TL;DR
- Pillar 1 – Social media: Review your privacy settings, especially on social media. Limit what strangers can see, and think before you post. Screens, badges, emails, locations, and even your pet’s name can all be used against you.
- Pillar 2 – Account protection: Stop using weak, guessable passwords. Use long, unique passwords or passphrases that don’t include personal details. Store them in a password manager instead of reusing them across accounts. Turn on multi-factor authentication (MFA) anywhere it’s offered, especially for email, banking, work accounts, and your password manager.
- Pillar 3 – Phishing and social engineering: Watch for phishing, vishing (voice phishing), and smishing (SMS phishing). Urgency, pressure, unusual requests, unexpected login prompts, or payment demands are all red flags. Slow down and verify using known contact details.
- Pillar 4 – Software updates: Keep your devices, browsers, and apps updated. Patching your software closes known security holes that attackers actively use. Enable automatic updates and remove apps you don’t use.
Introduction
When it comes to being security aware, there are seemingly endless things you need to consider. Here are four key areas as a user you can focus on to keep yourself secure:
Pillar 1: Social media
Think before you post on social media
Even if you think you’re only sharing with friends and family, your posts may still be visible to malicious users. Weak privacy settings, or someone else’s public or compromised account, can expose personal details.
It can be surprising to the average user that posts as innocent as “back to school photos” may reveal information about you, such as where you attended your school and thus where you live. This sort of information can be used against security questions such as:
- What was the name of your elementary school?
- What is your mother’s maiden name?
- What was the name of your first pet?
Therefore, it is important to be careful about what you post and to spend some time reviewing your privacy settings so you don’t accidentally leak information to malicious actors.
Conducting a social media privacy review
For social media apps like Facebook for example, you can use the “View as” feature on your account page to see how random users can see your page and what you post to determine if your settings are secure.
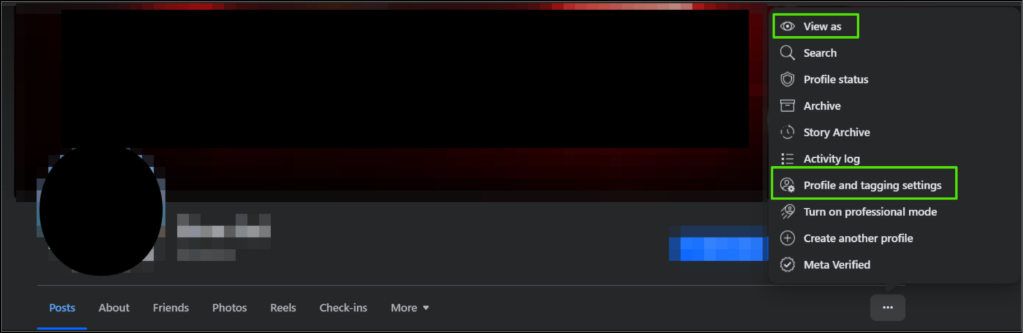
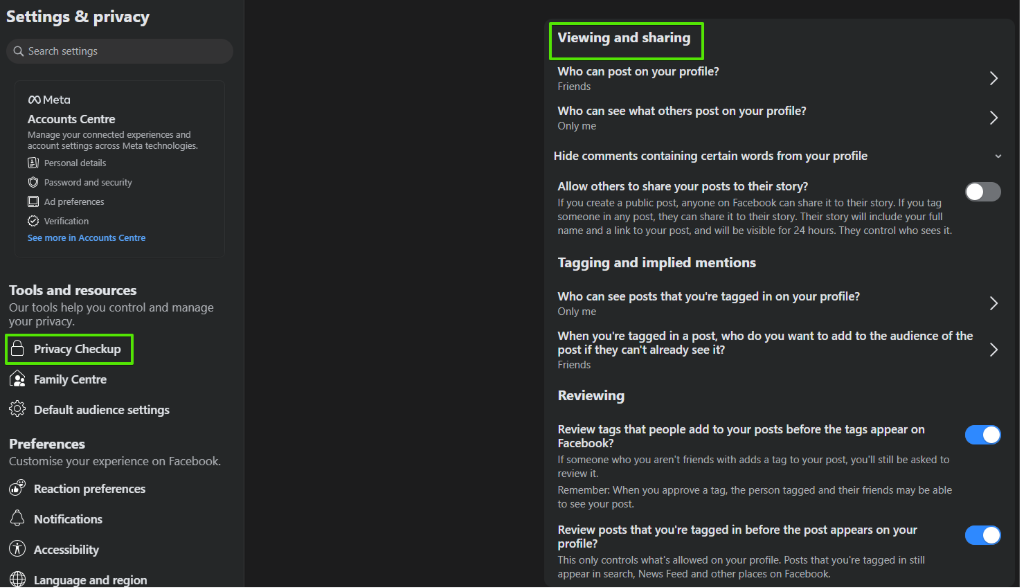
If you are unhappy with what people can see, you can edit the viewing and sharing settings under the same tab “Profile and tagging settings” and further settings can be changed under “Privacy Checkup”.
All social media platforms will have some form of “Privacy” setting to review who can view your profile and content and how it can be shared. For example, on Instagram under the profile “settings” cog, you can select “Settings and privacy”. Review these settings frequently, ideally once a year, to ensure they reflect any privacy changes.
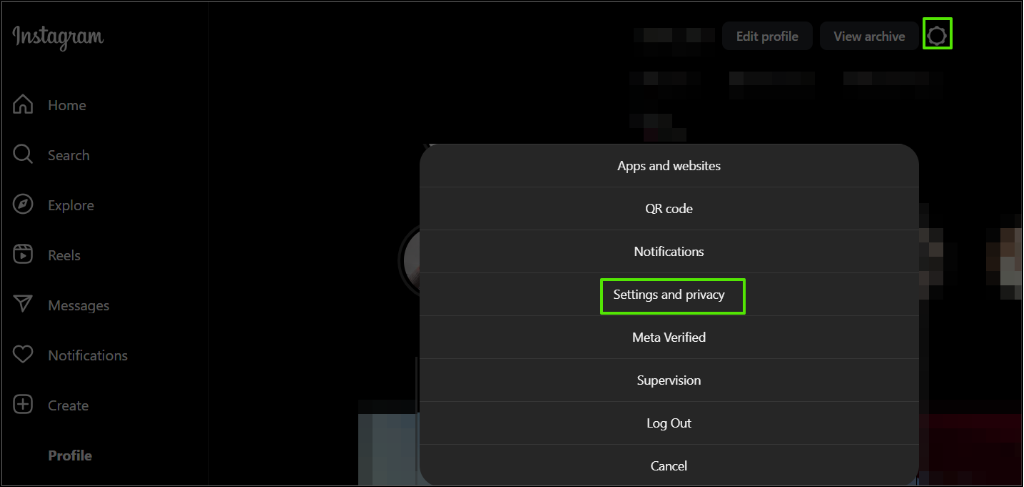
Under this setting many elements of the profile can be reviewed, including if the profile is public or private:
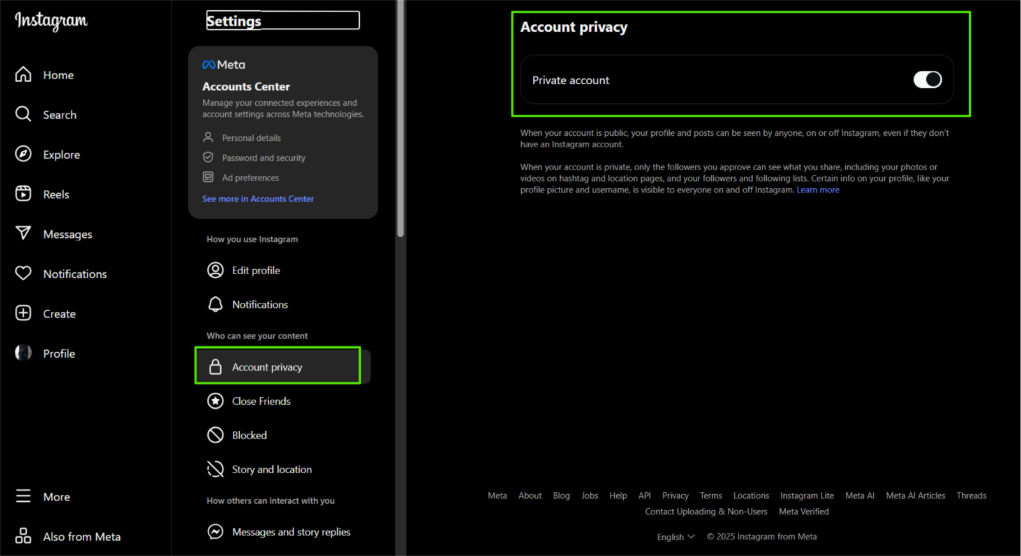
LinkedIn can be a hacker’s gold mine, if you let it
Networking sites like LinkedIn are often targeted because they contain valuable personal and business-related information, such as your work email or mobile number, that can be used to attack you and your business. Where security settings are required to be a little more “lax” for things like job hunting, review what is publicly facing. Ask yourself:
- Do all the people on LinkedIn need to know your work email address?
- Should your phone number be shared with so many people?
- Or can you share that directly with them as and when needed?
However, sometimes this information may also be inadvertently shared in a post or on social media publicly. Often with laptop screens, work documents or sticky notes in the background are clearly visible, aiding a malicious user to build a more believable backstory.
A few things should be considered when posting online, even following a privacy review:
- Does the post contain any sensitive information in the background? This can range from sticky notes containing information and employee badges to even a computer screen which may help identify the operating system or software in use.
- Avoid sharing personal information.
- Consider who you are sharing this content with.
Pillar 2: Account protection
Why your pet’s name is a bad password: the problem with predictability
Using predictable information like a pet’s name, birthdate, or street address makes your password easy for cybercriminals to guess or find online. Hackers use social engineering, automated bots, and brute-force attacks to test common passwords, dictionary words, and personal information. If your dog is named Bella, having a password like “Bella123” is extremely weak because it uses a common pet’s name combined with a simple number sequence, making it highly susceptible to a dictionary attack. This is made even easier if someone can find on a social media account a post of you and your dog tagged “Bella”.
It is important to avoid any personal information when setting passwords. This includes any football clubs you support, your partner’s name or anything else that can be discovered online or even by an innocent conversation with you. It is even more important to not set your work account passwords to anything related to the business name, business location or other easily guessable words.
There are numerous paths that may be taken to set strong passwords, a list has been previously posted in the Password policy guidance blog. But below I will explain how using a password manager tool can help.
Password managers
One method I recommend for keeping strong and unique passwords set for all your accounts is to use a password manager. It would be unreasonable to expect you to remember hundreds of long, complicated passwords, and if you do remember all your passwords, it is likely they are not that strong or similar and thus possibly insecure.
This eliminates the need to remember dozens of different passwords and prevents you from reusing the same one across multiple sites. Password managers can also fill in your login credentials automatically, which helps to protect you from phishing sites that mimic legitimate websites.
A password manager is an application that securely stores all your passwords behind one master password. Here is a typical layout once you login showing you all the different types of data you can store:
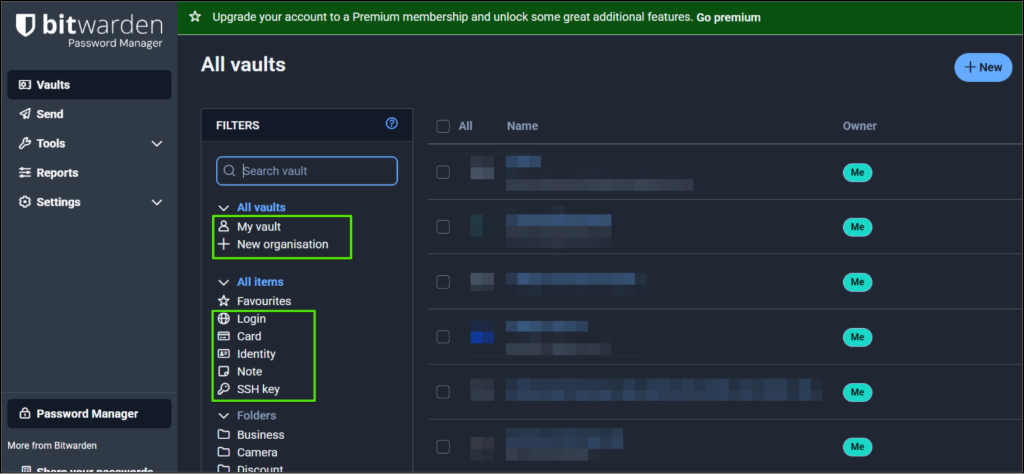
Often this is an app you can download from your Google or Apple store or access via the web. Some apps, like KeePass, are desktop apps. Password managers can securely store, manage, and generate long, unique, and complex passwords for all your online accounts. Often password managers let you choose between a password or passphrase. They are also often easily implemented into your phone to make it easier to paste or enter in your login details.
For example, bitwarden is an open-source password manager, here is an example of generating a passphrase and password:
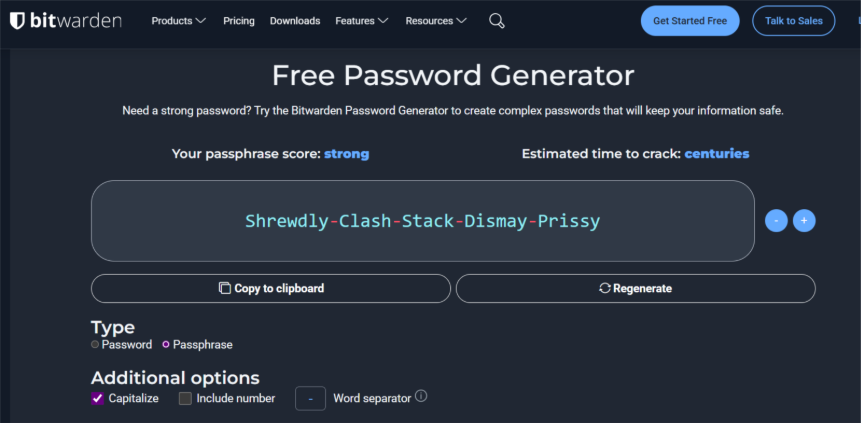
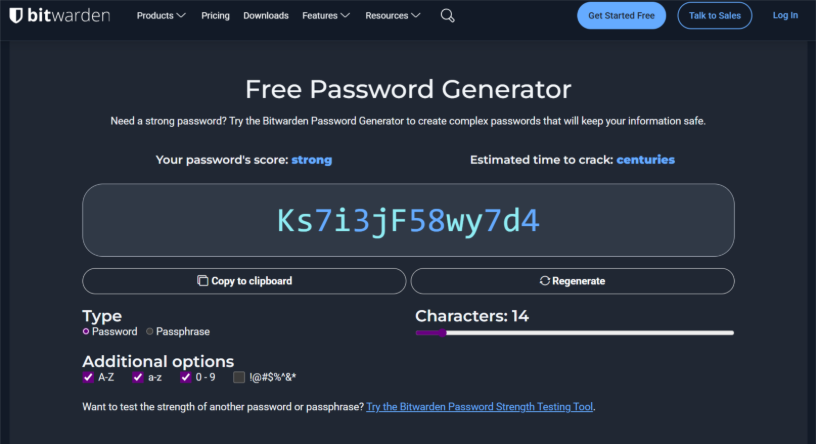
By not using weak passwords or the same password across multiple platforms, users eradicate numerous attack vectors. Firstly, passwords cannot easily be guessed by a hacker, but also if a website is compromised and your password is leaked, using the same password elsewhere would allow attackers to access that account. When passwords are leaked, they are often stored in a scrambled format called a hash. Hackers then try to “crack” these hashes by rapidly guessing millions of passwords against the hash. If your password is long and complex, it is much harder for them to crack the hash. Even so, if you are told a website you use has been breached, it is best to change your password straight away as a precaution.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security beyond just relying on a password. If your company uses Microsoft, then you are likely familiar with the MFA prompts when you log in, which can be frustrating, but it is effective at protecting your account. Even if an attacker Even if an attacker obtains your password, they cannot log in without the second factor, which significantly reduces the risk of automated attacks.
MFA is not always enabled by default, ensure where possible, that it is enabled in the settings. This feature is particularly important for sites where banking details are concerned or any sensitive information. Because of the sensitive data involved, password managers typically require MFA.
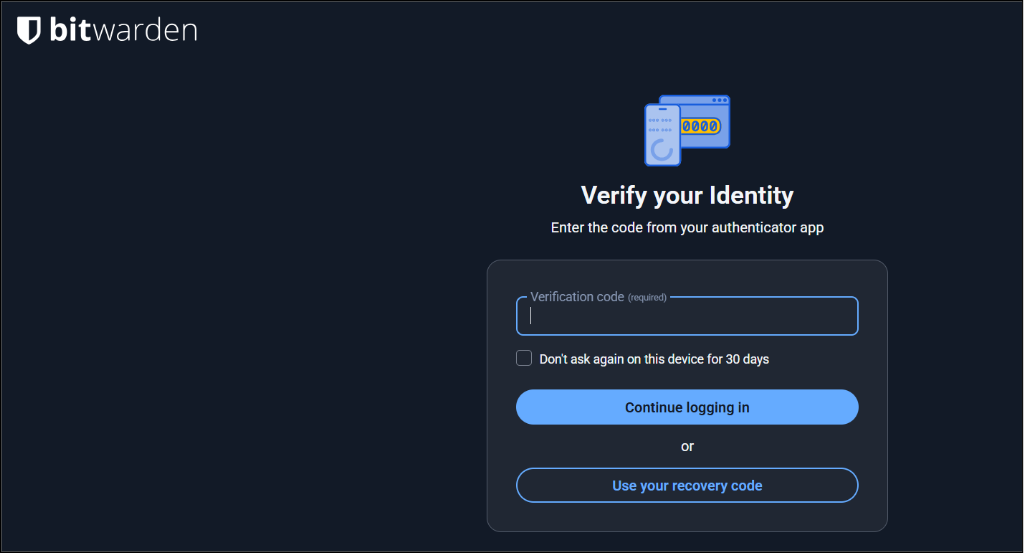
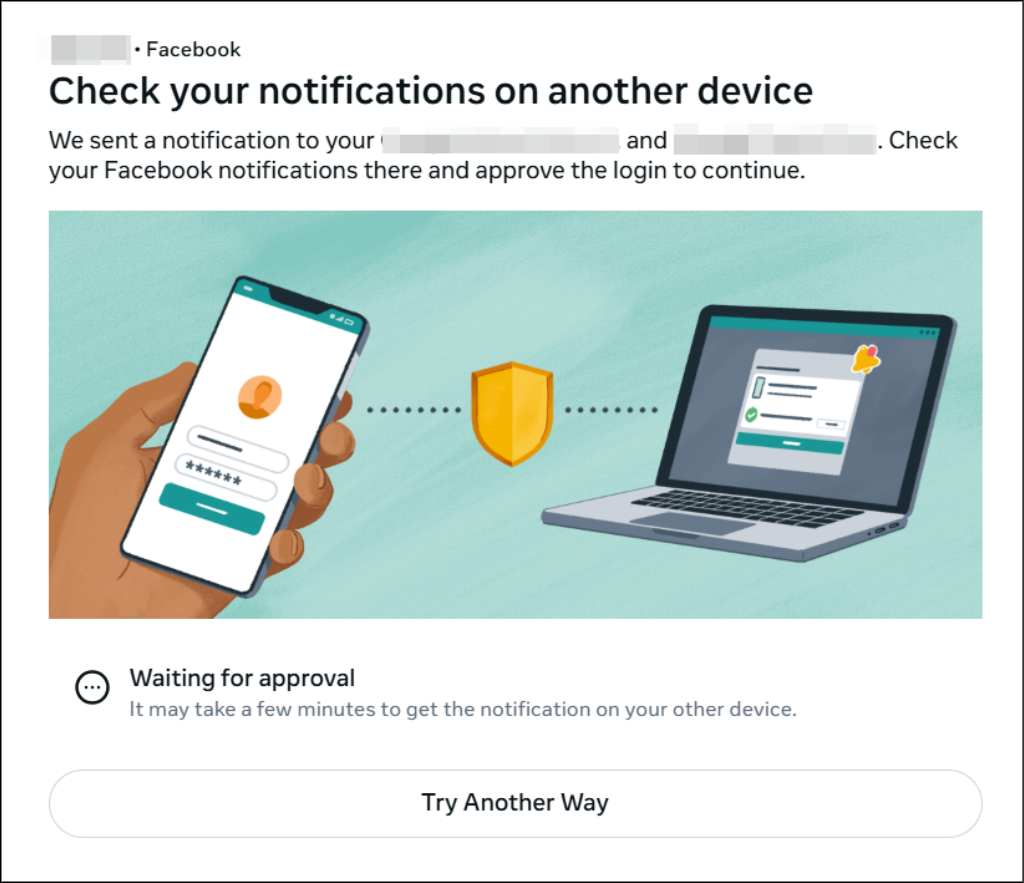
Other sites like Facebook use slightly different methods to provide MFA through a trusted device like your phone already logged in:
For some sites, such as Instagram, a mobile phone number is used as an MFA. However, ensure when logging into devices that are not your own to untick settings such as “Trust this device”, typically selected by default on social media apps:
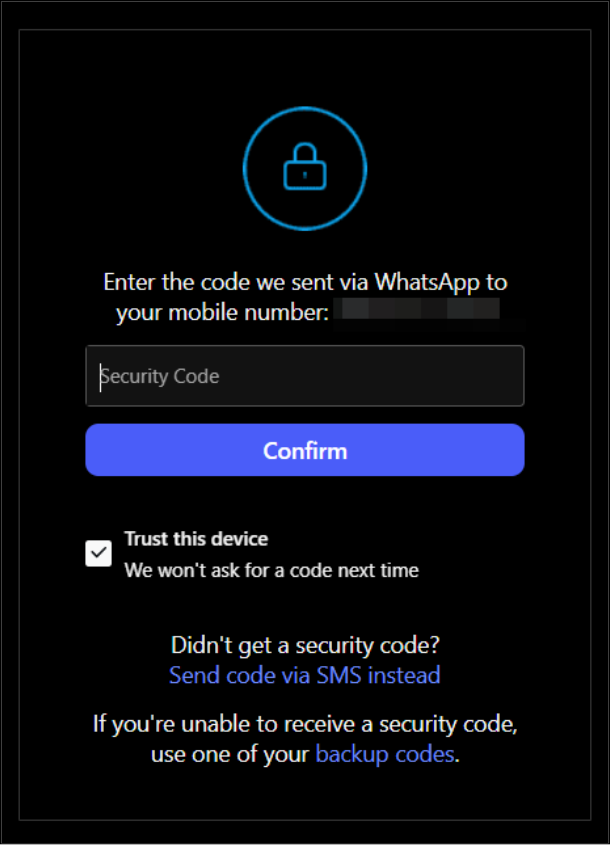
If you select this option, it will disable the MFA for this device for a certain duration.
Pillar 3: Phishing and social engineering
The human element of cybercrime
Social engineering is a type of cyberattack that manipulates people into giving up confidential information or money. Instead of targeting a system’s technical vulnerabilities, hackers exploit human psychology. Typically, these malicious users rely on publicly available information on platforms like Facebook, LinkedIn or company websites to create a believable scenario. Or other forms of reconnaissance.
Phishing
A phishing email might create a sense of urgency, fear, or excitement to trick you into clicking a malicious link or downloading an infected attachment. This could lead to a hacker gaining access to your accounts or network.
There are a few key signs users can look out for phishing:
- If there is a sense of urgency, be cautious, avoid clicking any links or QR codes. Open your browser and go directly to the official website to check for any issues.
- Are there any strange requests that you have already completed or would not typically be asked to do?
- If a phone number is provided, verify that it matches the contact details available online.
- Hackers can use AI to make their emails look more professional and less detectable.
Vishing / Smishing
Emails are also not the only form of attack. Hackers could also call you (also known as vishing) or text (known as smishing) impersonating your work’s service desk or other users or companies you may trust but not know personally. There are a few key signs users can look out for vishing:
- Similarly to phishing emails, vishing / smishing may also create a sense of urgency.
- Be aware of ID numbers, criminals can often spoof legitimate numbers to establish a sense of trust.
- Cyber criminals are typically out to get two or three things, your password, any form of MFA or financial information. Do not share any sensitive information you would not share with someone online.
All forms of social engineering aim to catch you at an inconvenient time or play on your emotions to assist them with providing information you may otherwise not provide. If you are unsure, it is safer to not provide the information and seek help from trusted sources and information you have gathered yourself.
Pillar 4: Software updates
Do not let your device become a gateway for hackers
Websites, apps or software can be compromised by other means, eliminating the password brute force route. Software and applications can have security gaps, or vulnerabilities, that hackers can exploit to gain unauthorised access.
Primarily, it is important that software is downloaded from a trusted developer or vendor. Downloading applications from untrusted sources could potentially expose your device to malicious code.
Software developers regularly release updates to fix any vulnerabilities and add new security features. By ignoring these updates, users can possibly leave these “gateways” open for cybercriminals.
Keeping operating systems, browsers, and applications updated is a fundamental step in protecting personal information and devices from malware and other threats. With so many apps on your phones or laptops, it is recommended to enable automatic updates in the app store on your device.
Apps that are not often used or require you to select to be updated are often left outdated. Browsers often have new updates which can be checked simply and usually by clicking the “Help” button under the three lines or dots indicating settings.
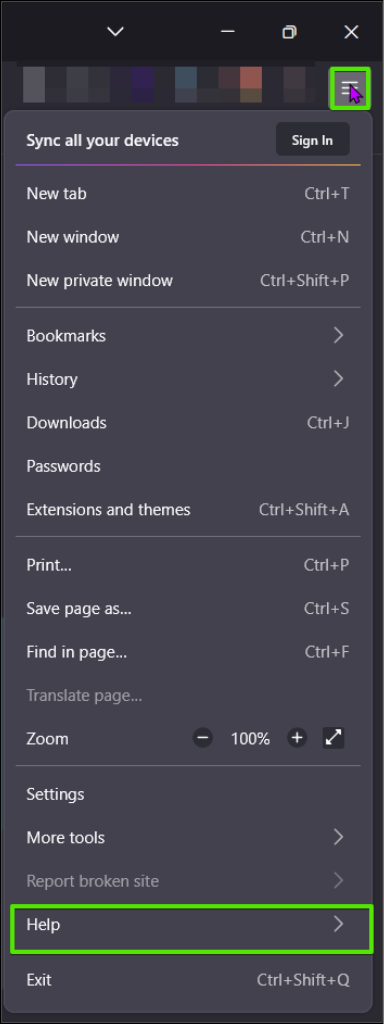
Within the settings, click “Help” and then “About”.
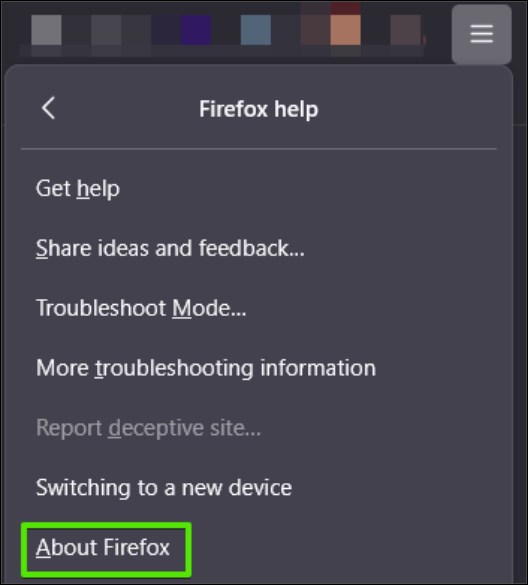
This should trigger a pop-up window that checks for any updates.

Similar steps can be taken for Microsoft Edge with the “…” –> “Help and Feedback” –> “About Microsoft Edge”
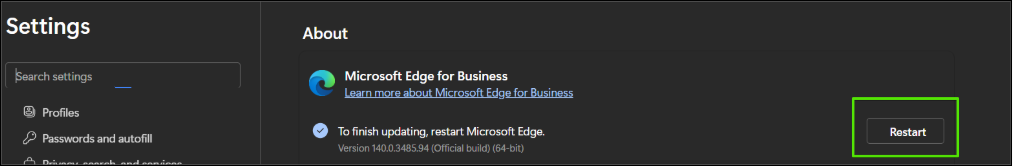
Applications often require a restart to apply any changes, like in the example above.
Common desktop applications such as Acrobat Reader can be checked for updates in a similar manner: “Help” -> “Check for updates”.
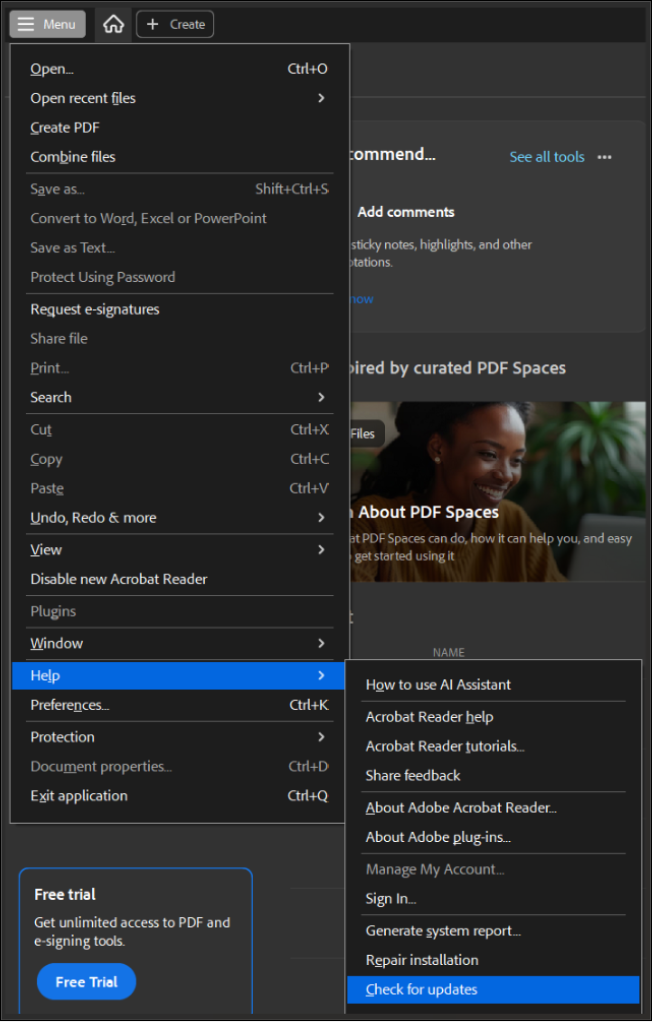
Conclusion
In summary, there are several steps users can take to keep themselves more secure online. Firstly, by ensuring their passwords are strong and unique across platforms, typically through the use of a password manager. Secondly, by enforcing multi-factor authentication incase the password is compromised. It is also important to be aware of social engineering attacks that may target these exact security features. Finally, it is important that devices, software and any apps are kept up to date to limit alternative exploit paths.














