Maybe second only to ransomware, the most likely type of attack a shipping operator will experience will be a phishing scam. Usually this will be carried out by email, or social media, or even messaging apps. It will likely include a link to what seems a plausible website, and/or have an attachment.
The quality of phishing attacks varies enormously. Doubtless you may have received an email from a bank that you don’t bank with. It’ll state that your account has been hacked or there’s been some admin foul-up, but whatever the ruse it’ll ask you take action:
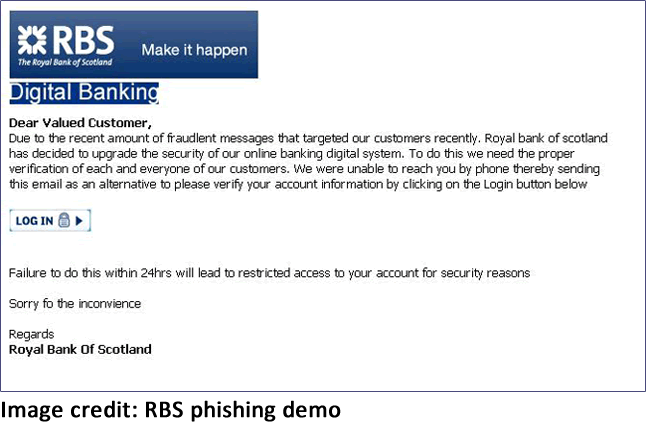
The attackers objective is to convince you to enter your banking credentials. Once they have those details they can then take full control of your bank account.
However, more and more we see carefully targeted attacks against management or board members. With these ‘whaling’ attacks the scammer will have done a some serious online (and sometimes telephone based) research on you and your organisation.
Bear in mind that scammers use ‘open source intelligence gathering’ or ‘OSINT’ (using social media and other resources) to build a picture of you and the people you work with. We published a real-world example for further reading.
Review your social media activity
I can’t stress enough that you should review your social media activity and settings. Are there any work related or office photos with your colleagues tagged in them? Are there any posts that mention suppliers/partners, or point to a connection?
There’s no real reason to make everything public, so consider locking your posts down to just friends/family.
Also scan through what your friends and family have posted about you, and consider what is appropriate about you to be available in the public domain. For example, are there photos of you at particular events, where a scammer could say they’d met you?
Consider the following attack:
Scammer notes from your online profile that you work for business X.
Using business social media networks such as LinkedIn, they search for all of the employees of the business you work with. Going further, they look at how your business interacts with its suppliers, as I’m sure some of your finance department are linked to other companies finance teams.
Even looking at your website and your suppliers can be revealing, particularly if one announces a large contract involving the other.
An email arrives to your accounts payable department, stating that the suppliers bank details have changed. The logo is correct, the name of the individual making the request is one you recognise. Bank details are changed for the next payment run to the supplier.
Except is was a scam and the money has now disappeared.
Transaction values in shipping are often significant. What if that was a bunkering payment? It happens all too often.
Many operators have improved finance processes to include validation of changes to bank details. Have you verified yours?
CEO fraud/Whaling
Social media will often reveal the organisational structure; who reports to who. Another common trick is to find the social media profile of a CEO, CFO or senior head in finance. The scammer waits until they post that they are going on holiday or boarding a long flight.
At that point, an email arrives in someone’s inbox in the finance team, coming from the CFO or CEO.
It’s usually quite threatening, stating that someone’s job will be on the line unless an urgent payment is made.
Attempts to validate the request fail because the CEO is on a long flight. So, the finance person is intimidated into making the payment.
Only when the CEO lands does the attack become obvious.
There are many different flavours of the same attack, some involving telephone calls to ‘warm up’ the finance person. What’s known as ‘social engineering’ is also employed by some scammers to sweet talk their victims into disclosing useful information.
Email attachments
Sending malware to a victim through email attachments is an effective way to compromise an organisation.
Emails are constructed, often made to appear as if they are being sent internally. One easy method is for the scammer to create a similar looking email address, often exploiting subtle differences between letters such as a ‘1’, ‘l’, ‘I’ to fool the reader in to thinking it’s a legitimate email.
Sometimes the email might appear to be sent to the reader by accident: an internal mail discussing salary change or redundancies with an attachment. How many readers would be inquisitive enough to have a quick look at the attachment before deleting it?
Anti-virus software can filter out simple malware, but it’s not very effective at blocking more advanced attacks.
Caution should be taken with email attachments, particularly those from external sources.
Extreme caution should be taken with ‘macro enabled’ Office documents. These have file extensions such as ‘.docm, .xlsm’ and similar. If you see the following alert, I strongly advise you do not open the attachment
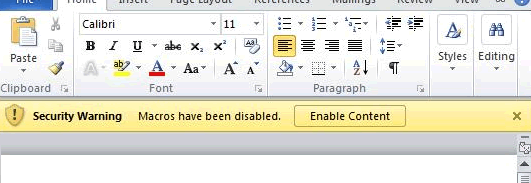
Zip files with passwords should also be treated with caution.
There’s a nice obvious labelling/warning system that your IT people can employ on corporate email to show users whether the email originated inside or outside the organisation, and so can indicate if it’s trustworthy or not. Full instructions here: Help users spot phishing. Tag fake “internal” emails for them.














