot lead to revenue loss.
Satellite terminal security review
Review of hardware for exposed physical and management interfaces (e.g. serial, ARINC 429, telnet or web), hardcoded passwords, and firmware update mechanisms. Network configuration review to ensure appropriate segregation between any implemented VLANs (e.g. passenger and information domains), any exposed WAN-side interfaces, and of any ancillary antenna control systems.
Aircraft domain segregation review
Typically an initial paper-based review of systems, interconnections, and cable routes which is then followed by assessment of high-risk LRUs. This would examine deployed functionality and firmware, exposed interfaces, and any buses/protocols/virtual links exposed to other systems in other domains to verify message integrity and correct source/sink configuration, along with any network routing and firewalling configuration.
Gatelink wireless security review (aircraft and/or airside review)
Verify correct and secure storage of WiFi credentials in onboard units, along with update mechanisms. Determination of protection from typical wireless attacks include deauthentication and “evil twin”, verification of appropriate levels of authentication and encryption (e.g. 802.1x certificate verification or strong WPA-PSKs). Review of airport AP deployments including correct segregation of Gatelink traffic from airport corporate / hotel-side networks.
Avionics hardware reverse engineering
Reverse engineering of deployed technology stacks from part numbers, enumeration of chip-connection interfaces such as JTAG, SWD, UART etc. , attempts at firmware extraction/modification via debug interfaces or chip removal, verification of firmware update mechanisms/signing, integration with other systems/components.
Avionics network protocol review
Attempt to circumvent bus protections (sink to source etc) and resilience of units of replay of commands / injection of error messages.
Aviation RF security review
Resilience of protocols to spoofing and injection, and reverse engineering of proprietary encryption mechanisms layered on top (e.g. ACARS)
Dataloading / maintenance crew equipment security review
End to end process review, encompassing build reviews against engineering field laptops, deployment procedure gap analysis, and PKI for verification of navigational databases / LSAPs etc.
PDL / ADL embedded systems testing for compliance against ARINC 645-1.
Security testing for assurance purposes
This provides confirmation of the risk levels and that security controls have been implemented correctly, both to a standalone unit, and in its communications with other modules and services. This is typically in support of standards such as ED-204A.
Testing can be conducted as “closed box” – which determines risk from an attacker with zero knowledge, however “open box” penetration testing is normally preferred for testing efficiency whereby test harnesses, schematics, and code are provided. A blended “grey box” test can also be performed with both phases.
Especially consider any connectivity from the unit to other devices or interfaces, particularly maintenance ports/laptops, FMS and monitoring connectivity (such as FOMAX).
Debug and programming ports such as JTAG, SWD, SPI etc should be fused or otherwise locked in order to prevent tampering with the firmware or recovery of cryptographic keys from memory. It is also important to use MCUs that do not have known code readout protection (CRP) bypasses.
Testing should ensure that the debug ports cannot be exploited or CRP bypassed to recover sensitive data.
Reverse engineering of deployed technology stacks from part numbers, enumeration of chip-connection interfaces such as JTAG, SWD, UART etc. , attempts at firmware extraction/modification via debug interfaces or chip removal, verification of firmware update mechanisms/signing, integration with other systems/components.
Verify correct and secure storage of WiFi credentials in onboard units, along with update mechanisms. Determination of protection from typical wireless attacks include deauthentication and “evil twin”, verification of appropriate levels of authentication and encryption (e.g. 802.1x certificate verification or strong WPA-PSKs).
End to end process review, encompassing build reviews against engineering field laptops, deployment procedure gap analysis, and PKI for verification of LSAPs etc.
Attempt to circumvent bus protections (429/664 sink to source etc) and resilience of units of replay of commands / injection of error messages. Review of firewall protections (iptables/nftables in embedded Linux).
Review of hardware for exposed physical and management interfaces (e.g. serial, ARINC 429, telnet or web), hardcoded passwords, and firmware update mechanisms. Network configuration review to ensure appropriate segregation between any implemented VLANs (e.g. passenger and information domains), any exposed WAN-side interfaces, and of any ancillary control systems.
How we can help you
Creating a security strategy will improve your posture. We have engineers and pilots on our team, so we understand airports, aircraft, and all things hardware.
Working hand-in-hand with airport cyber security teams we can help identify vulnerabilities and process gaps to improve your resilience to the myriad of threats that you face.
By emulating bad actors we can perform tactical security audits of your aircraft, hardware, and land-side operations to identify the ‘easy wins’ for security in the short term. Reviews of systems and software before deployment to an airline fleet can save significant time and money down the line.
Transport

Free Pen Test Partners Socks!!!
Pen Test Partners socks are THE hot security accessory this season, if you're a security professional get yours now!