TL;DR
- The game Cultist Simulator by Weather Factory trusts executable mods
- Mods can be installed from the Steam Workshop with a single-click
- Mods need to be enabled before they are executed
- Could allow full executable access to a player’s user and computer
- The vulnerability was “patched” by require a plugin to be installed
Remote Code Execution in Steam Workshop items for Cultist Simulator
CVSS 7.6 (High severity)
CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:C/C:H/I:H/A:H/E:P/RL:U/RC:C
Version: 2022.09.i.6
The game Cultist Simulator by Weather Factory is a card game developed in C# and playable through Valve’s Steam front end. It offers workshop support for Steam, allowing mods to be downloaded and enabled through the Steam front-end.
Upon examination of the game’s mod structure, it was identified that the game allowed mods to include DLL files, which can contain any valid .NET code, with no restrictions on what can be run. After installation through Steam, the mod needs to be enabled within the game and the game restarted. After this the code within the DLL would be executed as soon as the game was spawned.
A proof-of-concept was created which would create an instance of Windows calculator whenever Cultist Simulator was run. This was uploaded to the Steam Workshop and then subscribed to using the Steam frontend. It was enabled within the game and the game was restarted. This caused calculator to spawn.
Any code would run as the active user. An appropriate agent could allow access to all files and the registry as if they were running as the active user.
Steam does perform some basic checks when a file is uploaded to the workshop which did not highlight this mod.
This was fixed by the developers by requiring another mod, GHIRBI, the Gatekeeper to be installed to allow .NET code to be enabled. This is a suboptimal solution, as a malicious mod could just require this mod to be installed.
Timeline
2022-09-21: Vulnerability identified and PoC developed
2022-09-22: Disclosed to Weather Factory by online form
2022-10-03: No response received, sent another email referencing our Vulnerability Disclosure Policy
2022-10-3: Response received confirming the vulnerability
2022-10-4: Last communication with the vendor
2022-12-13: Ghirbi the Gatekeeper mod released
Detailed analysis
The MODDING_README.txt file inside Cultist Simulator’s files states what is required for a mod to successfully work within the game.
At the end of the file is a section titled “CUSTOM DLL LOADING (CURRENT EXPERIMENTAL, UNSTABLE, WINDOWS ONLY)” which states that it can load any DLL file in the modfolder/dll directory with some restrictions.
The mod system within the game will load all modfolder/dll files and run the method modfolder.Initialise() on game initialisation.
DLLs are expected to be for .NET; although it is possible that native code could work if it conformed to the correct calling conventions.
A simple Proof of Concept was written which would spawn Windows calculator. The module was called TestMod. The DLL consisted of the following lines of code:
using System;
using System.Diagnostics;
public class TestMod
{
public static void Initialise()
{
System.Diagnostics.Process.Start("calc.exe");
}
}
This was compiled into a .DLL file and a very simple mod was added to the local mods folder in c:\users\username\appdata\LocalLow\Weather Factory\Cultist Simulator\mods\Testmod with the following files:

The synopsis.json file was the minimum required for the mod to be accepted:
{
"name": "TestMod",
"author": "Bob",
"version": "0.0.1",
"description": "Test exploit",
"description_long": "",
"tags": [ ]
}
The game was run and “The Invisible Serapeum” was selected in the main menu which allows controls over mods and the “upload” button selected. Which uploads the mod to the Steam Workshop.
This could be seen in my workshop and could be subscribed. Permissions were set for a private workshop item to prevent any accidental downloads.
Once this was subscribed the game was run and the mod was enabled in game. After this, whenever the game was started the PoC code was executed and Windows calculator was spawned.
Conclusion
The developers decided to fix the vulnerability by enabling the DLL load facility with another installed mod, called Ghirbi, the Gatekeeper. Although this does make it harder to exploit, it is suboptimal as several large mods require this to be installed and it would not be hard to just make this part of a malicious mod’s requirements.
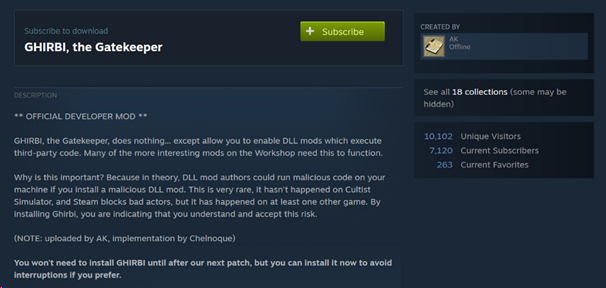
The developer’s statement for their patch warns of the potential for malicious interaction, but downplays the likelihood of it occurring implying a safety net from the Steam infrastructure. From previous experience, the Steam Workshop is not an effective security boundary and all mods should be treated as untrustworthy.
A similar exploit was found in the game Tales of Maj’Eyal showing that this could be a common problem with the Steam Workshop.
Overall, be wary of user-provided content that can be executable on gaming platforms, there are minimal protections in place from the platform meaning that all protections are in the games themselves which may have small development teams that do not have separate security functionalities.














