Aviation security is a complex environment. What first sparked my interest in avionics security was a comment from an airport customer of ours. They had seen the media coverage of the DHS work against a Boeing 757 a few years ago and were concerned that an ‘infected’ airplane might create a fresh attack surface for the airport.
When on the ground an aircraft’s communications with the airport and their company are prodigious, using Wi-Fi and other RF protocols to exchange data, notably Gatelink, but also simple crew laptops/tablets and phones in the briefing room.
The attack surface of an airport
Let’s look at some of the interfaces involved.
As a private pilot of many years I have personal experience of using a variety of these systems. I’ve been lucky enough to fly in to large commercial airports and mix it up with the ‘heavies’ in the same briefing rooms and security offices.
The biggest single challenge is the sheer volume of different entities that need access: passengers, crews, airline staff, security personnel, Police, Customs and other government agencies, freight, meal service and many more.
Access Control

A crew access pass needs to work at multiple locations, sometimes over different sites. Access control systems therefore need to be interoperable. It’s not much use if the access card only gets a pilot in to London Heathrow’s crew areas for example.
The demands of interoperability cause a few security challenges: it means that there are access pass issuing locations in remote airports with fewer security controls in place. It also causes ‘legacy drag’ as upgrading one system requires that all are upgraded at the same time.
So security controls often see a race to the bottom to ensure interoperability, mag stripe + PIN is still very common. Access passes need to operate across multiple airlines too, adding further complexity.
I don’t have an aircrew access pass to try and clone, but tools such as the Proxmark create possibilities. Maybe I need to buy the next commercial pilot I see a beer or three?
Building Management
Closely linked to access control is the building management system. Back in 2006 I noticed a press release from a BMS vendor announcing that they had won the contract to install building controllers at Heathrow’s then new Terminal 5.
So I bought an identical controller from eBay and got our team together to have a play with it. The results were a little scary.
BMS can control electronic door locks, HVAC, industrial process controllers and plenty more. Electronic door locks. Yes, those doors that keep airside separate from landside are usually electronically controlled. Hopefully alarms will go off if triggered, but we have discovered that some BMS have bypassable authentication and remote exploits. In most cases, they are behind access panels, but not always, and not always segregated on the network.
HVAC
Many airports go ‘long’ on windows, miles of glass in some places. This makes managing temperature challenging, requiring powerful air conditioning. Sometimes the HVAC is controlled with a locally-managed BMS, though remote management by a specialist firm is very common.
Let’s say that again, remote access in to the HVAC by a third party. Nothing has ever gone wrong there, right?
Interfering with the HVAC may only cause discomfort for passengers and staff as temperature goes awry, but it’s the connectivity to other systems that is likely to be of more concern.
Check-In Desks
Most desks are ‘rented’ from the airport by the airline. If you’ve ever looked at the screens the agents are using, you may see old-school green screen apps running in a window. These can be the airlines own system, or can be outsourced systems from organisations such as Galileo etc.
Given these check-in counters can be used by different staff from different airlines, how good do you think the user authentication is likely to be?
Self-check in kiosks also pose a risk as they’re publicly-accessible devices (although I imagine you’d get a swift tap on the shoulder from the airport police if you started unscrewing one) and again, are often multi-airline devices provided by the airport so they can be quickly repurposed as passenger demand varies.
Baggage
Want to see an airport in utter chaos? Go there when the baggage system has gone down.

Most baggage systems either have a degree of automation or are fully autonomous. They are controlled by industrial controllers such as PLCs, often managed by Windows systems.
Whilst the baggage system itself is rarely directly exposed on an airport network, usually residing on a dedicated serial network, interfaces to it are sometimes exposed.
Read our work on maritime serial networks if you want to see how much can be interfered with. Reflashing or bricking a few critical controllers or tampering with a small amount of serial data can be enough to snarl up a baggage system and bring the airport to a halt.
Flight Displays
I do love it when a client comes to us and says ‘make it as real as you can’. We carried out some red teaming for an airport and noticed that the flight displays appeared to have security issues.
We asked for permission to carry out a proof of concept, which the client agreed to. So we injected our very own flight:
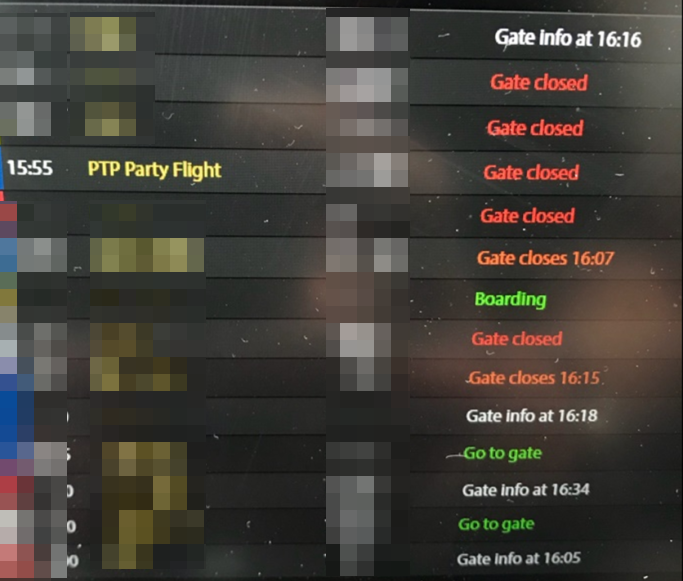
So what if the display boards go down or are tampered with? It happened fairly recently at Bristol Airport in the UK: a security incident, possibly ransomware, took out multiple systems including the flight displays.
The airport had to put significant numbers of additional staff out to replace the function of the displays. Not a security issue, but significant additional staffing costs were undoubtedly incurred.
CCTV
I won’t dwell on this as the security issues in CCTV are well documented. However, CCTV in some airports is amongst the finest in the world.
I have been awed by the resolution and low light capabilities of high end CCTV that we’ve been asked to look at by various airports. I was also impressed by high end CCTV hardware security, though that didn’t stop us recovering a private key from one ?
Airside Security
Electronic passport gates fascinate me. I was under the impression that they used biometrics to automatically verify the passenger. What I now know is that those scanned passport images are simply sent in near real time to a border guard who compares them with the camera image of the passenger. More efficient I guess, but not as ‘smart’ as I first thought.
We’ve seen insufficiently segregated passport gates on the network at airports before, such that law enforcement systems are visible from the corporate network. That would be a strong ‘win’ for security to sort out that segregation!
Security scanning / x-ray machines are also networked in many cases. We really want to have a look at these, together with substance detectors, but recent models are simply too expensive for researchers like us to purchase.
Airside Concessions / Duty Free

As with check-in desks, concession spaces are rented from the airport. Each concession will be provided with dedicated, isolated network connectivity from which to run their retail operations.
We’ve found some that were not segregated. Access to wider airport systems was possible, perhaps to facilitate interaction of the concession with other parts of the airport.
Wi-Fi
The issues with Wi-Fi are well known, though an airport can present interesting challenges. Electronic Flight Bags and other legitimate aviation devices can accidentally be connected to the wrong network if not carefully managed.
Spoofing a network to try to attract some interesting kit or credentials is sometimes successful given the large number of devices connecting to them.
Airside Systems
Ground power is essential for airport operations otherwise, airplanes would be left running their APU, burning expensive Jet A1 fuel and pumping out CO2, if on the ground for extended periods.
Guess what: the control and billing systems for ground power are networked.
Fuel delivery is arguably less networked, with most delivery carried out by a fuelling operator to the required load.

However, as evidenced by a lightning strike to the fuel depot at Stansted airport, knocking out high pressure pipeline pumps can cause trouble, so back to your OT hacking skills you go.
It’s probably not that well known that due to the huge volumes of fuel airports get through, they have dedicated pipelines to refineries, there would be no way to tanker in enough to keep up with demand – an A380 can hold 320,000 litres of Jet A1, which is over 250 tonnes.
Further, fuel delivery requests are becoming increasingly automated. The pilots Electronic Flight Bag can be used to specify the fuel load required, which is sent through an API to a tablet carried by the fueller, having been reviewed back at the airline’s flight operations for weight and balance.
Airside Vehicles

An airport is a busy place. It’s important to keep vehicles away from taxiing planes.
As a result, airside vehicles will be equipped with ADS-B at some airports. This means that they will show up on ground radar and help controllers keep everything safe.
ADS-B is an unencrypted and unauthenticated protocol. I’ve seen it fitted to some high end drones for conspicuity for legitimate, authorised use near airports.
It wouldn’t take much to broadcast a rogue ADS-B signal with an SDR and place a phantom vehicle on a runway. In low visibility conditions, this would cause chaos.
Pushback Tugs
Most airplanes will require pushback from the gate, so a tug is called on. The dispatcher walks back with the tug, keeping the pilot informed and providing an additional look-out over and above the tug driver.
Robot tugs are being trialled in several airports, where the dispatcher drives the tug by remote control, removing the need for two ground personnel to be involved.

So far, we believe that the tugs use both Wi-Fi and custom RF over 868MHz for remote control, but we haven’t had access to one to investigate thoroughly yet.
Hijack of a tug could be very troublesome, perhaps pushing one airplane in to another.
Airside RF
Aircraft are less reliant on ground navigational systems nowadays. The legacy VOR, ADB & DME navaids are being removed and have been largely superseded by inertial reference and GPS, although many airways still route VOR to VOR.
Instrument Landing Systems or ILS are still widely used, though often augmented or cross checked with GPS. This is a broadcast signal from a ground station at the end of the runway.
It has been shown that it’s not particularly difficult to spoof ILS and present a rogue signal that misdirects an aircraft. In good weather conditions, that offset would be obvious, but much less so in low visibility. Hopefully there is where Galileo can help as it’s supposed to be more resilient to spoofing.
Docking System
Again, to reduce the need for manual direction of a taxying airplane with bats, automated docking systems are becoming increasingly common.

These use infrared lasers to work out the distance of the aircraft to the stop point, however the systems have to know the aircraft type to work correctly. You’d hope the flight crew would notice it had been changed from an A380 to an A320 though!
Briefing Systems

Pilot briefing systems are critical to the dispatching of an airplane. One needs load sheets, weather, routing, clearances and plenty more.
This is usually done on a Windows PC in the pilot briefing room. Multiple pilots from different airlines will use these systems, so security controls can be a challenge to implement.
No clearance = no flight. There are back-up systems in place, but they add time. At the worst, this may involve clearances being read out and acknowledged by radio, significantly increasing the time to dispatch an airplane.
Increasingly briefing data is sent to the Electronic Flight Bag, but the briefing room still plays a key part.
Gatelink
This is designed to reduce the manual paperwork requirements for any flight. Load sheets, passenger manifests and plenty more is sent to the airport and back to the plane once it’s on the ground
Most Gatelink systems use Wi-Fi, activated once the aircraft wheels touch the ground. The client on board probes for a wireless AP at the airport, authenticates securely (one hopes!) and can download passenger data to the airport.
Ground Wi-Fi is a great deal less expensive to use than satcom data or VHF ACARS messages. It’s also used for download of engine performance data and numerous other metrics that can help efficient operation of the airplane.
Runway Lighting

Thanks to @fabcontrols for reminding us of the security challenges of runway lighting.
Having done flight training at night, I can tell you just how important that lighting is! The lighting is typically controlled using OT devices, so the attack surface will be familiar to those with experience of, for example, utility networks.
However, lights or not, planes can still land – whilst visual approach aids (VASIs / PAPIs etc) are very useful, the plane has other precision approach aids and its own lights. Of more sinister concern is the potential to tamper with taxiway and apron/ramp lighting. Stop bar / claerance bar lighting, runway guard lights could be switched off. Taxi centreline lighting is also very useful guidance when arriving at an unfamiliar airport at night. Putting a heavy aircraft wheel onto soft grass through not having taxi lights to follow is going to cause problems.
Larger airports will also likely have some ICS connection to standby generators to continue to power lighting, and a battery backup to bridge the time before those generators can start up.
Conclusion
As you can see, an airport is a very complex environment, one that’s difficult to secure. What critical actions should airports start with?
No surprises here, but basic principles apply: segregation, least privilege and containment of systems that can’t easily be secured.
Read more about our Aviation Cyber Security Testing services here.














