Introduction
The National Cyber Security Centre (NCSC) have advocated the use of three random words for several years to create strong passwords, and that advice has been repeated recently by the National Crime Agency, and multiple police forces in the UK…. but just how strong are these passwords?
Before we go there, we should acknowledge that most people have one or two weak passwords that they use on multiple sites & systems. One of those is breached, which results in other accounts being compromised through password stuffing. The NCSC advice is good in comparison to that low bar.
But we were surprised to see that password managers weren’t in the top 5 actions from NCSC. Here’s why they are so important:
The numbers
The English language has a huge number of words – the online Oxford English Dictionary has over 600,000 words however only around 171,000 are in current use. If we chose three random words from the words in current use, we’d have a search space of around 5,000 trillion. Yes, that is a lot, but modern GPUs are fast… really fast. One of our dedicated password crackers can search about 20 billion passwords every second from a disk-based wordlist (hashcat benchmark is about 185 GH/s). At that speed we could crack a three-word password in around 4 days.
The problem with this advice is that no one knows 171,000 words. Estimates for the number of words that a university-educated person knows is around 40,000 words, so we created a dictionary with the 66,000 most commonly-used words hoping that would cover most of the words that most people would tend to choose, and this reduced our search space by about 17 times allowing us to search all likely three word passwords in only 6 hours! Hmmm, it’s not looking good for ThreeRandomWords…
Official recommendation
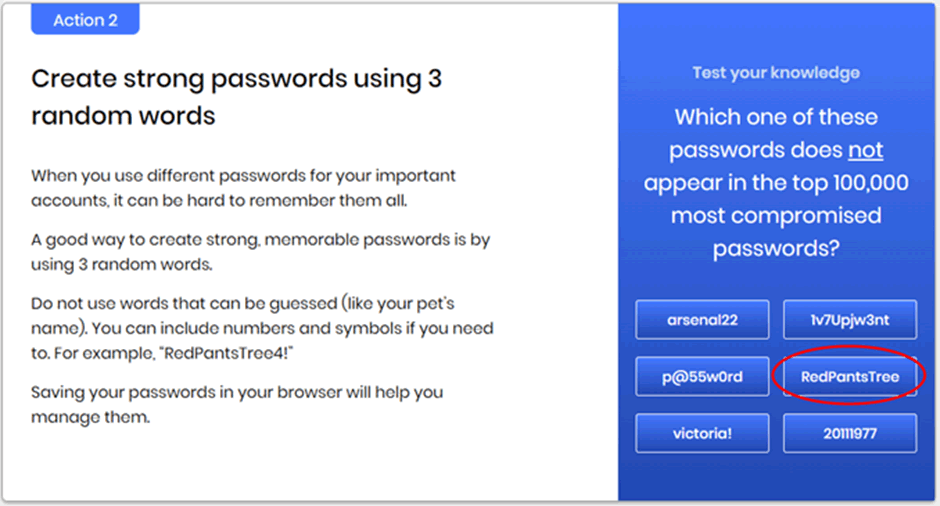
Source: https://www.ncsc.gov.uk/cyberaware/home
We took an interest in the example password of “RedPantsTree” given on the NCSC site. All of these words are easily in the top 30,000 most common words, but we decided to attack it with our big dictionary to simulate a more realistic attack time. We also added in the NTLM hash for “SuperfluousExonerateSerendipity” to show that even choosing less commonly thought of words is still an issue.
The NCSC password was cracked in about 4 hours, with the whole search space, including our uncommon three-word password, completed in around 6.5 hours.
MMMSession..........: papa_WWW Status...........: Running Hash.Name........: NTLM Hash.Target......: /home/papa/threerandomwords.ntlm Time.Started.....: Wed Jan 6 12:28:06 2021 (4 hours, 8 mins) Time.Estimated...: Wed Jan 6 19:15:33 2021 (2 hours, 38 mins) Guess.Base.......: File (/opt/dictionaries/papa/english-66k-upperupper.txt), Left Side Guess.Mod........: File (/opt/dictionaries/papa/english-66k-upper.txt), Right Side Recovered........: 0/3 (0.00%) Digests Progress.........: 272600599101440/427621521183219 (63.75%) Rejected.........: 0/272600599101440 (0.00%) Restore.Point....: 3616604160/5675964921 (63.72%) Candidates.#1....: OwainLawyersAugury -> OwenSuckedAvertir Candidates.#2....: OviedoClaudianLatex -> OwainLawyerLeahy Candidates.#3....: OverysselSightedPreviously -> OviedoClaudiaProclamations Candidates.#4....: OverworkInterrogationsWiry -> OverysselSightWo de947fd0bbd9f4f5c65a5d802cae1597:RedPantsTree . . f654100d842b2f6f68efeddcec2973bb:SuperfluousExonerateSerendipity
CorrectHorseBatteryStaple
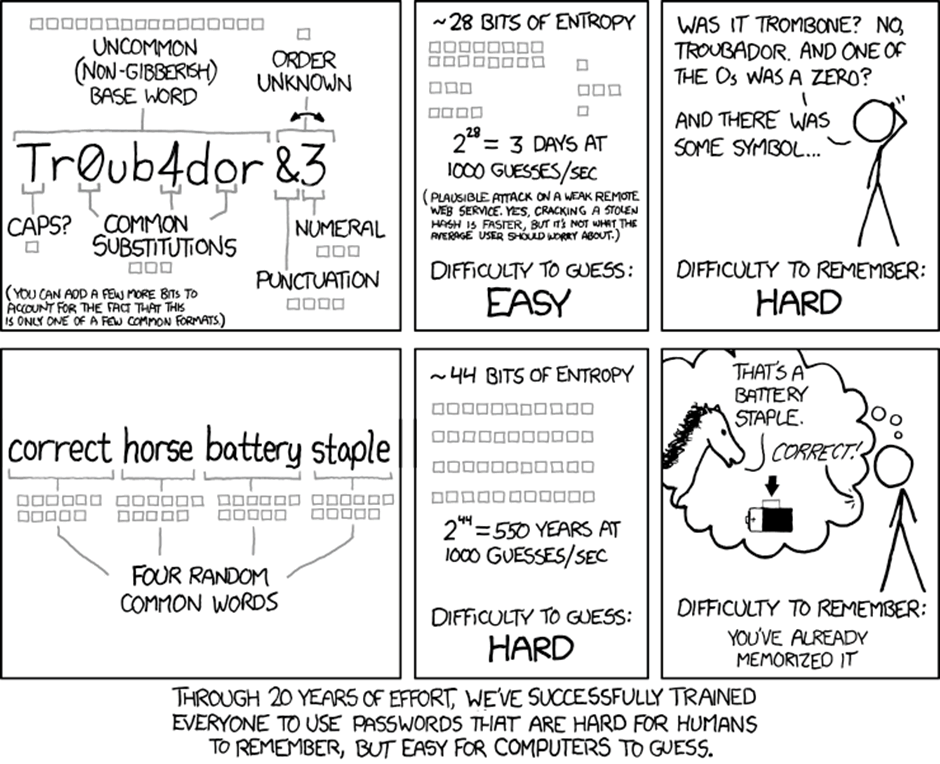
Source: https://xkcd.com/936/
What about using four words… does that work? Well, it does make things more difficult, but again it depends on how commonly used the words are, and how big the attackers dictionary is. The first three words of the xkcd example are really common and appear in the top 5,000 of every frequency list that I’ve seen. Staple is less common and is usually in position 18,000 to 20,000. So to actually crack that specific four word password encoded as an NTLM hash, would take about 5 months on one of our password cracking servers.
Cracking characteristics
Although it only takes about 6 hours to run through all of the three-word passwords, that is exclusively for words with an uppercase first character. If we want to crack all lowercase, that would be an extra 6 hours, add a “1” or a “!” at the end, and that’s an extra 6 hours. So, if an attacker compromised your Windows domain and everyone was using NCSC recommendations would it take forever to crack? Well, counterintuitively, it takes the same amount of time to crack 1,000 passwords as it takes to crack just 1, so if your NTLM hashes are compromised, within a couple of days, an attacker would have compromised most of your passwords. With the NCSC advice to also not expire passwords, cracking even a four-word password in 5 months could still be an issue.
What to do?
At Pen Test Partners, our IT team install a password manager by default on all managed devices. A password manager creates randomly-generated passwords that are super strong, and encrypts them for secure storage. I have no idea what 99% of my passwords are – they are all stored in my password manager, and it really doesn’t matter that I don’t know what they are. The password manager logs me into any system I need, quicker than I could type amonie and Password1!
For more sensitive systems, and anything that’s internet-facing, we also advise the use of Two-Factor Authentication (2FA). That means that even if your password is compromised, an attacker still can’t log in without your secondary authentication.
If you manage a Windows domain, we also recommend doing regular password audits. Our password auditing tool, Papa, now checks for three random word passwords in various formats and we spend several days of cracking time now, just on the three-word passwords.














