Introduction
We’ve been advocates of regular password auditing for years. Over that time, we’ve noticed that password choice is not only very personal, but hugely influenced by current events, trends, and even what’s sat on your desk. It’s given us a unique opportunity to see these common influences reflected in the passwords that we’ve cracked.
Bearing that in mind it’ll come as no surprise that the pandemic helped form some people’s passwords, and a certain government advisor’s misdemeanour (driving to ‘test’ his vision) even influenced choices.
Lazy humans
If users are not choosing passwords based on their favourite football team, or current city, they are choosing words like wedding, and Christmas when they are on their mind.
The problem is that humans want convenience. We firstly want a password that’s easy to remember, so we tend to choose a word. Then we remember we need to make it secure, so we capitalise the first letter and stick a 1 at the end. Brilliant – it passes the password complexity requirements!
Sometimes people swap some of the characters with numbers, letter, or symbol look-alikes – it’s known as l33t or 1337 speak. Our dedicated password cracking servers can try billions of permutations per second. It doesn’t take much extra effort to try a “3” in place of the e’s, or a “0” in place of the o’s. Swapping an replacing characters like this just makes a really weak password slightly less weak.
Erm…. other Humans

Nobody gets hacked.
To get hacked you need somebody with 197 IQ and he needs about 15 percent of your password.

The President of the United States of America, October 2020.

Sorry Donnie, that’s just not how it works.
Specific humans / eye tests
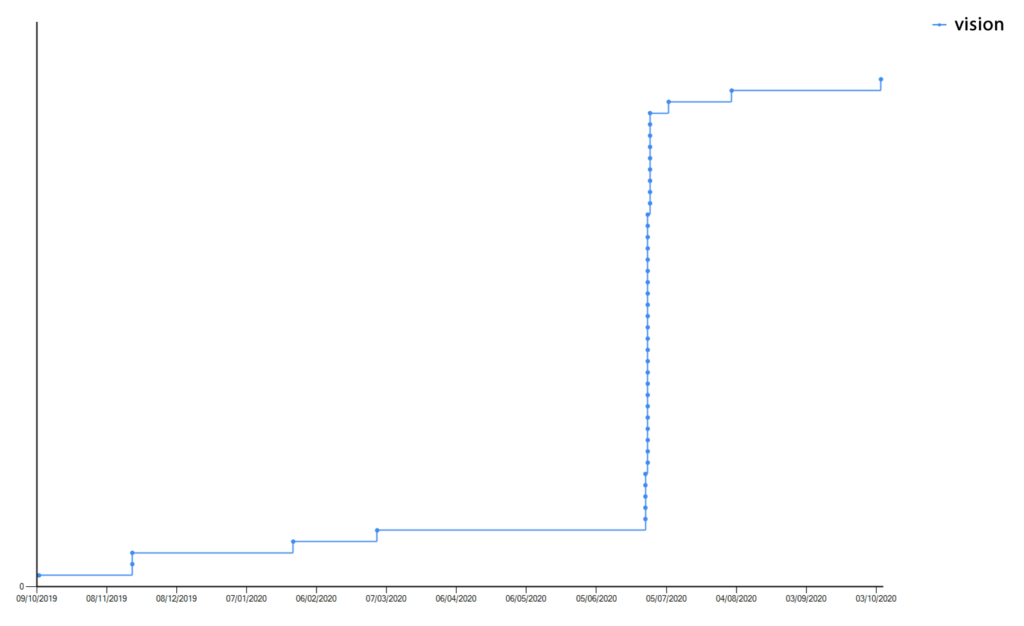
One thing that our data highlighted was passwords based on the word “vision”. There was a huge spike after the Spring lockdown in the UK, but why?
Everyone was supposed to be staying at home. Ministers, government advisors, everyone. If you wanted to have your vision checked with an eye test you couldn’t.
No one was driving anywhere to check their eyesight, not even to beauty spots in Teesdale like Barnard Castle.
…or were they?
Influences
We have an in-house developed software product called Papa that is used by our consultants, as well as our customers, to perform password audits of Windows domains. Papa can identify base words that are used within an organisation, and see how that trend changes over time. The tool can reverse what the lazy humans have concocted and un-l33t speak passwords. That then allows it to do base word analysis.
At the PTP server end, we don’t get to see the same level of detail, but because we keep a list of cracked passwords, and we know when they were cracked, we can do somewhat fuzzy analysis across all of the passwords.
At this scale it’s impossible to see influences at the organisational or individual level, but during a pandemic when everyone is thinking about similar issues, that influence does seep into password choices that we can see at the back end. When we look for words like covid, corona, and lockdown we can see them appearing right around the times we’d expect.
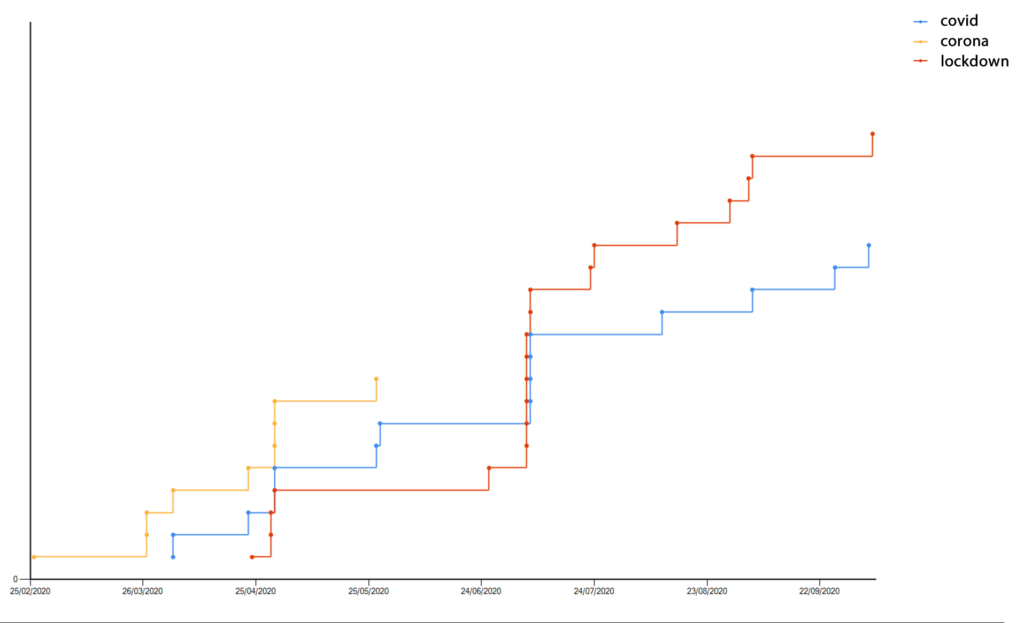
During February and March, most people referred to the virus as Corona, or Coronavirus. The prevalence of Covid-19 didn’t take hold until a month or two later, and we see the yellow “corona” line appearing before the blue “covid” line. As we move forward in time, we can see the “lockdown” series in red having more of an influence in our poor choice of password!
If we add in the words, “computer”, “phone”, and “office” and adjust the scale to the previous 12 months, we can see that as people started to abandon their offices, the influence of these types of words radically declines, and the line flattens.
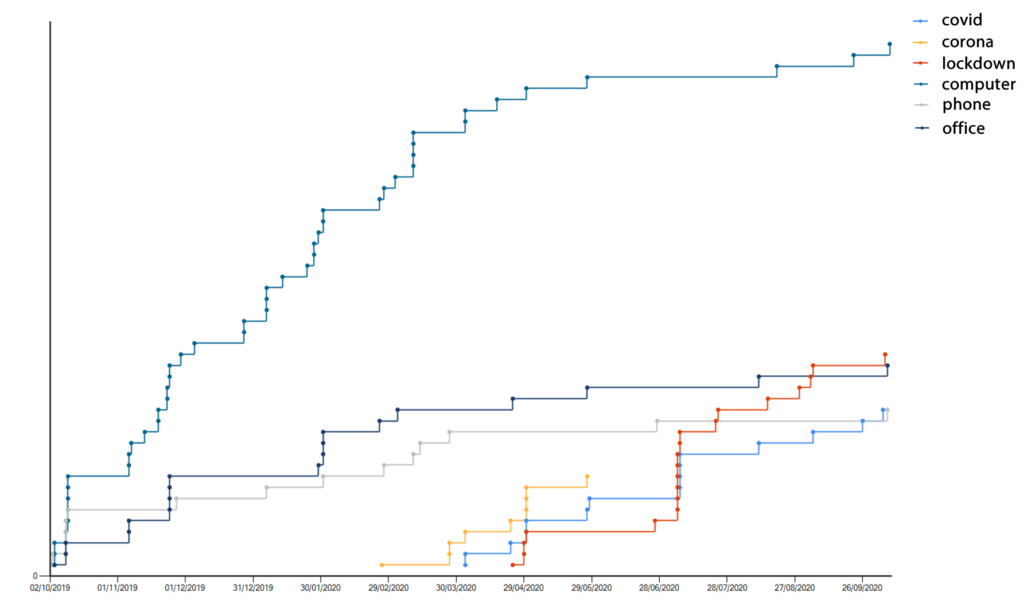
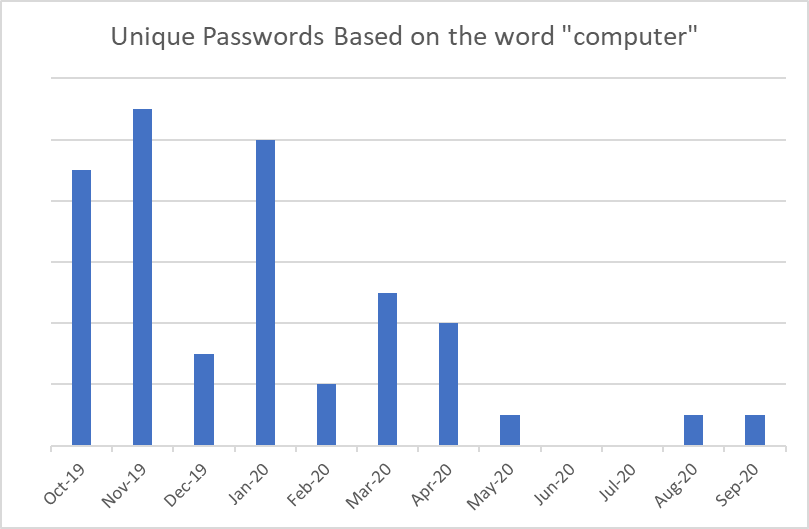
In the last 5 months, we’ve seen 3 new passwords based on the word “computer”, but in the 5 months before lockdown there were over 30. It could be because people call laptops “laptops”, and the rows of office desktops are out of sight. The same rapid decline is also true for “office” and “phone”.
Naughty hoomans
We know we shouldn’t… we know it’s naughty, but we still choose passwords based on the word password. How big of a problem is it… well, if we add passwords based on the naughty word, then we see this:
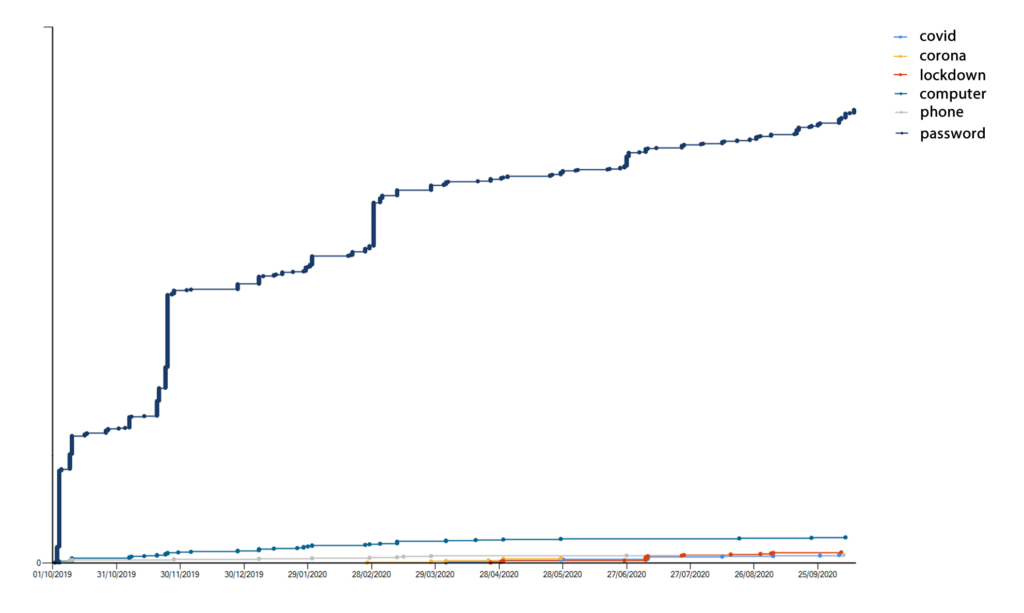
It completely dwarfs the other trend lines. In the past 12 months we’ve cracked 845 new variations on the word “password”, and there are now around 6,000 variations in our database. If you try “Password1” against every user on a large domain, there is a good chance you’d compromise a domain account. It’s just that common a mistake.
Conclusions
Passwords are, unfortunately, still something we use to secure our data. We’ve tried to bolster them with 2FA, and we’ve tried to make them more complicated, but they are still a weak point that is actively being exploited.
- We need to stop using passwords based on a word – especially words based on current events, or things around you. L33t speak doesn’t really help.
- IT departments should be encouraging users to use a password manager. I often find passwords stored in cleartext files on network shares. At PTP our IT team install a password manager on every corporate laptop they build.
- Don’t expire passwords. NCSC now recommend that passwords don’t expire. It can encourage users to choose easily-remembered passwords. Let them choose a strong password and if it’s strong, don’t expire it.
- Perform regular password audits with a tool such as Papa – we recommend monthly.
References
- PTP Advanced Password Auditor (Papa) – https://www.pentestpartners.com/penetration-testing-services/papa/
- NCSC Password Tips – https://www.ncsc.gov.uk/collection/top-tips-for-staying-secure-online/use-a-strong-and-separate-password-for-email














