FireWire Memory Attack: A how-to video
Hello, and welcome to the Security Kitchen. My name is Ken and today we’ll be looking at FireWire and a tool called Inception that’s used for getting around logins on locked machines. This something we demonstrated at Infosecurity Europe back in 2013.
The scenario was a personal Macintosh which had been stolen and we showed how to recover backed up data from it. This exploit we’re going to be running works on lots of different operating systems but today we’re running it on a Mac. To give Apple their due they have fixed the issue, which I’ll cover in a moment.
Inception is an awesome bit of gear that takes advantage of the FireWire port, you may well have one on an old laptop. As you can see I have a fairly old device here, with a FireWire port. It’s used for high speed file transfer and video streaming for example, it had really high throughput at the time. It’s largely been deprecated by Thunderbolt and USB3 though. Even if you don’t have a FireWire port remember that if you have a PC card port that will accept a PC card FireWire port, making this attack possible.
So, I have my victim machine here, and my attack machine here, connected together over the FireWire port. I’ve loaded Inception and you can see that it’s identified the device, we’ve got version 5 Mac OSX, and I’m going to start Inception up. It’s now going to go through the process of searching memory, the area of memory that is concerned with the logic of establishing whether a password entered on start up is true or false.
So I’ve got my locked machine here, it’ll take a little while, as you can see it is still locked. OK, now we’ve found the correct area in memory that deals with logic involving passwords and Inception has patched that. Here’s the magic bit. We go back to our Mac here, try to login, and it’s unlocked. Easy as that.
What can you do about this? This exploit works on Windows 7, I believe it works on Windows 8 as well. On a Mac the best thing to do is disable the FireWire drivers. On a PC the best thing to do is disable FireWire and PC card drivers too. On a Mac anything newer than Lion OSX 10.7.2 has been fixed. They disabled the Direct Memory Access (DMA) when the device is locked, so you can’t run this exploit any more.
Generally, on Windows at work you can enforce a group policy to remove the ability for machines to go to sleep. This commonly happens when the laptop screen is folded down, instead of simply locking it. Disable sleep mode because that writes the state of the laptop to memory which means of course that we can mess around with it. Its far better to use hibernate as this writes the state to disk. Although you are far better off powering down the laptop completely.
If you’ve got a locked machine that isn’t configured correctly I recommend not leaving it unattended, you might even want to consider taking it to the toilet with you.

How We Hacked Swann Cameras: Lessons for IoT Security

Hacking with Chromecast and Alexa

The Tapplock Bluetooth unlock attack

Z-Wave Z-Shave downgrade attack
A smart coffee machine

Disabling Wireless Alarms 1 – Simple Jamming
Disabling Wireless Alarms 3 – PIN Brute Force

Disabling Wireless Alarms 2 – Replay Attacks

Disabling Wireless Alarms 4 – Attacking A Brand New Alarm
Wireless Alarms – What To Look For In An Alarm

Hacking the Mitsubishi Outlander PHEV SUV

Android PIN Patterns: A how-to video

Exfiltrating data in ping packet padding: Video demo
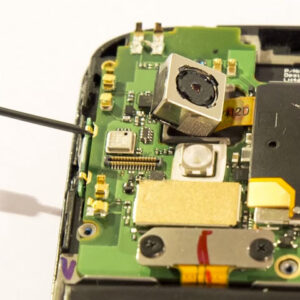
Scraping Memory From Android Phones With JTAG: A how-to video

How to bruteforce the PIN on Android: Nexus 4 video demo

iPhone PIN Cracking: A video demonstration

Hacking Android Through Accessibility Events: A how-to video

ADB PIN Crack

How to hack Tesco’s Android Hudl

Teensy USB Connect Back Hack Video

RFID Cloning With Proxmark
Bypassing Antivirus To Deliver Malware With Code Packers
Getting a divorce with iOS – Siri Bypass

iOS PIN Cracking Video
Keylogger Keyboard Hardware

Wireless Probe Snooping

Email Connect Back

















