The Ghost Rover is a ghost hunting tank. You control it with a mobile app.
We’ve looked at a toy spy tank before, it wasn’t great from a security point of view.
Let’s hope our ghost-hunting tank – which, at $200, cost almost 4 time as much as the spy tank – has considerable security improvements in place. We certainly don’t want any interference when using a tool like this in the field.

The tank itself is predominantly plastic, and feels quite light. The ghost stickers on the shell illustrate its intended functionality.
From the outside, it looks very similar to the spy tank we tested. It has very similar wheels and tracks, and the Wi-Fi SSID is printed on a label on the base:

So, first of all, let’s get this thing working under “normal” conditions. There’s a couple of ways to run this tank – “Network Mode” or “LAN Mode”. Let’s look at the instructions:
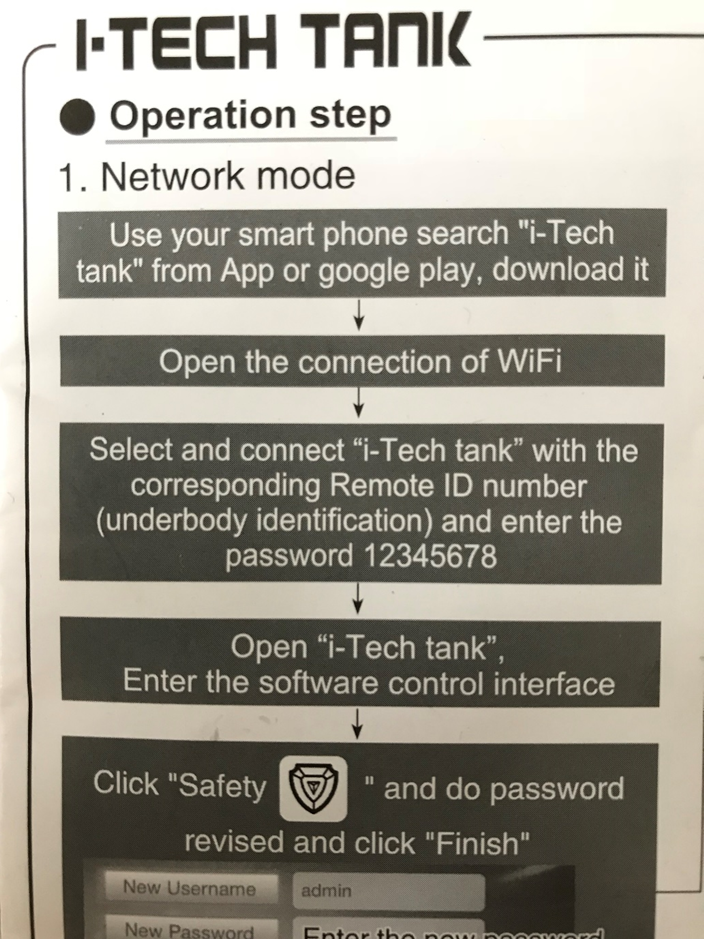
Firstly, the app. It’s on the Play Store, and is developed by Leo Lu.
Leo’s got a lot more, very similar apps on the Play Store! Including an app which looks very very similar to the one we tested in our last toy tank post…

It’s almost certain that this tank is made by the same company/person.
Also obvious from the setup manual – the tank Wi-Fi AP password is 12345678.
The Two Modes
Putting the tank into “Network mode” simply means that the tank is connected to a local home Wi-Fi network and the internal tank Wi-Fi is dropped. The app then tries to find the tank by sending a bunch of probe packets out to the local network to UDP port 6666.
The “LAN mode” means that the tank is controlled only while connected to the internal tank Wi-Fi. There does not appear to be a way to change the internal tank Wi-Fi AP password from the hard-coded 12345678.
As well as a Wi-Fi password, there’s also a tank-level password. This is to protect rogue forces from taking control of the tank. That’s the “Safety” step that’s recommended in the instructions. You’re not supposed to be able to get access to the tank unless you use the right password. However, even after the password’s been set, there doesn’t seem to be any check when resetting a new password.
As usual with things like this, it’s a massive pain to get it set up working normally.

Anyway, after some messing around, it worked. We can see stuff like our Boo Buddy, and the interface lets us drive the little thing around. It’s quite cool.

Once connected to the tank, either in Network or LAN modes, let’s see what TCP ports might be open.
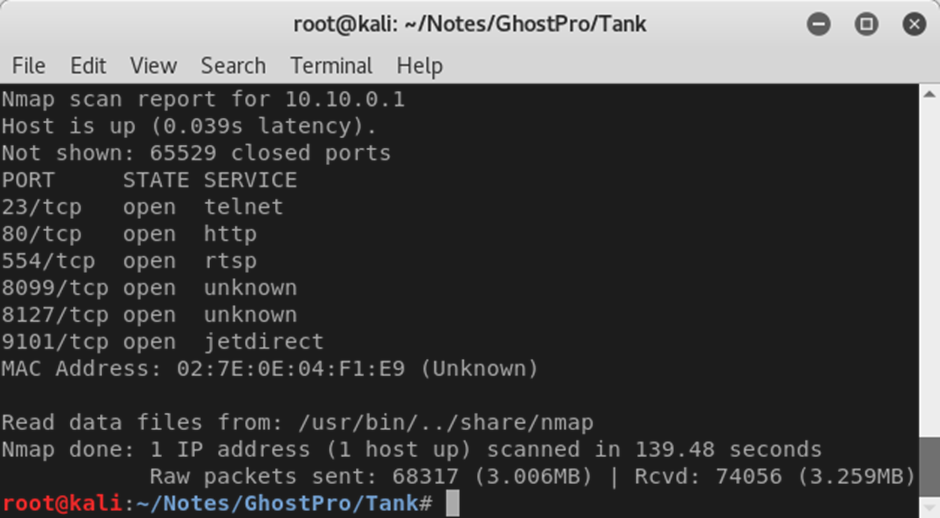
RTSP is open on port 554, as expected – this is a surveillance tank after all.
Sadly, from a security perspective, telnet is also open on port 23. We’ll come back to that later.
Not sure what’s on 8099 or 8127 – and it’s unlikely there’s any printer functionality via port 9101.
There’s also a web server running on port 80. Web servers can give a lot away about the underlying system on an IP camera like this. What’s on the there then?
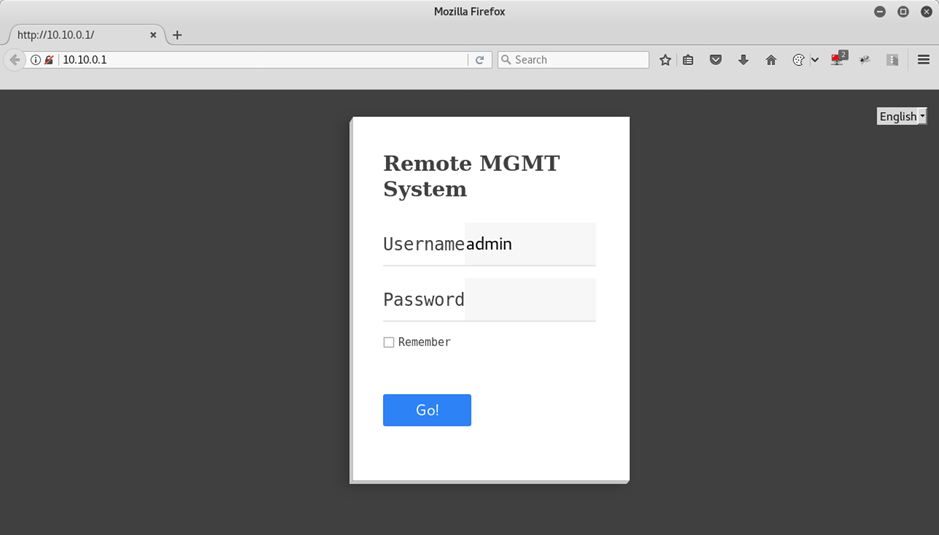
The username’s admin, and the password’s whatever the tank password has been set in the app. Luckily, the app doesn’t require any knowledge of the tank password to set a new password – once we’re connected to the tank with the app, either on the local network or directly to the tank AP, we can just set whatever password we want.
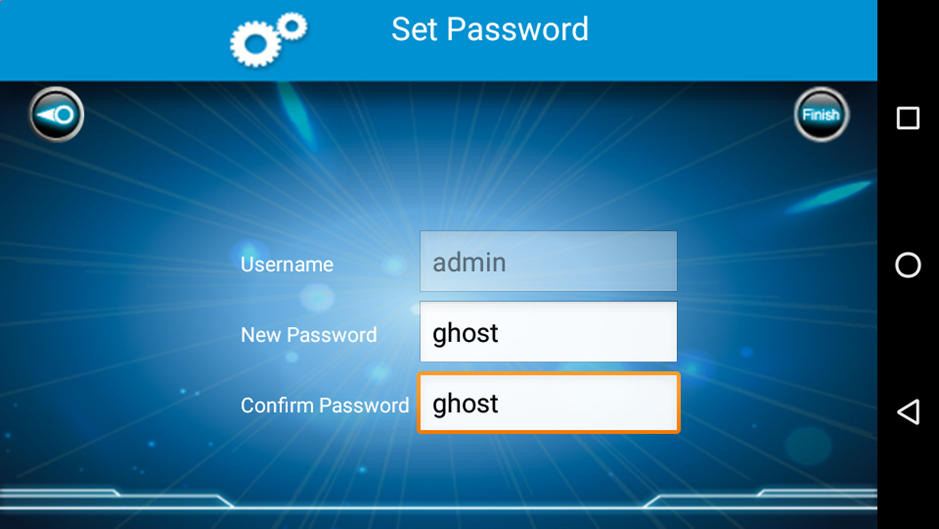
And, we’re in.
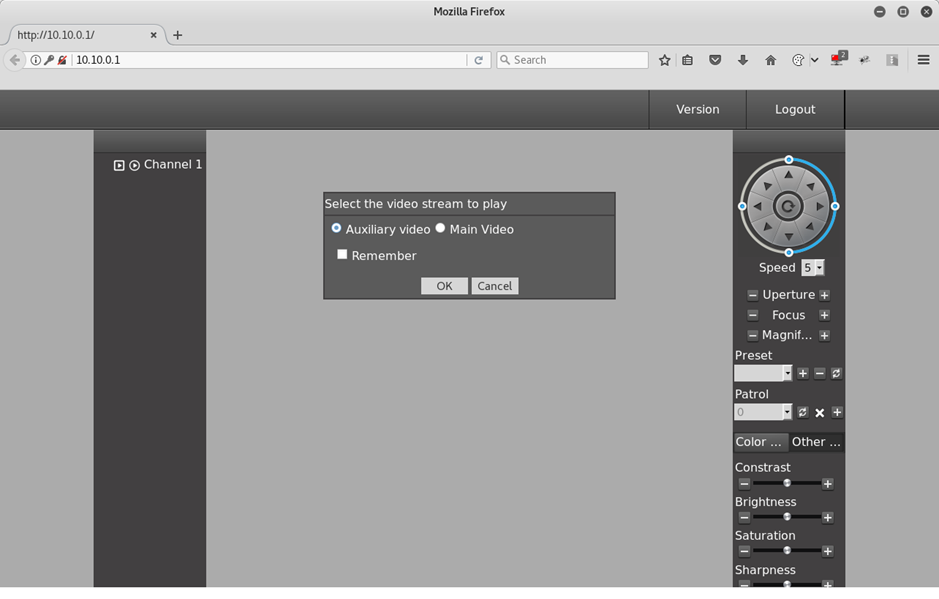
The web server’s a lot like most IP camera web interfaces. There’s a PTZ control, some image controls, and I’m still not going to download and install the plugin. There’s more important work to do. There’s ghosts to find.
So, what’s happening on this web server? It’s obvious by intercepting the traffic that all calls are made to a file in the cgi-bin folder called jvsweb.cgi. There’s a few interesting things about this – the most interesting of which is that the username and password parameters are sent, but appear to be totally ignored.
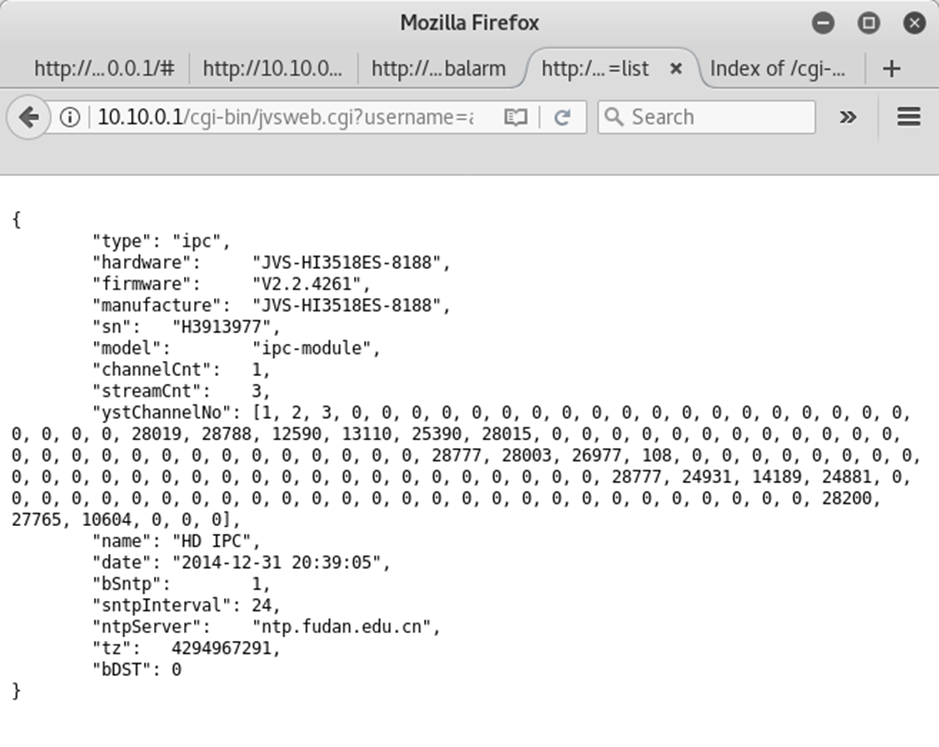
Result from an info request made to the the jvsweb.cgi endpoint.
By doing some light googling, the underling system is almost certainly some kind of Jovision IP camera. Looking up the jvsweb.cgi file turns up quite a lot of info and previous work done by others on these cameras.
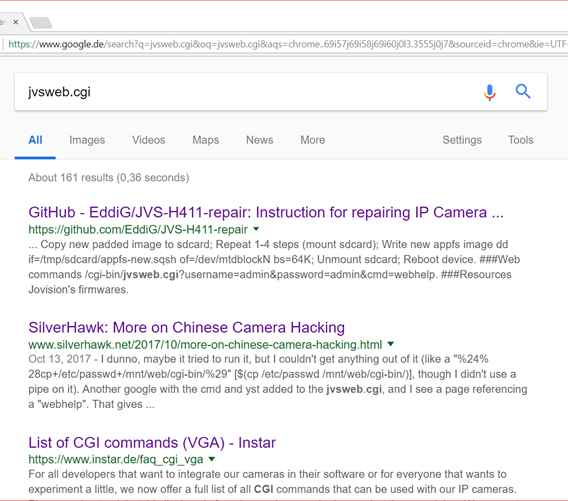
Some OSINT on the jvsweb.cgi file.
A bit of clicking around leads to a Russian language page, which notes a hardcoded root password – jvbzd. (https://habrahabr.ru/post/318572/)
Since we’ve got a telnet port open – let’s see if that works.
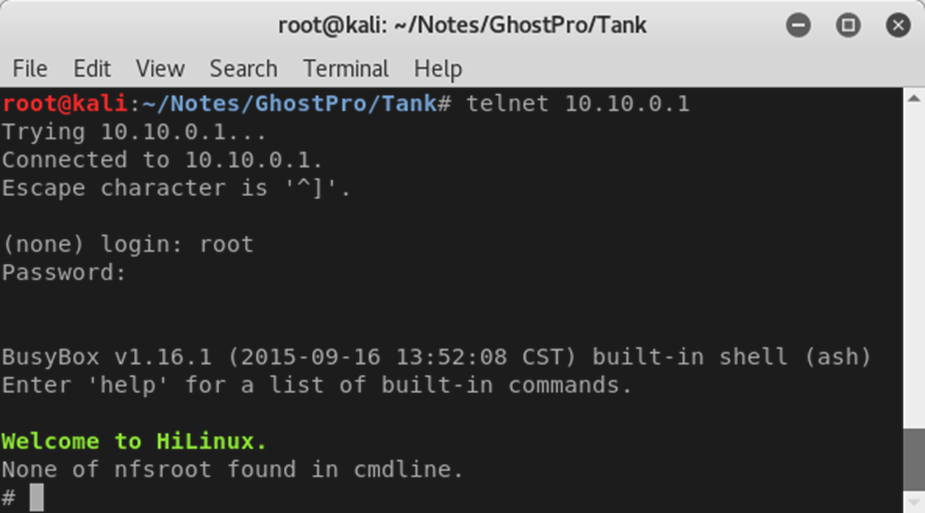
Too easy. Anyone who can get onto the tank – either through a user’s local network or connecting to the tank’s own Wi-Fi AP – can get a root shell on the tank itself.
Conclusion
The tank does very much what it says on the tin. It drives around, controlled by a mobile app and has an IR camera on it.
It’s almost certain that the IR functionality is introduced in the same way that it is on the Eken H9 “Ghost Pro” – by removal of the IR filter between the lens and sensor. In that way, at $200 it feels extremely expensive – considering you can get a normal tank for less than $80.
But – there’s some real nasty security issues on it.
- There’s a hard-coded password which gives root access to the underlying operating system. Over telnet. Any person with network-level access to the tank could cause some real disruption this way.
- The tank has a hard-coded password on it’s Wi-Fi AP – “12345678”. If you’re running the tank in LAN mode – remember that basically anyone can also connect.
- You can change the tank password to whatever you want, once you’re either on the tank AP or on the local Wi-Fi network. There’s basically no security preventing hostile takeover of the tank.
There’s also an introduction to Ghost Hardware plus a full review of ghost hunting device No.1 the Ghost Pro, and a review of ghost hunting device No.2, the Boo Buddy.














